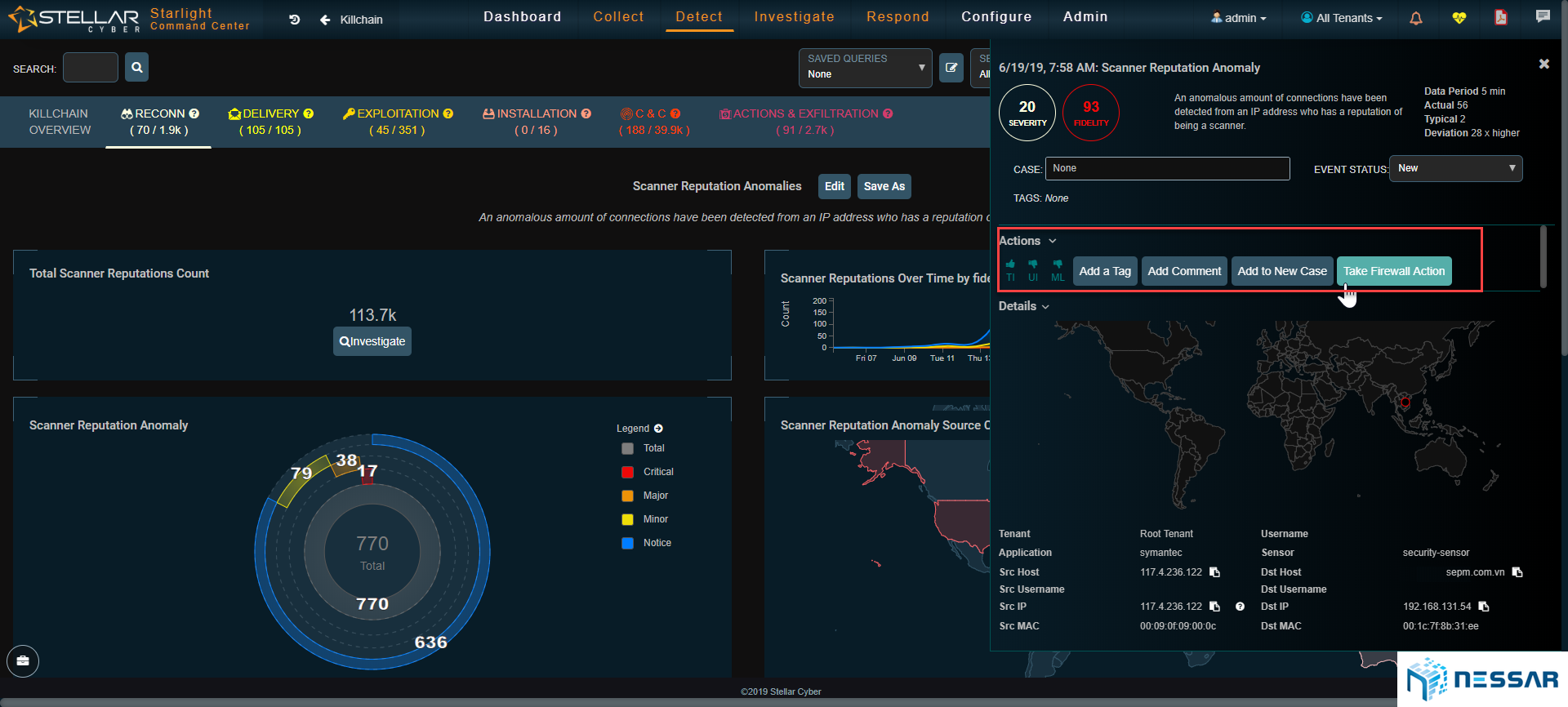
Advanced Threat Detections
Starlight leverages patent pending Distributed Security Intelligence™ technology to deliver massively scalable, pervasive breach detection. Using sophisticated correlation of enriched data and advanced artificial intelligence techniques, Starlight is able to detect breach events faster than humans and with higher fidelity. This unique approach helps companies reduce the time to detect a breach from an industry average 200 days down to mere minutes.
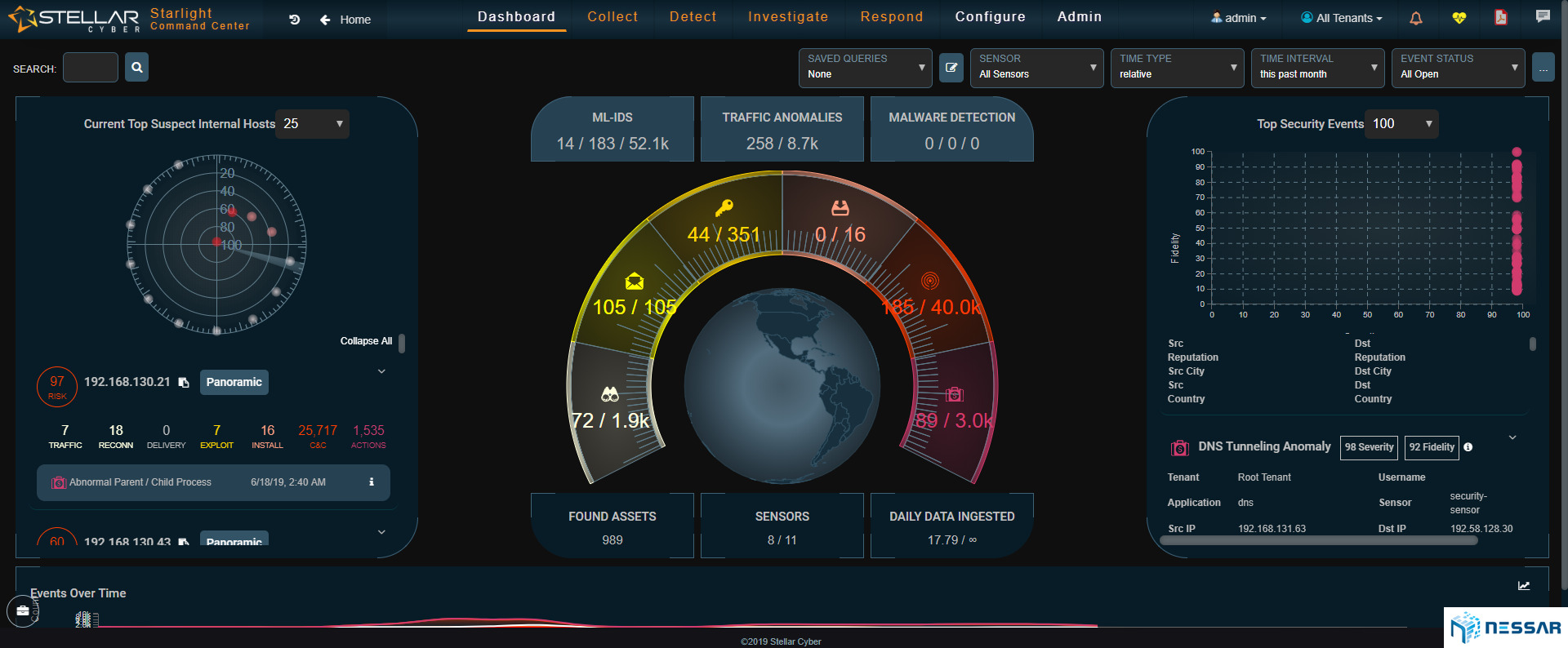
Starting with Advanced Threat Detections
Starlight’s dashboard provides an overview of the entire cybersecurity kill chain and is based on a defense-in depth security design.
