PAMaturity
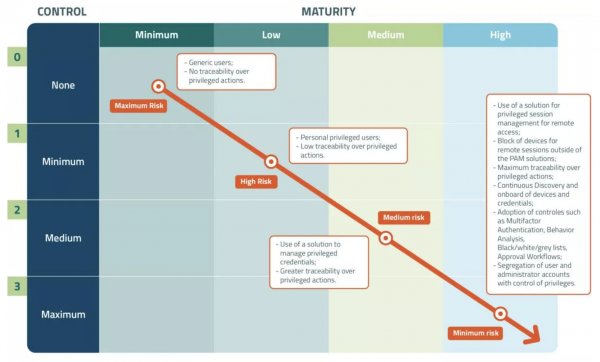
PAMaturity Find out your PAM maturity level. We at senhasegura take Privileged Access Management (PAM) seriously. And we want to bring all of our PAM...
View morePAM Advanced Monitoring
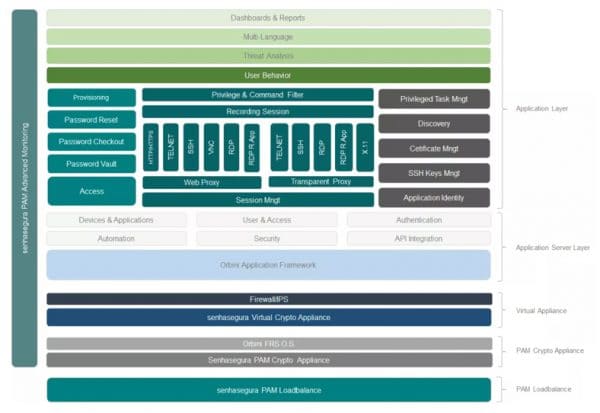
PAM Advanced Monitoring Full monitoring of the senhasegura solution. What it is Monitoring of senhasegura operation aspects and its components. Benefits Operational gain in the...
View morePAM Load Balancer
PAM Load Balancer Optimal usage of senhasegura resources. What it is Integrated load balancing solution, which monitors various aspects of senhasegura Cluster and performs...
View moreLocal User Provisioning
Local User Provisioning Create and manage local users centrally. What it is Provisioning and revocation of privileged local user access on Windows, Linux and...
View moreCertificate Management
Certificate Management Automatic and centralized digital certificate management. What it is Centralized management of digital certificates lifecycle within the organization, from discovery through automatic scanning...
View morePrivilege Management Linux
Privilege Management Linux Restrict user privileges on Linux endpoints. What it is senhasegura.Go for Linux allows the execution of Run As function on local endpoints...
View moreDevOps and Secret Management
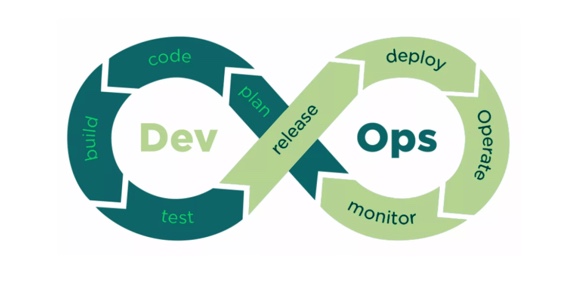
DevOps and Secret Management Senhasegura is fully compliant with DevOps environments. DevOps and Secret Management Currently, the software delivery pipeline is focused on delivering...
View morePrivilege Management for Windows Endpoints
Privilege Management for Windows Endpoints Restrict user privileges on Windows workstations. What it is Allows the execution of Run As feature on local workstations to...
View moreApplication Identity
Application Identity Eliminate hard-coded passwords and identify privileged accesses. What it is It’s possible to delete credentials embedded in source codes, scripts and configuration files,...
View moreSSH Key Management
SSH Key Management Securely control the SSH key cycle. What it is Secure storage, rotation and access control for SSH key protection. Benefits Blocking unauthorized...
View moreSaaS Access Management (PAM)
SaaS Access Management Fast and easy protection of privileged access. The compliance with current standards and regulations (LGPD; DGPR; PCI DSS; ISA 62443; among others)...
View morePrivileged Change Audit
Privileged Change Audit Ensure that actions are performed correctly. What it is The Privileged Change Audit feature is dedicated to protecting groups of devices and...
View moreLocal User Provisioning
Local User Provisioning Create and manage local users centrally. What it is Provisioning and revocation of privileged local user access on Windows, Linux and...
View moreCertificate Management
Certificate Management Automatic and centralized digital certificate management. What it is Centralized management of digital certificates lifecycle within the organization, from discovery through automatic scanning...
View moreCloud Identity and Access Management
Cloud Identity and Access Management The world has changed a lot in recent years, not only in how business is conducted, but also in how...
View morePAMaturity
PAMaturity Find out your PAM maturity level. We at senhasegura take Privileged Access Management (PAM) seriously. And we want to bring all of our PAM...
View morePAM Advanced Monitoring
PAM Advanced Monitoring Full monitoring of the senhasegura solution. What it is Monitoring of senhasegura operation aspects and its components. Benefits Operational gain in the...
View morePAM Load Balancer
PAM Load Balancer Optimal usage of senhasegura resources. What it is Integrated load balancing solution, which monitors various aspects of senhasegura Cluster and performs...
View morePAM Security Appliance
PAM Security Appliance Increased security and performance for your PAM solution. What it is Appliance-based hardware solution with custom operating system and embedded proprietary database...
View moreChina has Published Its Specific Law for the Protection of Personal Data. What Are the Implications?
China has Published Its Specific Law for the Protection of Personal Data. What Are the Implications? Global efforts to ensure data protection have increased dramatically...
View moreThe benefits of Using Cloud Computing
The benefits of Using Cloud Computing Cloud computing has been around for some time, and while data points to the efficiency, cost-effectiveness, and competitive advantages...
View moreThe Biggest Cyberattacks of Recent Years
The Biggest Cyberattacks of Recent Years We all know that cyber vulnerabilities are not a current issue. However, with the evolution of technology and virtualization growing...
View moreDigital Sovereignty: The Precepts of Senhasegura According to an American Periodical
Digital Sovereignty The Precepts of Senhasegura According to an American Periodical Nomenclatures and acronyms are part of the routine of those who work in...
View moreWhy is Data the New Oil?
Why is Data the New Oil? Performing any task today is much easier than it was a few years ago. With the evolution of...
View moreWhy is Information Security Important to Your Organization?
Why is Information Security Important to Your Organization? As technology becomes increasingly sophisticated, criminals’ skills often evolve as well, in many cases surpassing the...
View moreIs your company really prepared for a cyber attack? – Part 2
Is your company really prepared for a cyber attack? – Part 2 In the previous article, we discussed the importance of digital transformation to...
View moreSenhasegura: The Pillars of Information Security – Part 2
The Pillars of Information Security – Part 2 Currently, the use of information is a great ally for companies from different industries. However, along with...
View more