Secure Access
Trust Endpoint Access to Your Cloud and Local Networks
Solution Overview
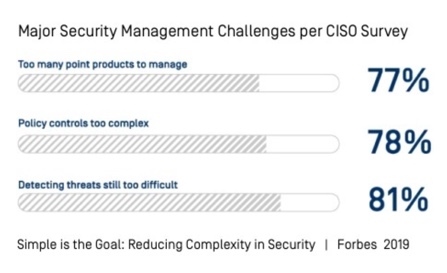
The proliferation of BYOD and cloud applications and the growing need to also access corporate data remotely has accelerated the demand for secure access including unmanaged device oversight and compliance. It is more important than ever to go beyond basic checks such as OS level and anti-virus to include removable media, unwanted applications, keyloggers and screen capture protection.
How can you confirm every device in your organization complies with security policies before accessing applications or your network, no matter where they are connecting from and where your data is located?
At the same time, in addition to ensuring the device is secure, organizations need secure access to the network, applications and data.
How OPSWAT can help
The OPSWAT solution provides a single integrated platform to address each one of these challenges and complexities. It is uniquely positioned to ensure that wherever your data is located and wherever the user is located, the access and the device will be secure and meet your security policies. Implementing secure access for remote and on-prem users, and ensuring endpoint compliance for managed, BYOD and IoT devices can take months to a year requiring senior network engineers and administrators, as well as third party consultants.
Use Cases for Secure Access
With this single platform approach, the implementation and management become easier for the IT staff, both to implement and manage on an ongoing basis, with no third-party services required. At the same time, users will gain access as needed, with easy self-remediation steps if there are issues to get back in compliance. For common applications such as VMware and Salesforce, even stronger integration is available for maximum productivity.
Secure Cloud, Remote and On-Prem Access
OPSWAT enables cloud integration through Security Assertion Markup Language (SAML), an open standard that allows identity providers (IdP) to pass authorization credentials to service providers (SP). OPSWAT also offers a zero-trust solution which supersedes VPNs with better security, easier management, and a more positive user experience.
Secure On-Prem Access
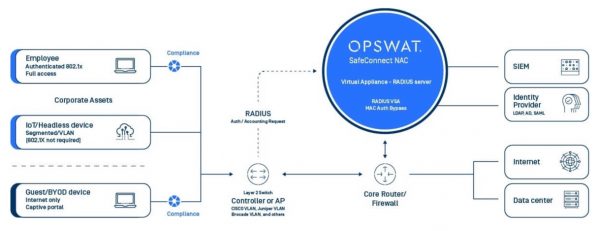
For an on-prem environment, OPSWAT provides detailed identification and security compliance to ensure you do know exactly what is on your network, can block any unauthorized attempts and enable segmentation placing IOT devices in the proper group.
Specialized Solutions
OPSWAT offers integrated solutions for specific environments, such as Virtual Desktop Infrastructure (VDI) and Salesforce to make it even easier for both IT and the end user to have a secure device and access for these situations.
In-Depth Compliance & Control
OPSWAT examines devices with standard security checks such as OS and Anti-virus and then goes much deeper, including a risk and vulnerability evaluation, with the ability to detect and fingerprint over 5,000 third-party applications. Other checks include encryption, removable media, anti-keylogger, screen capture protection, unwanted applications and multi-scanning, to detect active and passive malware.
Instant Visibility
OPSWAT illustrates the endpoint health of the entire environment and delivers control of every device accessing your network and cloud applications—on a single pane of glass. Administrators can conduct a detailed security review of any device and monitor which devices access which applications and when. A holistic dashboard illustrates risks, device activities, and current vulnerabilities across the enterprise.
Automatic & Self-Remediation
OPSWAT offers self-remediation options out-of-the box, minimizing costly help desk calls. To maximize productivity, some remediation options can simply be automated, such as updating the virus definitions on local anti-malware software, activating firewall software, and removing unwanted applications.
High BYOD Adoption
BYOD users frequently avoid access security software, because it is traditionally cumbersome and slows productivity. OPSWAT provides a lightweight client that conducts a quick, yet comprehensive assessment and is dis-solvable from the device.
Up-to-Date Vulnerability and Patch Management
Detect all the known threats in the Common Vulnerability and Exposures (CVE) library as well as using MetaAccess’ own scoring system created from guarding over 100 million endpoints to assist with prioritization.