From reconnaissance to exfiltration, suspicious communications to internal and external actors, Starlight gives real time visibility of threat progression as it happens.
Starlight studies each data point to remove the noise and show only high fidelity, scored attacks and anomalies. Admins do not need to deal with thousands of noisy alerts but only a handful, relevant events on their dashboard.
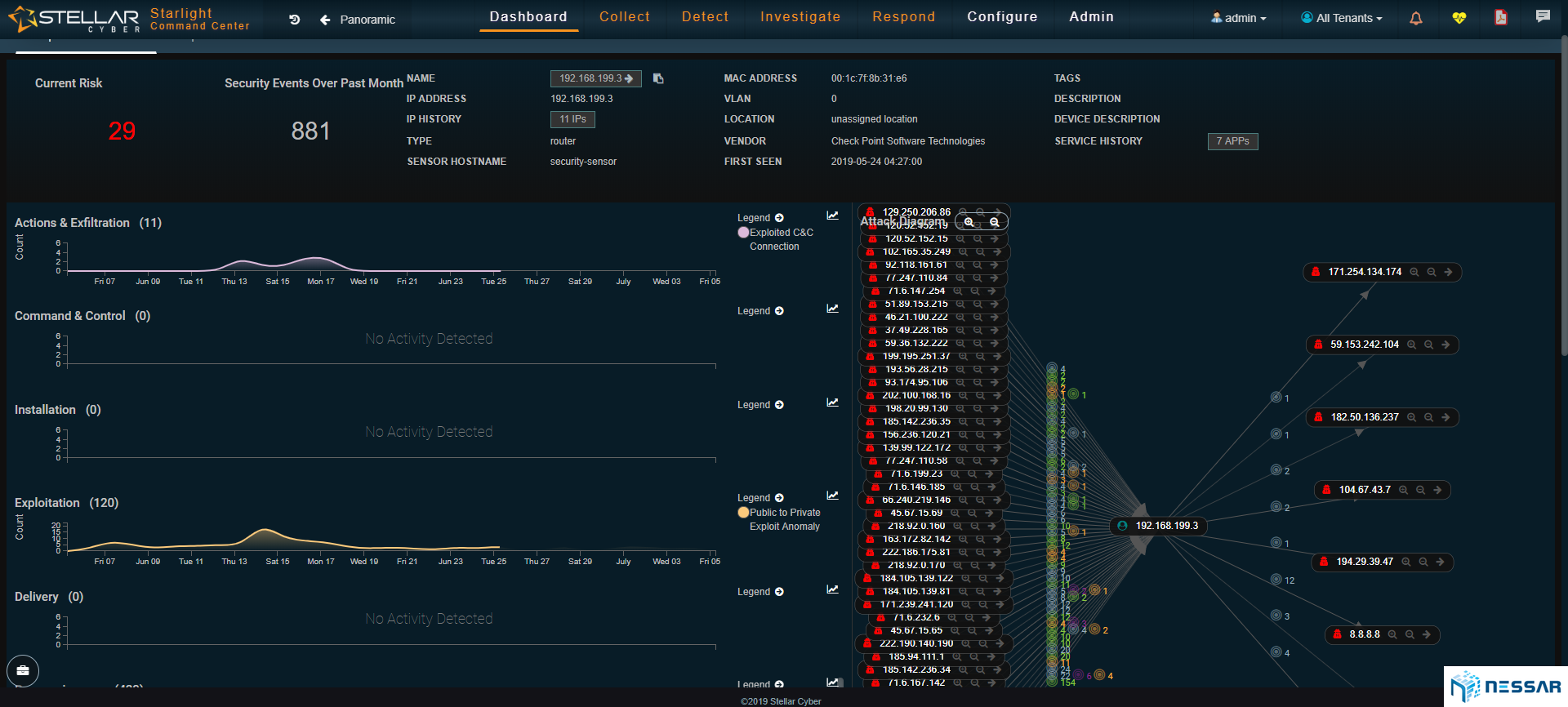
Panoramic View
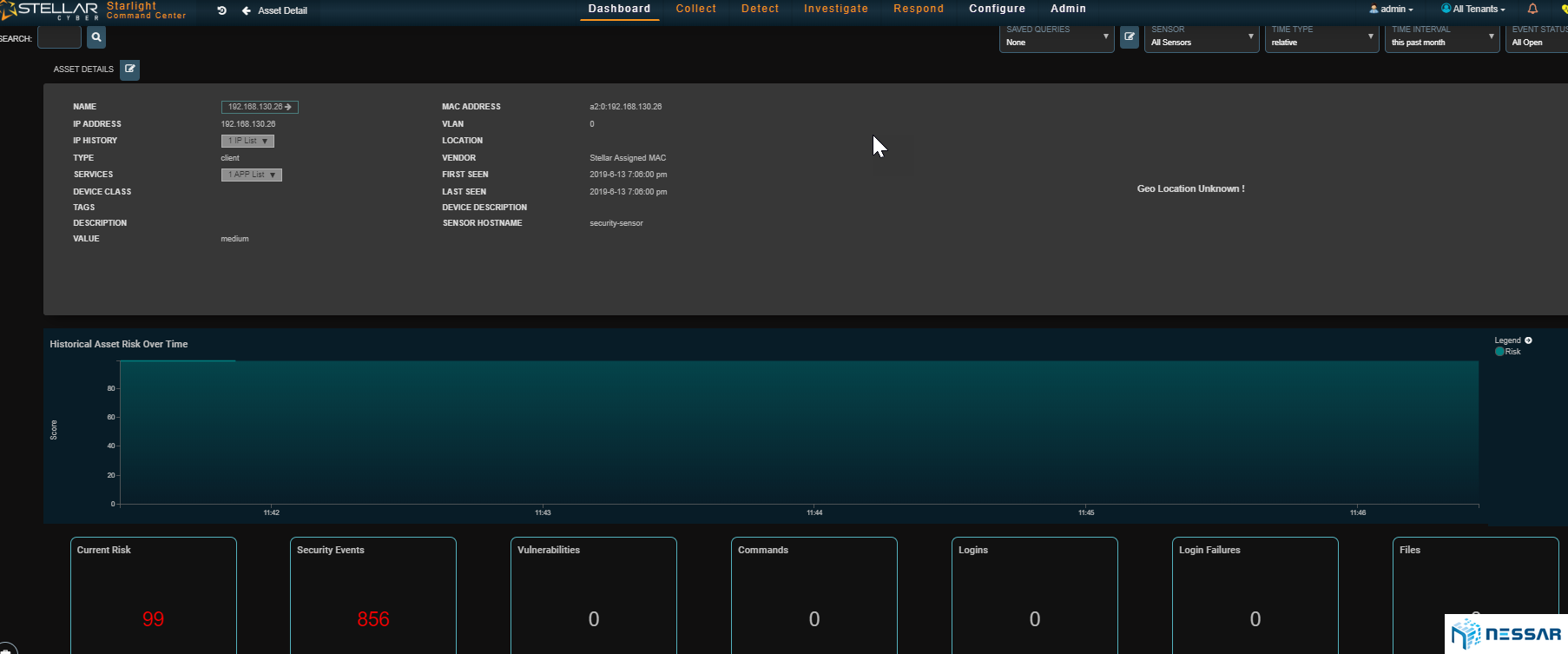
Starlight’s panoramic view provides high fidelity attack and anomaly visibility of compromised or targeted assets and external bad actors, and correlates data across the cybersecurity kill chain.
