File Upload Security Overview
Protect Against Malicious File Uploads
File uploads are essential for the effective functioning of an organization and are needed for collaboration between an organization’s workforce and for user productivity. They are a critical ingredient of most web applications and services. However, they represent a significant security risk since cybercriminals can compromise your servers or your entire system by uploading malicious files.
Enterprises need a robust layer of protection between uploaded files and their network.
Traditional detection and prevention mechanisms are insufficient to prevent cybercriminals from attempting to upload malicious content to penetrate your environment and steal data.
Integrating the multiple solutions needed to evaluate suspicious files and detect sensitive data leakage is costly and time-consuming.
Why you need file upload security protection
Protect Your Users
Do you allow user generated or external content (resumes, invoices, forms, installers, patches, etc.) into your organization?
Do you have a customer portal where you allow users to upload information/files?
Do you expose any collaboration tools or file exchange services to partners and customers?
Can you trust every file or installer downloaded or shared by your staff?
Protect Your Critical Infrastructure
Are you a major financial institution that accepts mortgage/loan applications, banking details, etc. or stores critical data like credit card numbers, social security numbers for millions of customers?
Are you a healthcare provider that accepts and stores sensitive PHI (Personal Health Information) data of patients?
Can you trust every external file uploaded into your web applications?
Attackers can target end users and infect their systems. They can steal sensitive information and PII (Personally Identifiable Information) data from them.
Your collaboration and hosting platform can inadvertently host and spread malicious samples that could contain illegal, offensive, or copyrighted content/data, resulting in regulatory fines, expensive lawsuits and bad publicity.
Hackers can bypass security and upload a new file or overwrite an existing file that can be used to launch a server-side attack. They could then take control of your server and data, bring down your website/application, exploit you for ransom, sell/expose sensitive information, or upload more malicious files into your system.
If an extremely large file (multi-level archives, etc.) is uploaded, this could result in high consumption of the servers’ resources and disrupt your service.
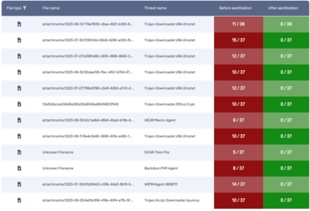
Zero-Day and Advanced Malware Prevention
Zero-day attacks, advanced persistent threats (APT), and sophisticated malware can be hidden in innocuous files and bypass traditional anti-virus solutions.
OPSWAT Deep CDR (Content Disarm and Reconstruction) technology sanitizes 100+ common file types to prevent both known and unknown threats – including threats that are equipped with malware evasion technology such as Fully Undetectable malware, VMware detection, obfuscation and many others.
The resulting output is usable safe-to-consume files for your end-users.
Data Loss Prevention
Detect, block, and redact sensitive and proprietary data like credit card numbers and social security numbers.
Content-check 40+ common file types for confidential data and personally identifiable information (PII) with Proactive DLP (Data Loss Prevention) technology and prevent potential data breaches and regulatory compliance violations.
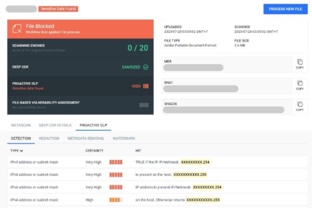

Meet Compliance Requirements
Regulatory rules are enforced to minimize breaches and privacy violations. Meeting compliance requirements is time-consuming and can be costly. If requirements like HIPAA, GDPR, PCI-DSS, etc. are not met, it can result in significant fines and penalties.
OPSWAT Technologies provide compliant processes, comprehensive visibility, and detailed reporting capabilities to help meet requirements in the OWASP guidelines.
Malware Detection and Prevention
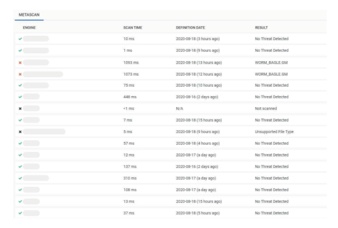
OPSWAT delivers proprietary Multiscanning technology, and is the known leader in the industry and proactively detects 99%+ of known malware threats by using signatures, heuristics, NGAV, and machine learning.
Simultaneous analysis leveraging the combined threat prevention of 30+ antimalware engines is an advanced threat detection and prevention technology that increases detection rates, decreases outbreak detection times and provides resiliency to anti-malware vendor issues.
Assess Vulnerabilities Before Deployment
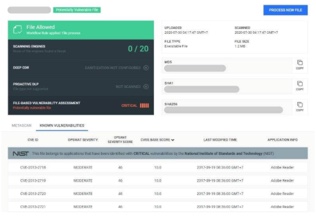
Uploaded files can trigger vulnerabilities in broken libraries or applications. Organizations are increasingly vulnerable to exploits during the detection window when an application is installed and when a vulnerability is detected. OPSWAT File-based Vulnerability Assessment – scans and analyzes binaries and installers uploaded through your website to detect known application vulnerabilities before they are installed or deployed.
File Upload Security Assessment
OPSWAT Professional Services can quickly assess your File Upload security readiness. We tailor the evaluation to your organization’s specific needs based on our proven methodology, then provide a detailed analysis report with follow up discussion and recommendations.

