Product
OWASP Top 10 Compliance with RidgeBot 3.6 What is OWASP Top 10? Security breaches and attacks have become so prevalent that only the very largest ones now make the But attacks against organizations of all sizes have never been so rife or so sophisticated, making it all the more critical that you do everything […]

OWASP Top 10 Compliance with RidgeBot 3.6
What is OWASP Top 10?
Security breaches and attacks have become so prevalent that only the very largest ones now make the But attacks against organizations of all sizes have never been so rife or so sophisticated, making it all the more critical that you do everything you can to protect your organization’s digital assets.
The Open Web Application Security Project (OWASP) is a non-profit organization that works towards raising awareness, improving, and managing web application security Virtually all businesses and other public/private organizations in today ’s digital economy maintain web applications and servers to advertise, buy, sell, inform, and serve their customers or members in countless ways. By definition, a web application is public-facing: this makes it especially vulnerable to exploits from anywhere at any time. To protect your organization against security attacks and breaches, it is imperative to manage closely the vulnerabilities in web application software interactions. OWASP evaluates the most prevalent and critical web application vulnerabilities to produce a Top 10 list that is updated every 3-4 years. The most recent report was published in 2017. The OWASP Top 10 project uses broad industry consensus to determine the 10 most critical web application security risk categories. Well-known industry CWEs (Common Weakness Enumeration) are mapped into the Top 10 categories. The CWEs in turn draw on a larger database of CVEs (Common Vulnerabilities and Exposures) maintained in the National Vulnerability Database (NVD) under the direction of the U.S. National Institute of Standards and Technology (NIST) Cybersecurity Framework.
Understanding the OWASP Top 10 Categories
The 2017 Top 10 OWASP vulnerabilities are:
A1:2017 Injection: Injection flaws, such as SQL, NoSQL, OS, and LDAP injection, occur when untrusted data is sent to an interpreter as part of a command or query. A2:2017 Broken Authentication: Authentication and session management functions implemented incorrectly allow attackers to compromise passwords, keys, or session tokens to exploit user identities.
A3:2017 Sensitive Data Exposure: Many web applications and APIs do not properly protect sensitive data, such as financial, healthcare, and personally identifiable information (PII), allowing attackers to steal or modify such data to conduct fraud, identity theft, or other crimes.
A4:2017 XML External Entities (XXE): Many older or poorly configured XML processors evaluate external entity references within XML documents. External entities can be used to perpetrate other data, crimes and attacks.
A5:2017 Broken Access Control: Improper enforcement of restrictions on what authenticated users are allowed to do enable attackers to exploit access to unauthorized functionality and/or data.
A6:2017 Security Misconfigurations: Security misconfiguration is the most commonly seen issue, including insecure default configurations, incomplete or ad hoc configurations, open cloud storage, misconfigured HTTP headers, and verbose error messages containing sensitive information.
A7:2017 Cross-Site Scripting (XSS): XSS flaws occur whenever an application includes untrusted data in a new web page without proper validation or escaping, or updates an existing web page with user supplied data using a browser API that can create HTML or JavaScript.
A8:2017 Insecure Deserialization: Insecure deserialization often leads to remote code execution, or can be used to perform replay attacks, injection attacks, and privilege escalation attacks.
A9:2017 Using Components with Known Vulnerabilities: Exploiting a vulnerable component—such as libraries, frameworks, and other software modules that run with the same privileges as the application—can lead to serious data loss or server takeover.
A.10:2017 Insufficient Logging and Monitoring: Insufficient logging and monitoring, coupled with missing or ineffective integration with incident response, allows attackers to further attack systems, maintain persistence, pivot to more systems, and tamper, extract, or destroy data.
Ridge Security’s CWE to OWASP Top 10 Mapping
The OWASP Top 10 categories provide an easy, clear at-a-glance summary of the ten most critical web application security risks. To protect your organization’s web applications and servers, you must understand which specific vulnerabilities (CWEs) are included in each of the OWASP Top 10 categories.