Admins can easily trace the attacks that have taken place on an asset and identify which bad actors have contributed to the compromise. Starlight also gives admins the ability to locate where bad actors are coming from. With the single click of a button an admin can drill down to see the details of security events and determine the reason of behind an event.
Starlight is the most open and easy to understand, so use, security analytics platform in the world with huge difference…
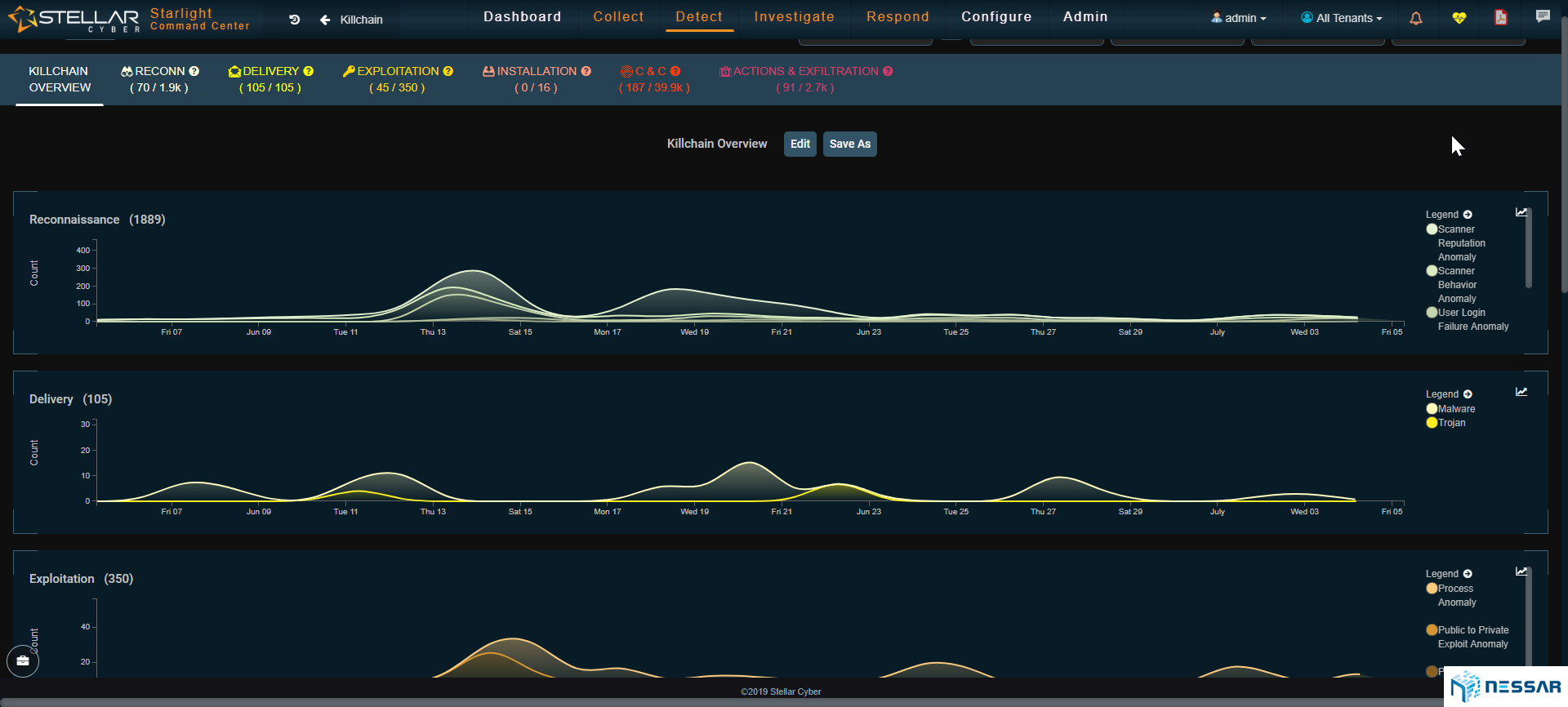
Advanced Threat Detection
Suspicious Communications
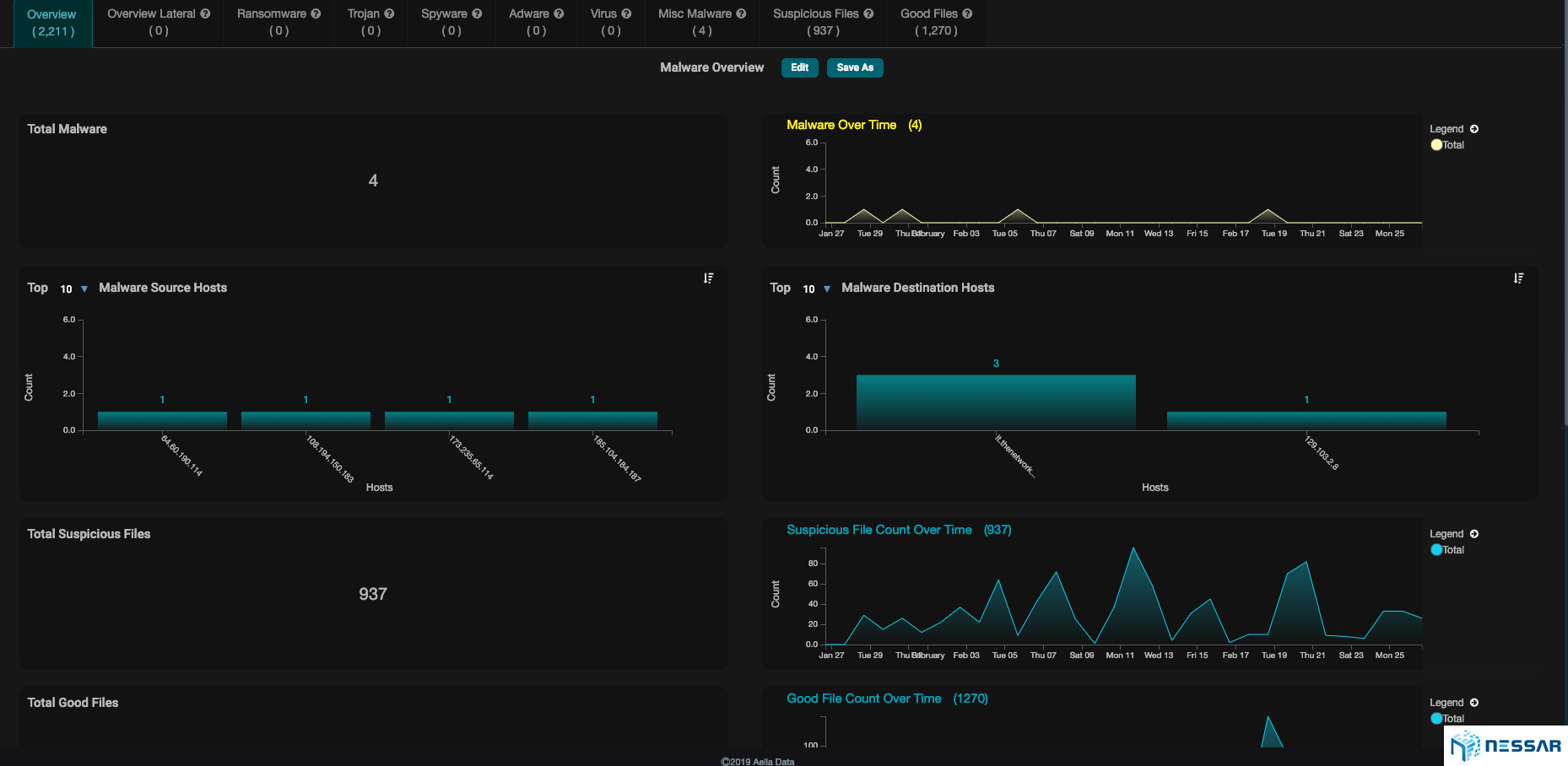
Starlight provides separate views for communications that are anomalies within the environment breaks the views down into relevant detection categories.