Why OPSWAT for File Upload Security
OPSWAT provides everything you need to secure your file uploads:
Visibility
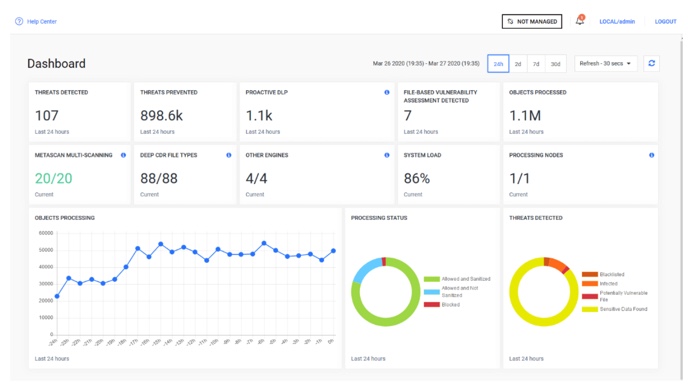
Monitor and evaluate your security status and potential risks at a glance.
Real-time dashboard immediately alerts you to potential threats and vulnerabilities in your assets. Drill deeper to investigate any areas of concern and take corrective actions.
High Performance and Scalability
Fast scanning and reconstruction of files in milliseconds without affecting performance. Scalability to any volume with our built-in high-performance architecture and load balancing features.
Simple and Flexible Deployment
Fast and scalable implementation on-premises and in the cloud using REST API or any Internet Content Adaptation Protocol (ICAP) enabled product.
Multi-platform (Windows, Linux) and multiple deployment mode (Docker, Cloud, Datacenter) support.
Customizations
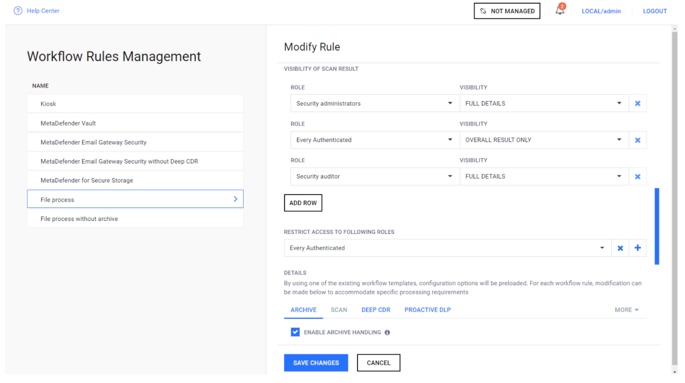
You have the flexibility and control to customize and create multiple workflows and rules to meet different security policies.
Administrators can create processes and restrict access based on users, file sources and file types to best fit the use case for your organization.
Low Overhead Implementation
Powerful control over cybersecurity through a single platform. This results in a higher ROI, higher adoption, lower overhead, and fewer trained professionals needed to oversee complex systems.
File Upload Security Options

File Upload Security Assessment
For a professional assessment of your file upload security and recommendations for improvements

MetaDefender Core
For integration with your existing security architectures via REST API

MetaDefender ICAP Server
For integration with web apps (via WAF, LB or API Gateway) or Storage (NAS) to detect and prevent threats in file transfer process

MetaDefender Cloud
For integration in cloud and IaaS environment or with your existing SaaS products via REST API and leveraging our large hash database, IP reputation services, and more
MetaDefender Core AMI
For deployment in your AWS account to process received files or protect your S3 buckets
Source : opswat.com
View more product : nessar.net