While there is broad industry agreement on mapping CWEs to OWASP categories, there are differences in the specific implementations by different security mitigation vendors’ products. These details matter to the breadth of coverage and protection you get from using a specific vendor’s product to pentest your web applications. RidgeBot covers a comprehensive list of CWEs in each OWASP Top 10 category, providing you with the highest confidence that RidgeBot ’s pentest and exploitation capabilities result in thorough protection of your organization’s web application and servers.
A1:2017 Injection
|
|
|
|
|
|
|
|
|
|
|
|
|
|
A2:2017 Broken Authentication
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
A3:2017 Sensitive Data Exposure
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
A4:2017 XML External Entities (XXE)
|
|
A5:2017 Broken Access Control
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
A6:2017 Security Misconfigurations
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
A7:2017 Cross-Site Scripting (XSS)
|
A8:2017 Insecure Deserialization
|
|
|
|
A9:2017 Using Components with Known Vulnerabilities
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
A.10:2017 Insufficient Logging and Monitoring
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
|
How a RidgeBot OWASP Top 10 Report Helps with Security Audits
Because the CWE to OWASP TOP 10 mappings vary among vendor implementations, the statement that your organization is “OWASP Top 10” compliant remains ambiguous. During an audit you may have to provide detailed evidence of protection for each of the specific CWEs that you, or the auditor, believe makes you OWASP compliant.
RidgeBot ’s comprehensive built-in OWASP report streamlines providing evidence to management or auditors that all your web applications are OWASP Top 10 compliant.
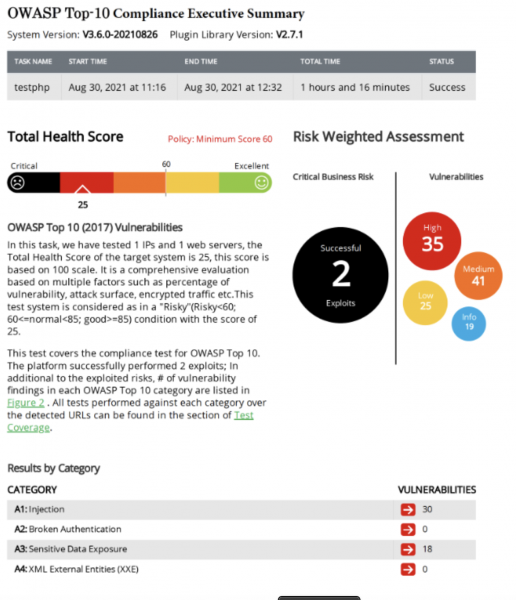
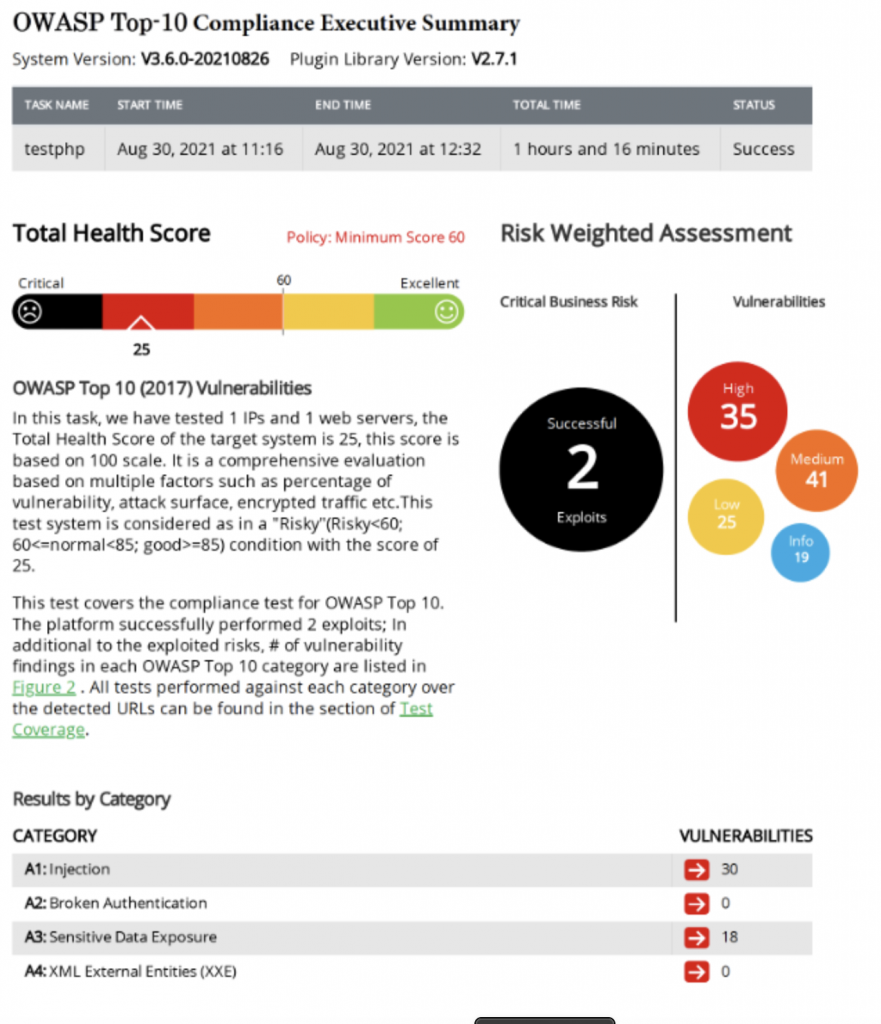
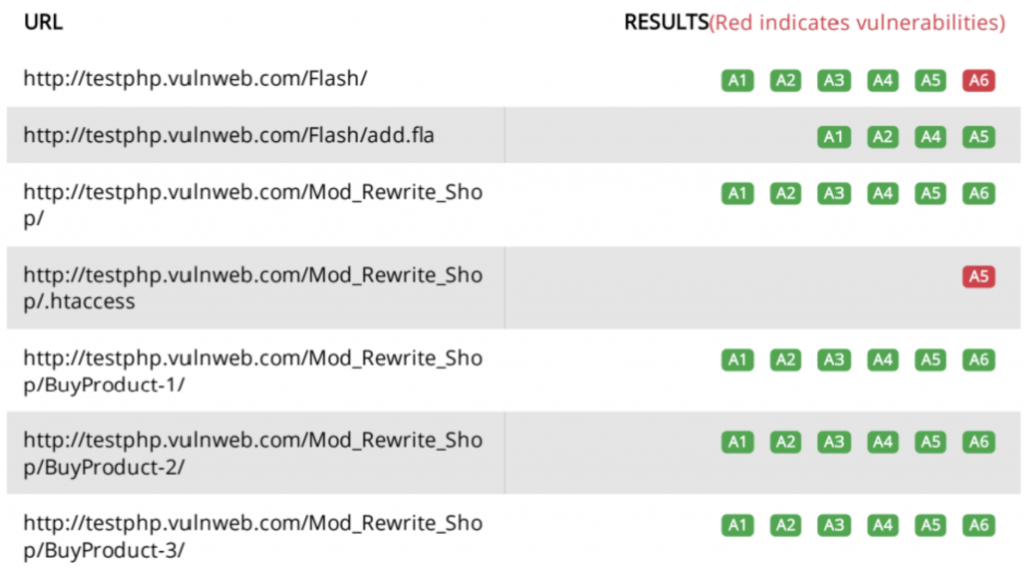
The header of the RidgeBot OWASP Top 10 report gives an executive summary of all the vulnerabilities found—classified into appropriate levels of severity—as well as those that were successfully exploited (red arrow). Further down (green arrow), the report provides detailed compliance information for each of the OWASP Top 10 categories and for the exact CWEs tested in each category.