It includes a view where admins can find high fidelity firewall alerts thanks to its industry first and only ML-Firewall (TM) component. Stellar Cyber innovated machine learning on firewall data, to get rid of firewall log noise to provide a cleaner view of what is important and needs attention.
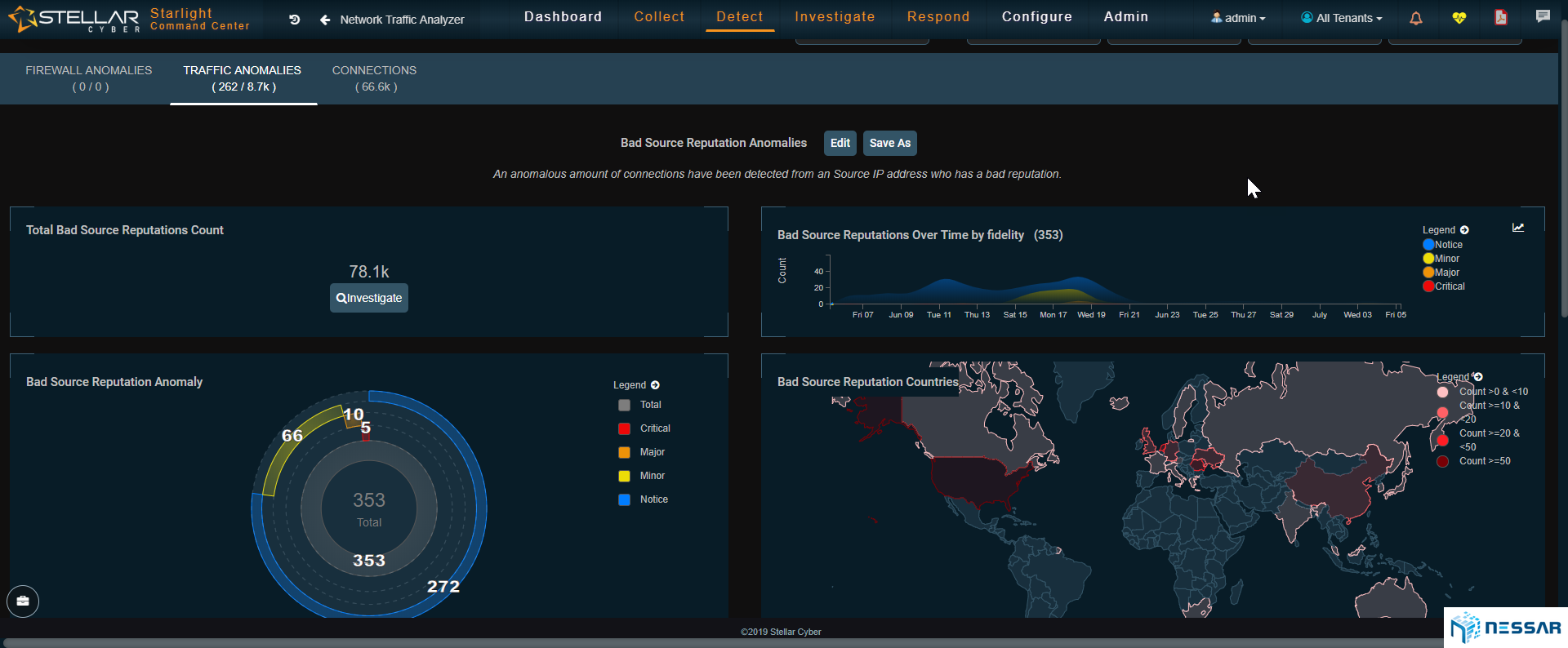
ML-IDS
Starlight innovated the machine learned IDS feature. ML-IDS is a new design when compared to traditional Intrusion Detection Systems.
By combining best of bread IDS technology with machine learning, Starlight dramatically improves the elimination of IDS noise and false positives.
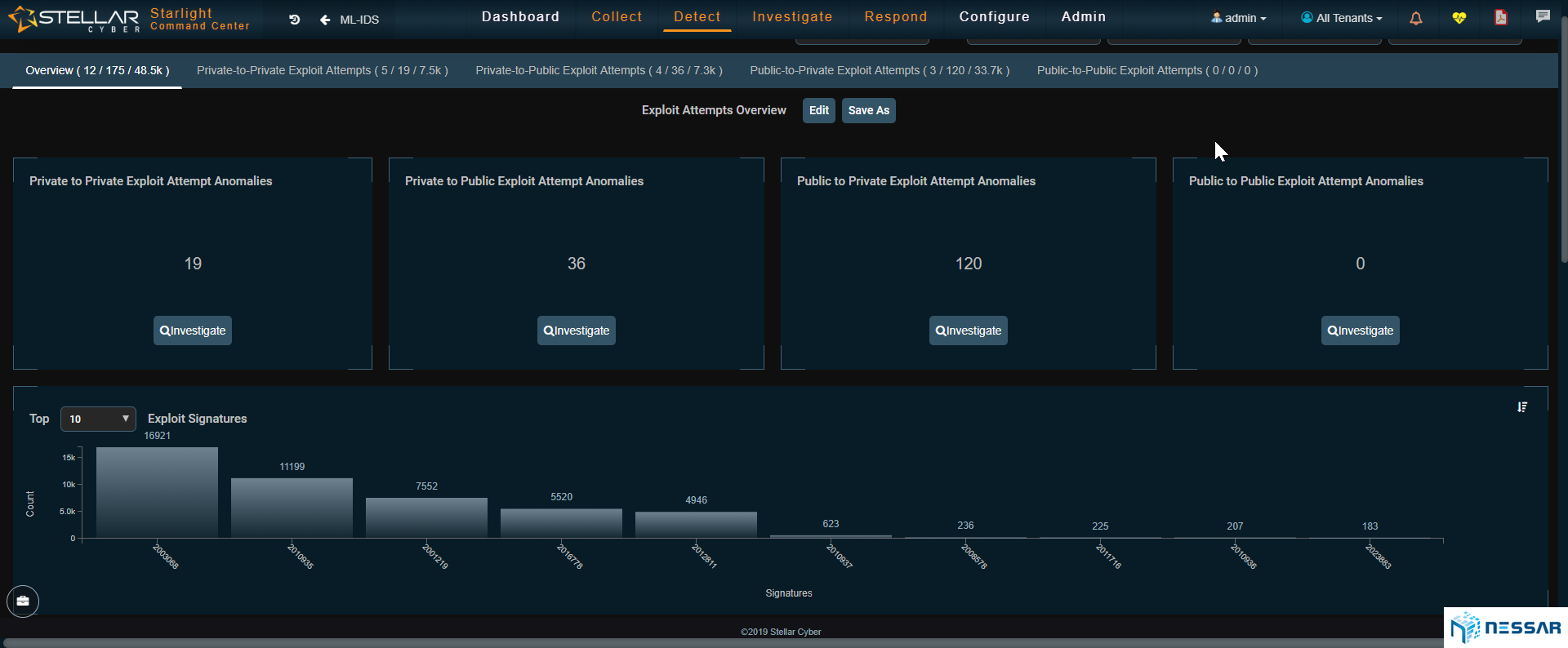
SIEM
Visualizer
Starlight provides incredible visualization capabilities for admins to leverage existing views, customize templates and create completely new dashboards from the complete set of data that platform offers as Interflow™.
