admin.nessar
Ridge Security Announces Expanded Core Capabilities in RidgeBot with Enhanced Web Application Testing
Ridge Security Announces Expanded Core Capabilities in RidgeBot with Enhanced Web Application Testing From network, to host, to web applications, RidgeBot 3.5 delivers the most...
View moreHow to Act in Case of Data Invasion and Theft?
How to Act in Case of Data Invasion and Theft? In the contemporary world, where the use of technological means and virtual systems is becoming...
View moreCommon Questions about Privileged Access Management (PAM) Solutions
Common Questions about Privileged Access Management (PAM) Solutions With technology increasingly present in our lives, ensuring the security of your company’s information has become a...
View moreWhat Is a Network Packet?
What Is a Network Packet? Everything flowing through a network can be classified as part of data enclosed in a packet. A network packet or IP packet...
View moreThe Past, Present, and Future of Pentesting
The Past, Present, and Future of Pentesting Pentesting, or penetration testing, is a cybersecurity measure that fights hackers by exposing the hacker’s possible entry points,...
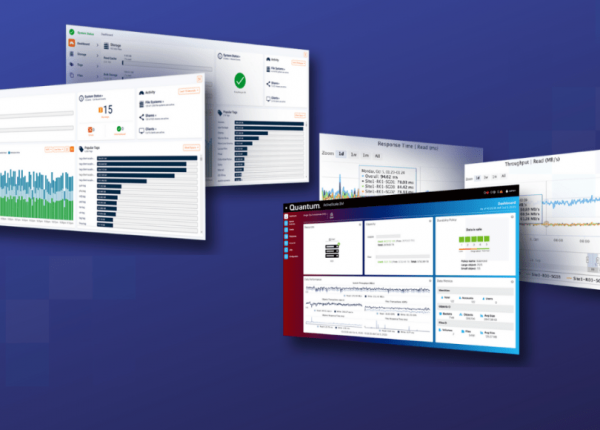
View moreQuantum’s Portfolio for Managing Unstructured Data
Quantum’s Portfolio for Managing Unstructured Data This week, we made a significant announcement, introducing an expanded portfolio focused on classifying, managing, and protecting unstructured data...
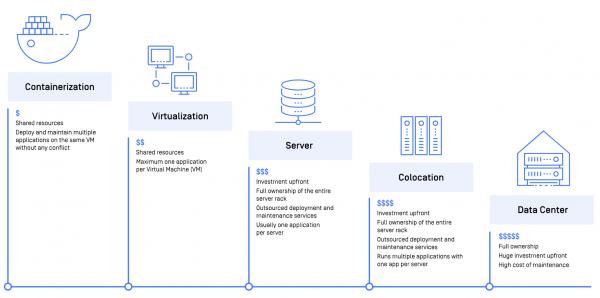
View moreEvolution of Infrastructure: From Data Centers to Containers
Evolution of Infrastructure: From Data Centers to Containers The impact of the digital transformation revolution requires organizations to look for more efficient solutions to manage,...
View moreHow to Measure Network Performance Effectively
How to Measure Network Performance Effectively To run an enterprise effectively today, a good chunk of the yearly budget will have to be directed towards...
View moreTypes of Network Monitoring Protocols
Types of Network Monitoring Protocols Corporate networks as a system are made up of numerous components, and it is not uncommon that some components due...
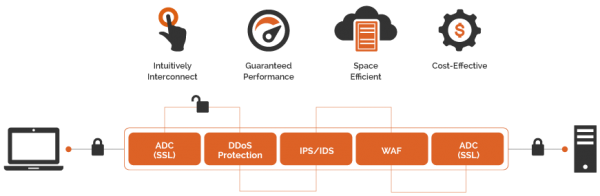
View moreApplication Delivery That’s Simple Yet Scalable & Powerful Yet Cost-Effective
Application Delivery That’s Simple Yet Scalable & Powerful Yet Cost-Effective Array APV Series application delivery controllers provide the availability, scalability, performance, security and control essential to keeping...
View moreHillstone Server Protection Solution
Comprehensive Server Protection with Unparalleled Visibility and Efficacy Hillstone Server Breach Detection System (sBDS) I-Series product line detects and helps mitigate advanced multi-stage, multi-layer, threats...
View moreTwin Mode HA for Redundant Data Centers
Full Security and Continuity for Intra-Data Center Traffic To support 24/7/365 application availability for enterprise operations, redundant data center design with application failover has become...
View more