admin.nessar
Hillstone Server Protection Solution
Comprehensive Server Protection with Unparalleled Visibility and Efficacy Hillstone Server Breach Detection System (sBDS) I-Series product line detects and helps mitigate advanced multi-stage, multi-layer, threats...
View morePAM Market Trends According to Gartner
PAM Market Trends According to Gartner Protecting privileged credentials is essential in the cybersecurity strategies of companies of all sizes and verticals. According to Verizon...
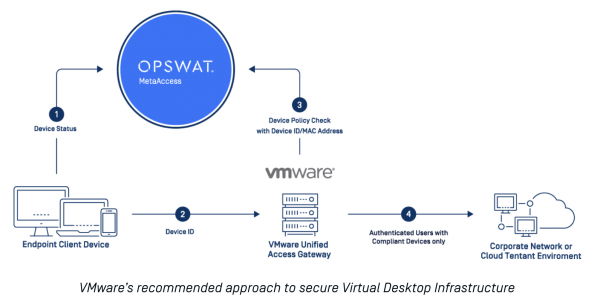
View moreOPSWAT Solutions now available in VMware Marketplace
OPSWAT Solutions now available in VMware Marketplace As a leading provider of security solutions protecting the world’s most critical infrastructure, OPSWAT has built a network...
View moreWhat is An Incident Response Plan (IRP) and why is It Important to Have One?
What is An Incident Response Plan (IRP) and why is It Important to Have One? With the evolution of technology and the revolution in the...
View moreRecently discovered Zimbra vulnerabilities may have compromised 200,000 companies
Recently discovered Zimbra vulnerabilities may have compromised 200,000 companies Zimbra, an open-source collaborative office suite, consisting of webmail, web...
View moreHillstone Cloud Protection
Hillstone Cloud Protection Easily Protect your Cloud Applications and Resources With the adoption of public clouds and increasing importance of virtualization, organizations need security solutions...
View moreHillstone Edge Protection Solutions
The First Line of Defense Multi-stage, Multi-layer Attacks Hillstone Edge Protection Solutions Reimagine Perimeter Defense For many corporations, the enterprise edge is the first line...
View moreThe Pillars of Information Security
The Pillars of Information Security Given the importance of protecting employees and the information of an entire corporation, it is essential to understand and put...
View moreQuantum Agencies Manage and Protect Mission-Critical Data
Helping Agencies Manage and Protect Mission-Critical Data Government agencies make critical decisions every day by leveraging data collected for their missions and programs – from...
View moreClustering and other Enhancements for Hillstone ADCs
Clustering and other Enhancements for Hillstone ADCs Recently, Hillstone announced the release of its Application Delivery Controller (ADC) version 2.8. This release offers new models...
View moreCyberattacks Have Increased During the Pandemic, Learn How to Protect Yourself
Cyberattacks Have Increased During the Pandemic Learn How to Protect Yourself Cyberattacks have been causing concern and discomfort for those who use and depend on...
View moreMyths and Truths About Privileged Access Management
Myths and Truths About Privileged Access Management Implementing privileged access management to systems in a company is critical to ensuring that there are no information theft and...
View more