Each dashboard, whether it is from an existing or customized template, the platforms dashboards to be turned into PDF reports. Admins can also schedule these reports to be automatically emailed.
This gives admins an ability to create an unlimited number of reports to satisfy any business needs and turn repetitive reporting tasks to one time configurations in a snap.
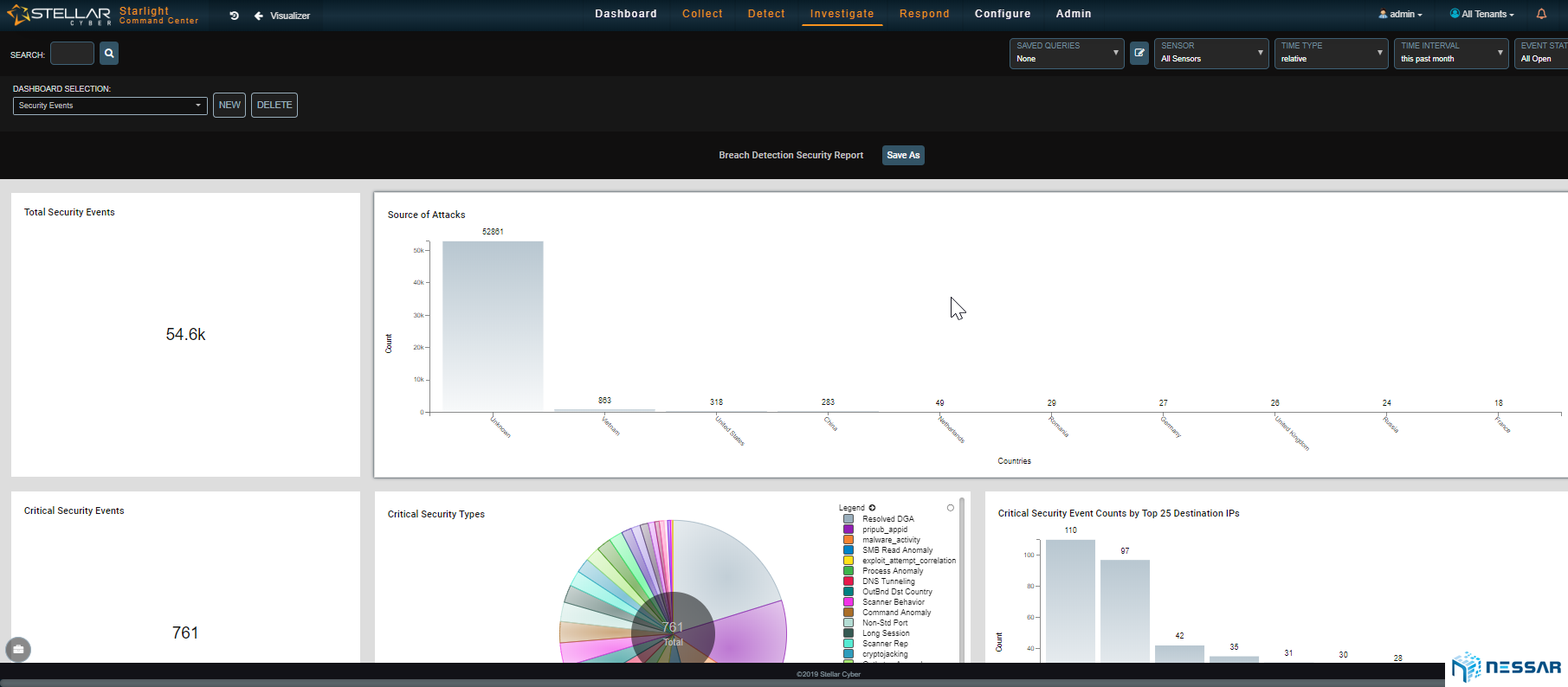
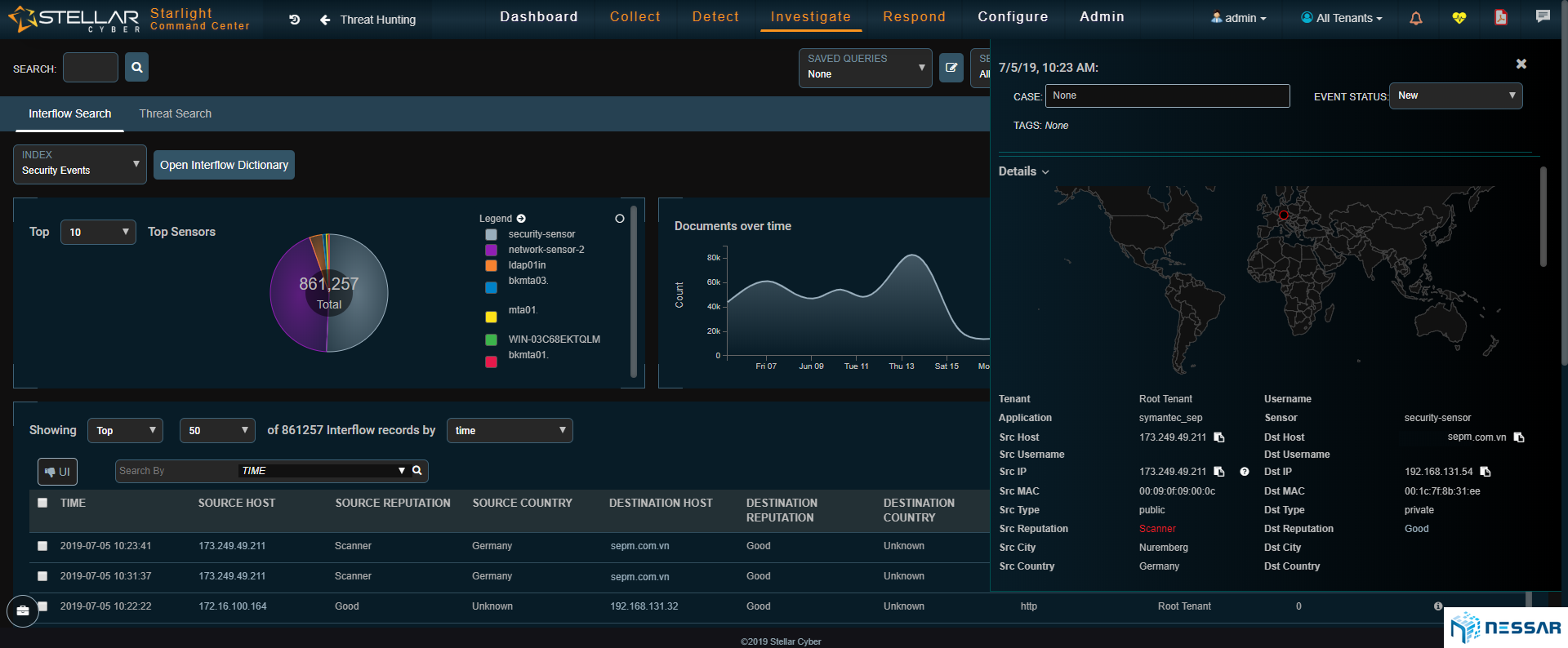
Threat Hunting
With Starlights unique data collection and Interflow™ technology, the platform enables admins to perform threat hunting at ease.
Users can leverage any dashboard/report view as a template, click on data points to zoom in or out dynamically and even enter their own queries with a Google like search bar to get the bottom of any incident.