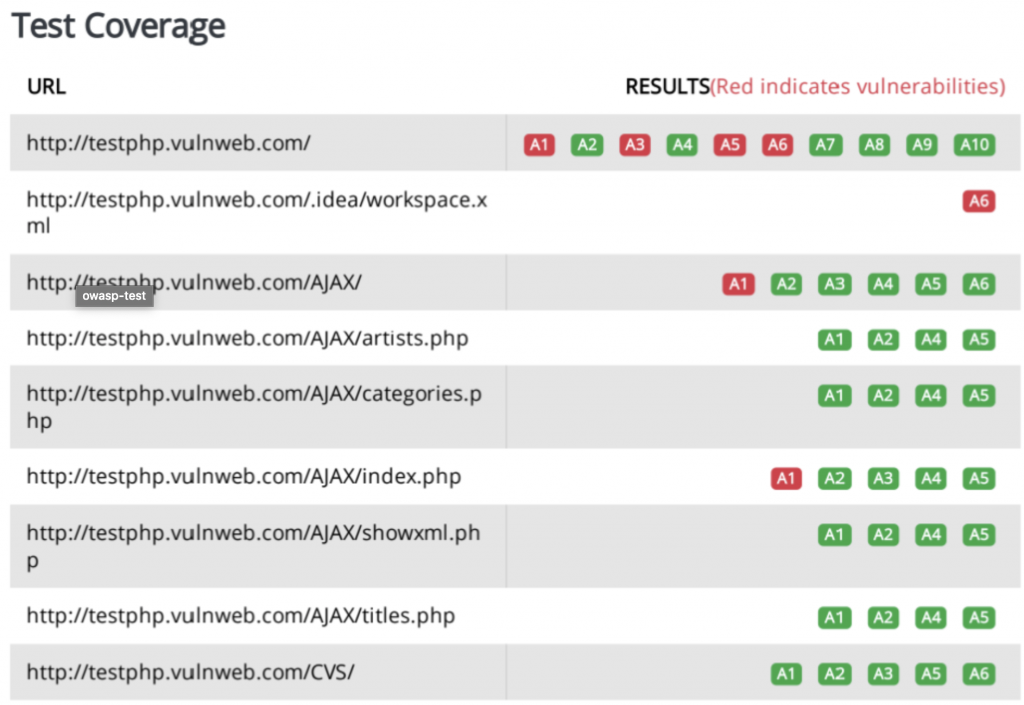
For each of the servers you subjected to RidegBot web penetration testing and exploitation, the body of the report indicates the compliance status of each of the OWASP Top 10 categories. This information gives you an instant roadmap to patch, upgrade or replace your applications to become compliant. It also gives you ready evidence to present to an auditor that your applications and servers are compliant.
The Benefits of Using RidgeBot to Maintain Protection Against OWASP Top 10
The OWASP community provides helpful information and tools to address web application security risks. While the Top 10 list is an extremely helpful and broad industry benchmark, it does not ease the burden of implementing a strategy to know how your web applications measure up, or how to fix lingering vulnerabilities. The Top 10 list also does not provide specifics of which exact CWEs your applications are protected against.
A RidgeBot pen-testing and exploitation run targets a comprehensive and industry- superior set of CWE vulnerabilities in each Top 10 category. The built-in report provides exact details of every Top 10 category and CWE tested and/or exploited. With a periodic—the frequency of your choosing—RidgeBot test-exploit against your web servers and applications you can always rest assured that your organization’s digital assets are as secure as possible from reigning web-based attacks. You can provide on-demand information and evidence to management or auditors about the state of compliance of your organization’s web-based activities. The report also includes detailed steps for resolving any vulnerabilities found—and the relative priority of each—that can guide staff on the specific actions to take to become or maintain 100% compliance.