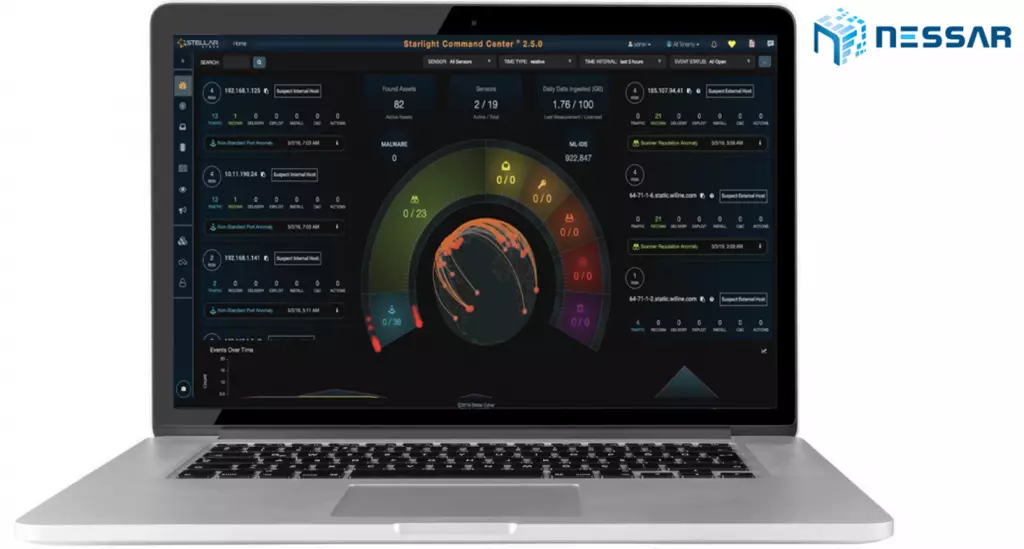
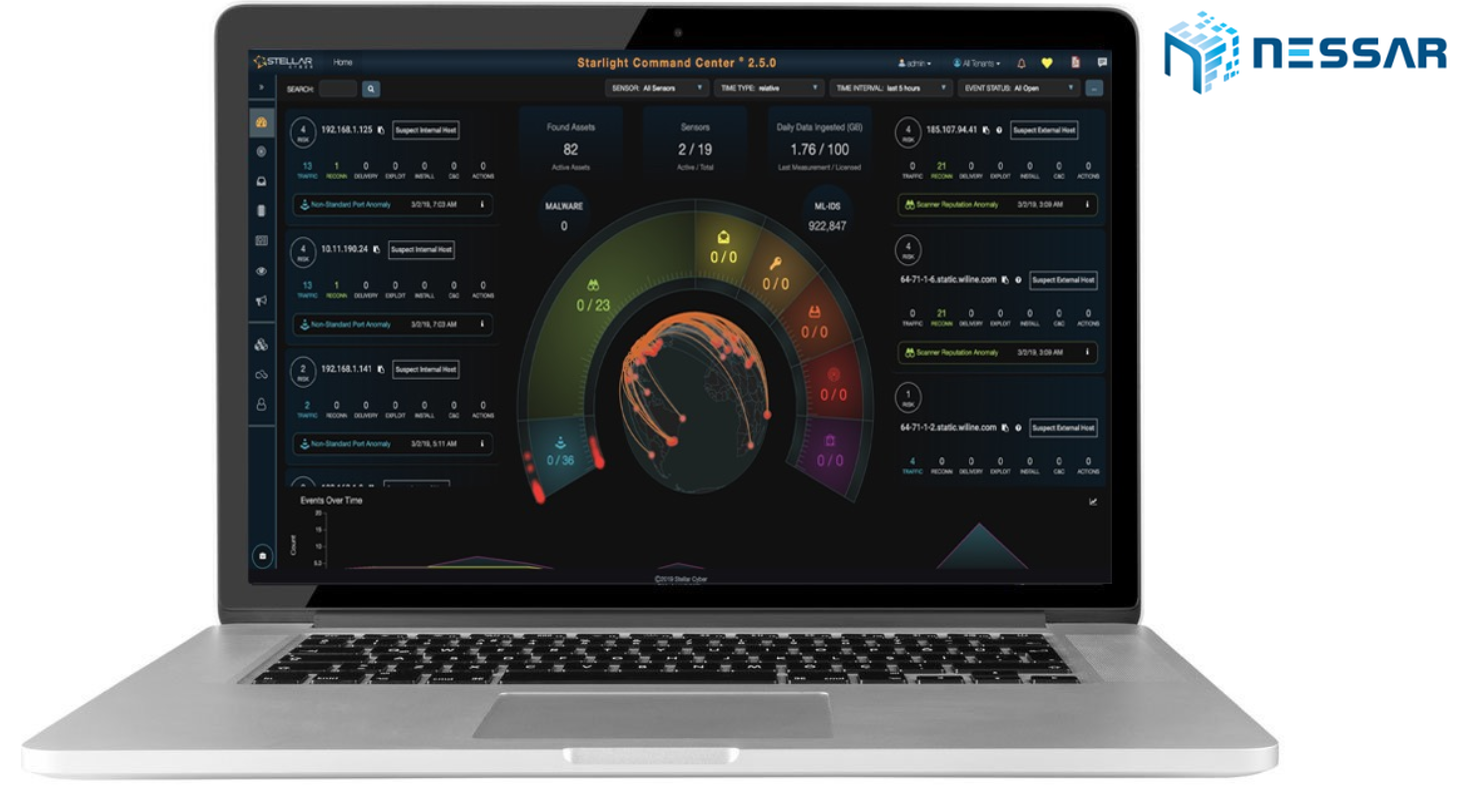
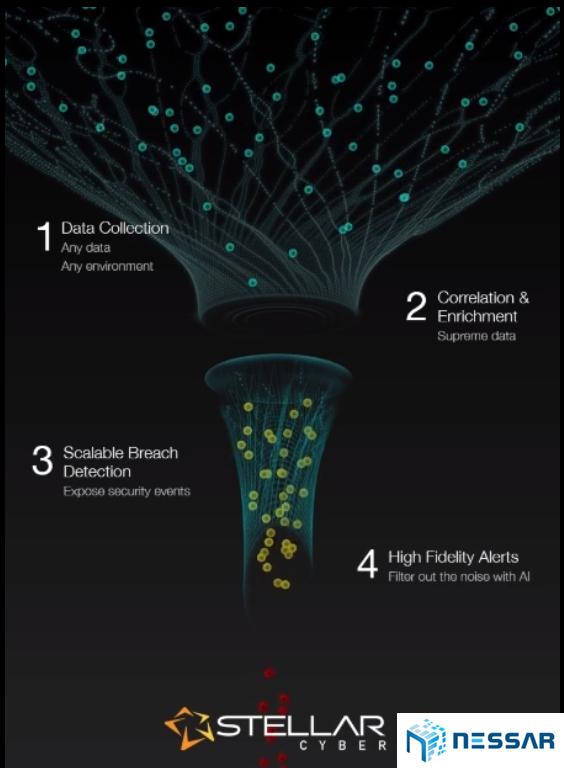
Công Ty Cổ Phần Công Nghệ Nessar Việt Nam - Nessar
- HOME
- ABOUT US
- SOLUTIONS
- ENTERPRISE SOLUTIONS
- SECURITY SOLUTIONS
- INDUSTRIES BASED SOLUTIONS
- VENDORS SOLUTIONS
- PRODUCT
- STELLAR CYBER
- HILLSTONE
- QUANTUM
- FIREMON
- SOTI
- DELPHIX
- QUEST
- ARRAY NETWORKS
- CUBRO
- SEGURA
- PRE SECURITY
- RIDGE SECURITY
- HOLM SECURITY
- LIVEACTION
- DIGITAL.AI
- ADVENICA
- CYFIRMA
- HIVEPRO
- ACTI
- CYBERTEST SYSTEM
- REDIS
- PROJECTS