Each and every record has the contextual data to grasp the details immediately and Interflow™ has all the evidence that admins need to make their ultimate decision.
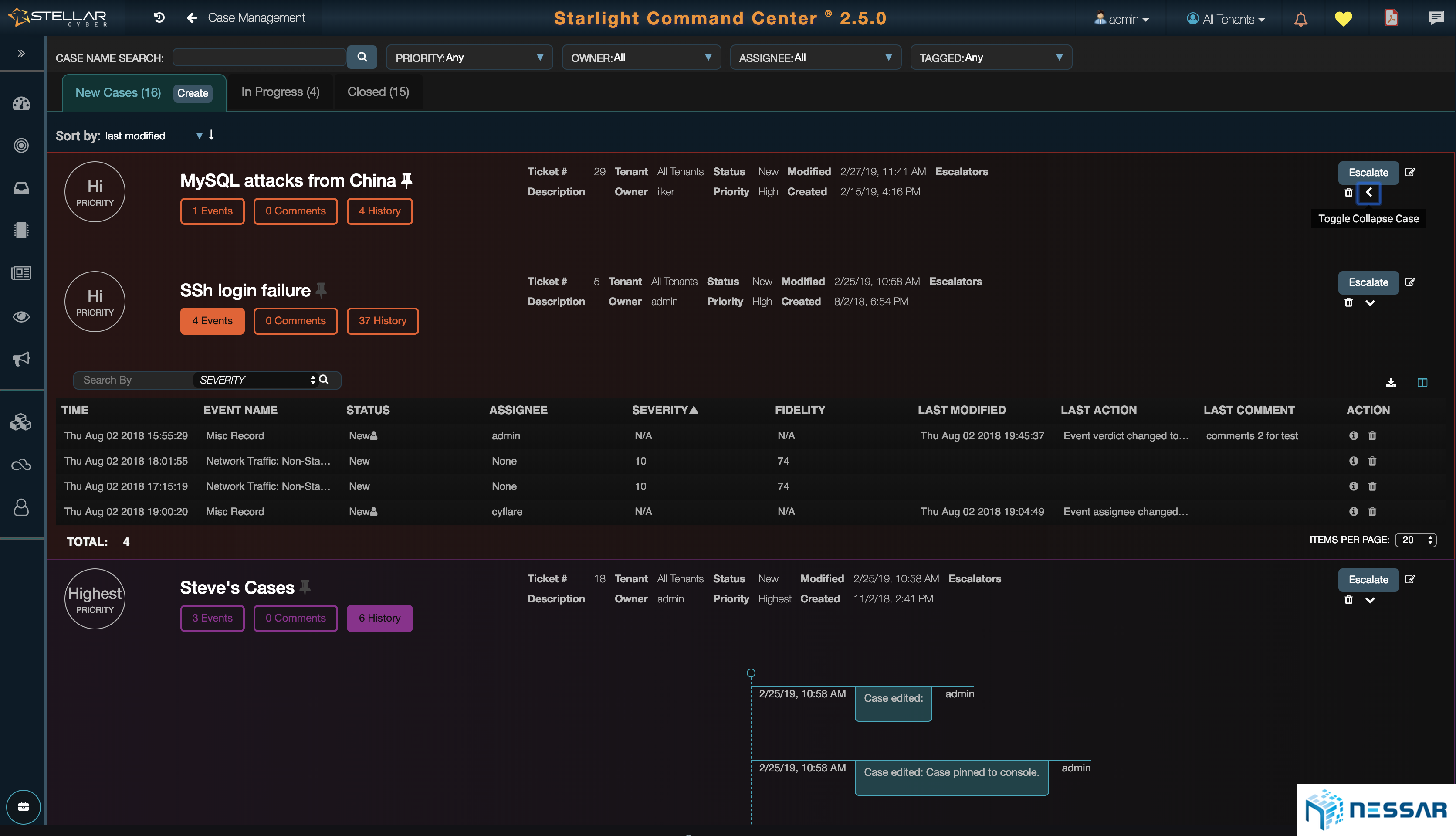
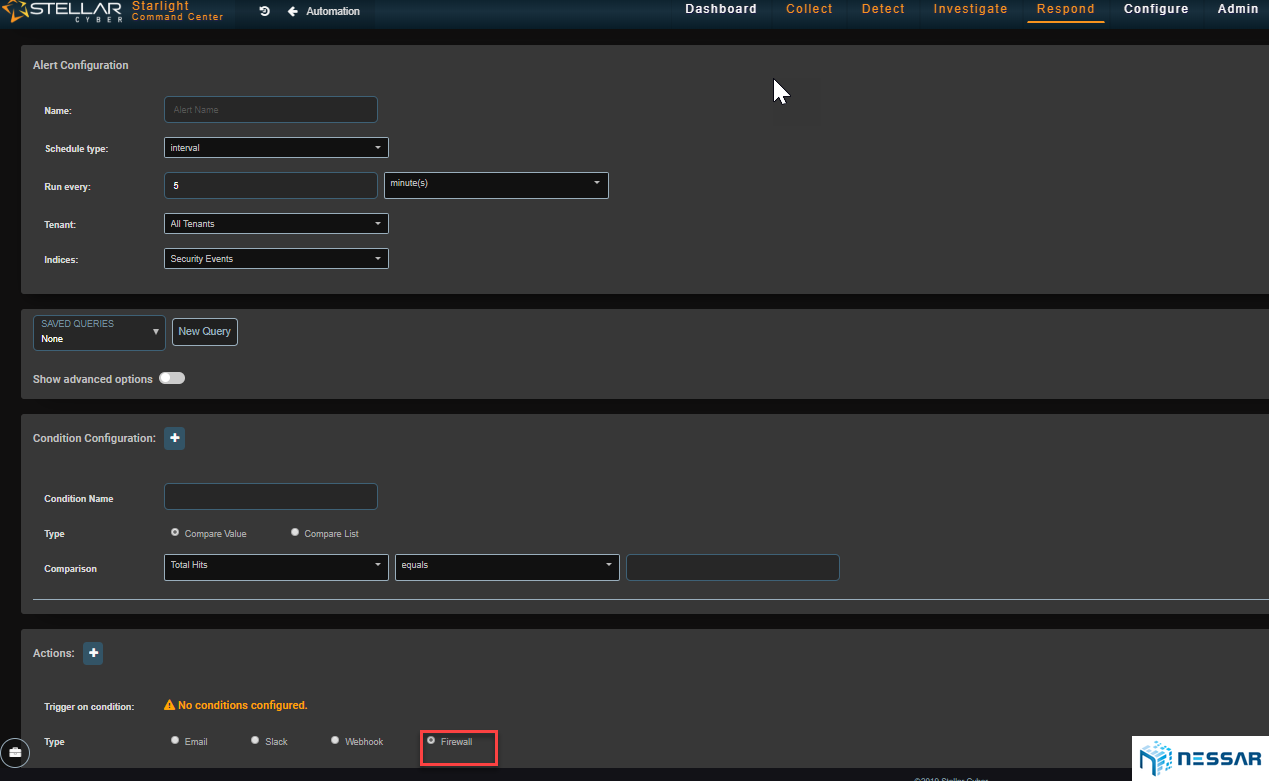
Automated Threat Hunting
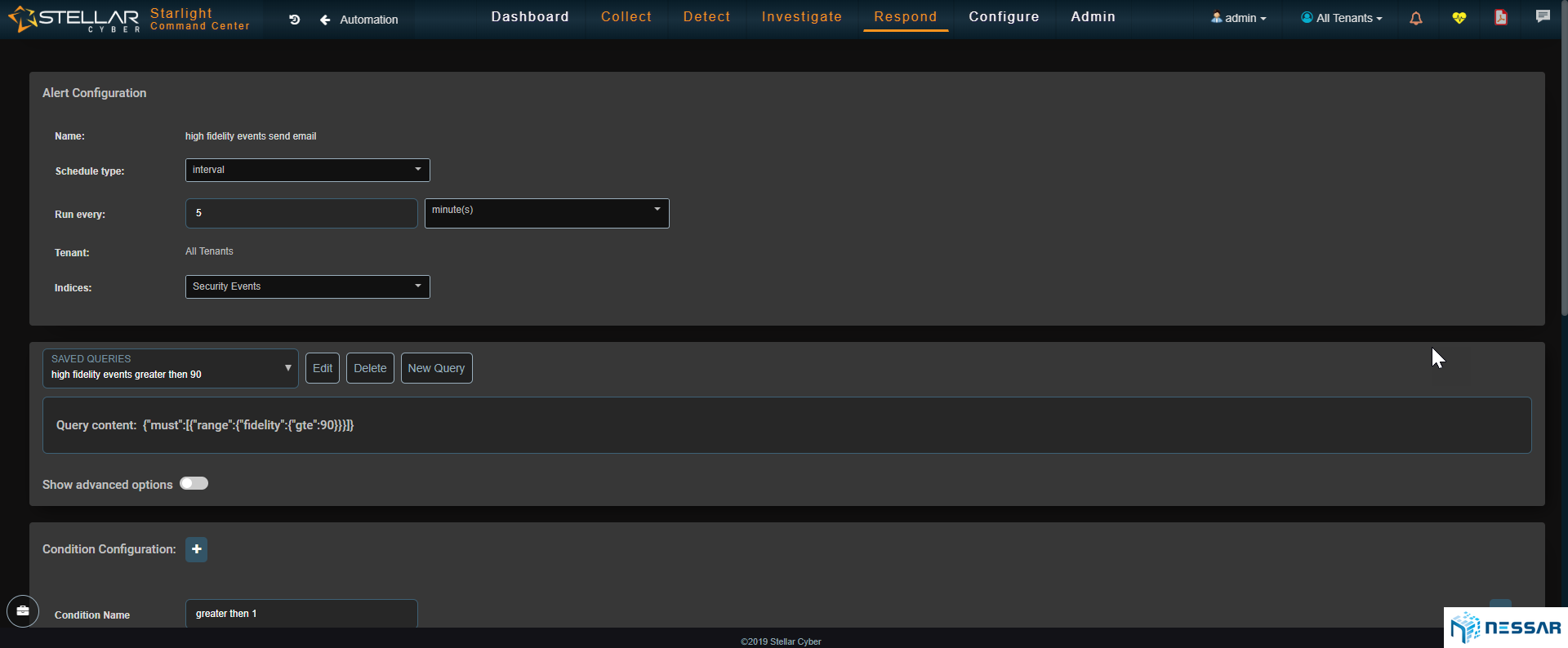
Starlight automates the way admin searches for threats and also automates response actions. The platform delivers huge time, human capital, and cost savings for companies.
Admins can create rules and queries to be run on a desired period and set up an alert via email, slack or webhook to notified admins of any new findings immediately.
An example, search for any login failures with the source country Russia and destination of an internal application every 10 minutes. If any record is found, alert the “Threat Hunting” group via Slack and also put 1 hour block rule to the relevant firewall in order to mitigate the possible attack until the event is fully investigated.
Click edit button to change this text. Lorem ipsum dolor sit amet, consectetur adipiscing elit. Ut elit tellus, luctus nec ullamcorper mattis, pulvinar dapibus leo.
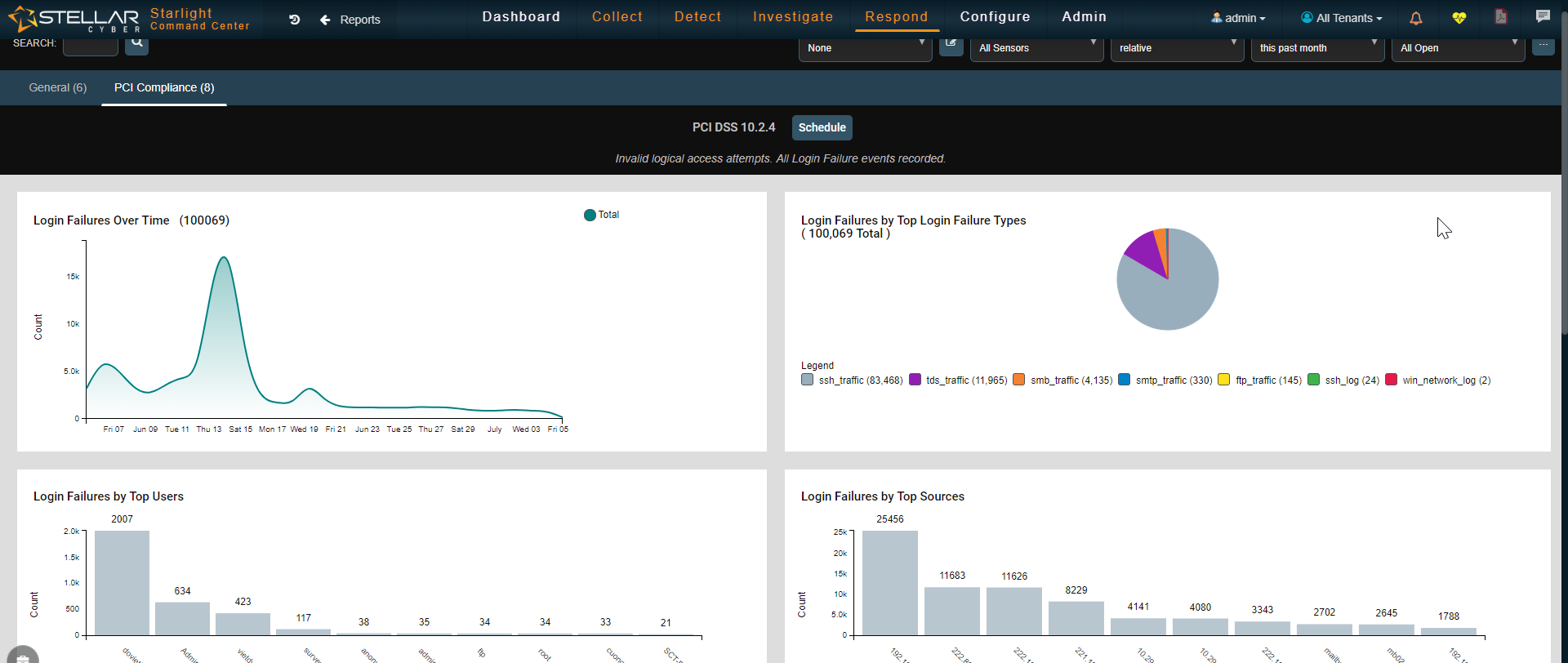
Reporting / Compliance
Starlight enables comprehensive reporting capabilities including compliance reports.
Admins can leverage existing reports, can customize any of them to their needs and can create custom reports with unlimited data and visualization possibilities to satisfy their business requirements.
The Starlight platform also provides a scheduling function to send the reports via email on desired periods and timeline.
Response
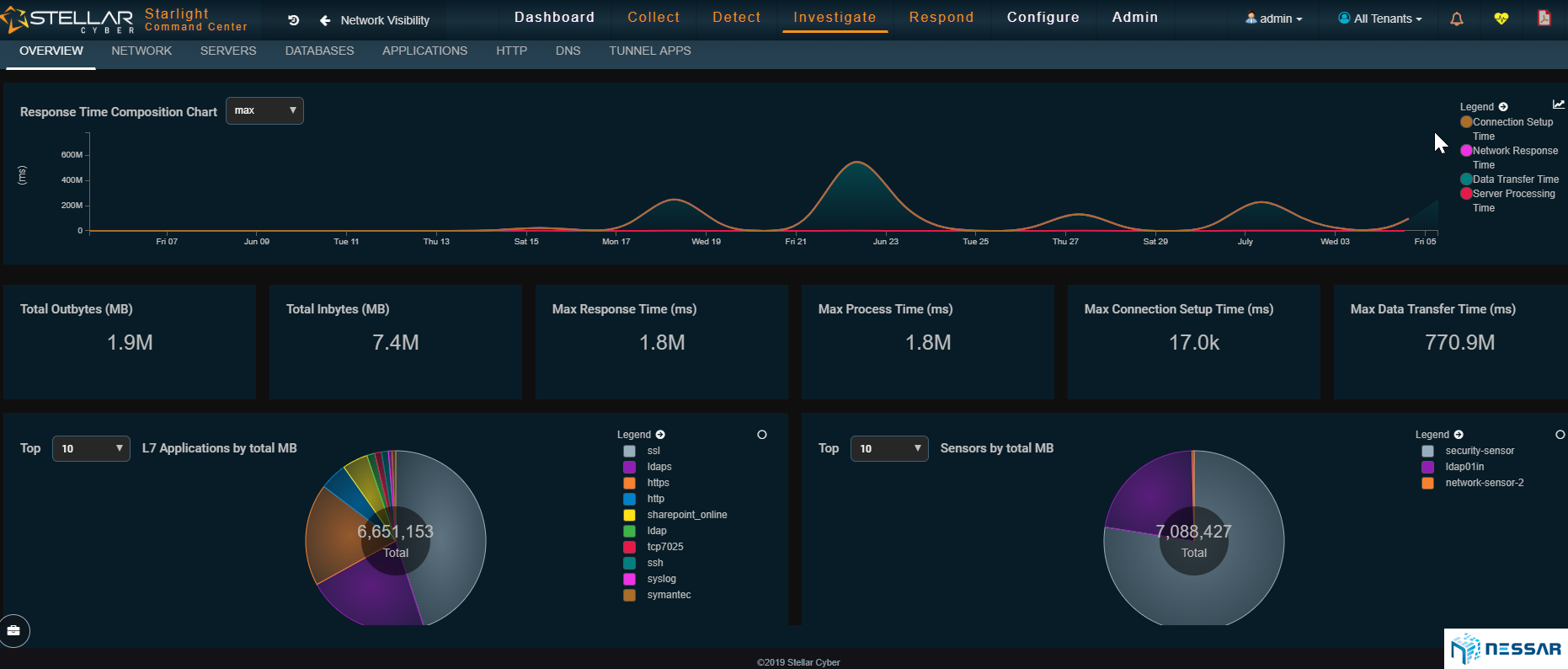
Network Traffic Analyzer
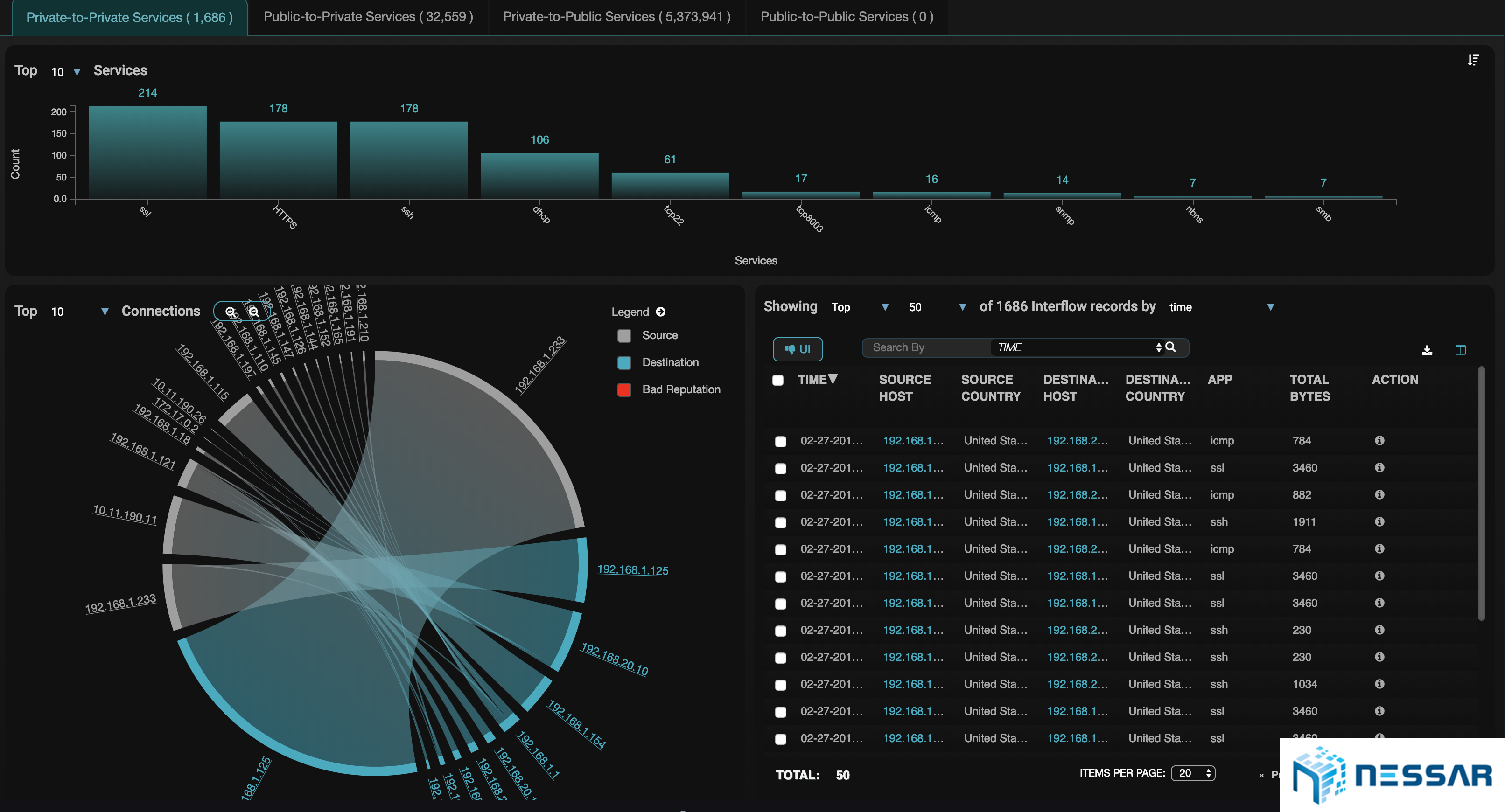
Network Traffic Analysis View
Starlight is also a great tool for network traffic analysis, such as commonly done with NetFlow collector tools. Because Starlight uses Interflow™ to capture L2-L7 flow telemetry we are able to visualize the performance of networks, servers, and applications. Admins are able to quickly identify performance bottlenecks, understand which applications are being used the most, and see if the server is causing any problems or if the network itself is at fault.