What We Offer
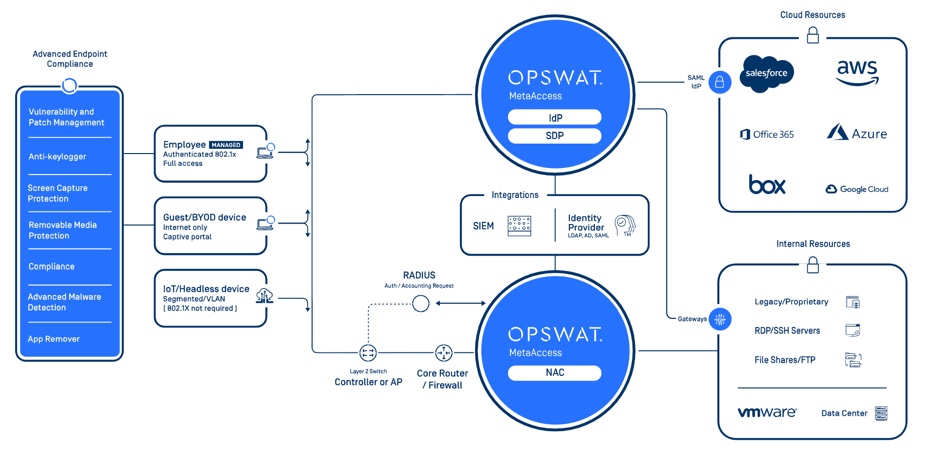
OPSWAT offers the MetaAccess Solution that addresses both secure access and device compliance in a single platform. As you can see in the diagram below, MetaAccess performs seven deep device security checks on your employee, BYOD or guest and IoT devices. If the device is compliant, you can then ensure secure access remotely or on-prem to only the authorized network segments and applications. With this platform, your security compliance is addressed, the amount of resources to implement and maintain are reduced, and your uses have a positive, cohesive experience to access company applications and data.
MetaAccess Platform
Cloud Access
To get true control over devices accessing the cloud, use OPSWAT’s SAML integration, a protocol for cloud access. With this capability, each user will be authenticated, compliance checked, and if found to be non-compliant, will not be allowed access to the cloud application. Instead, the user will be presented with a Self-Remediation page to address any issues, after remediating, they will once again be allowed access.
Remote Access
It’s time for organizations to rethink the way users access valuable applications and data. OPSWAT replaces your VPN with an offering that verifies security and compliance first and then only permits connections to applications and data resources. This Zero-Trust access model encrypts communications between user devices and applications and integrates with your existing Identity Access Management solution, easing management and enabling Multi-factor authentication in a seamless fashion.
On-Prem Access
For users’ devices in the office, gain the same visibility, security and control of all devices on your network with Network Access Control (NAC), which collects information about the device from multiple sources to properly assign the device to the proper segment on the network. Unauthorized users are blocked and will not be able to plug into an empty port. Non-compliant devices can be audited, warned or quarantined, depending upon the organization’s policies. This solution makes your other security investments smarter.
Specialized Solutions
Secure Virtual Desktop Access
Securing access to applications accessed using Virtual Desktop Infrastructure (VDI) by ensuring the device used to connect to the VDI server is critical, especially when the device is a BYOD. The VDI clients now allow many interactions with the underlying endpoint, and as such it is often important, for example, to prevent screen captures or key loggers. To help ensure the endpoint is secure and compliant before using a VDI client, OPSWAT integrates with VDI offerings from vendors like VMware.
OPSWAT Cloud Security for Salesforce
Given the level of reliance many companies have on Salesforce, with much of their valuable data on many aspects of their business stored there, securing access and ensuring compliance before users connect can both ensure that data is not compromised and that it is only accessed in a compliant fashion. OPSWAT offers a Salesforce app that integrates with our solution to ensure all risky devices will be denied access to Salesforce until they self-remediate.
Safeguard Against Vulnerable Devices
Every additional connected device exposes your network and cloud applications to vulnerabilities. Stolen devices, lack of password protection, updated security software, and misuse of encryption all create exposure points, as does exposure to keyloggers or screen capture. OPSWAT provides comprehensive device inspection, so that you can be confident that only trusted devices access your environment.
Meet Compliance Requirements
Regulatory compliance requirements are enforced to minimize breaches and privacy violations. Meeting compliance is time consuming and can be costly—if requirements are not met. OPSWAT technologies provide comprehensive visibility, detailed reporting capabilities, and help meet requirements for PCI DSS, HIPPA, FINRA, HITECH, NIST, ISO, FTC, COBIT, Sarbanes-Oxley, CIS, and SANS. Learn how MetaAccess can meet the specific terms of the regulatory compliance in your industry.

Securely Work From Anywhere
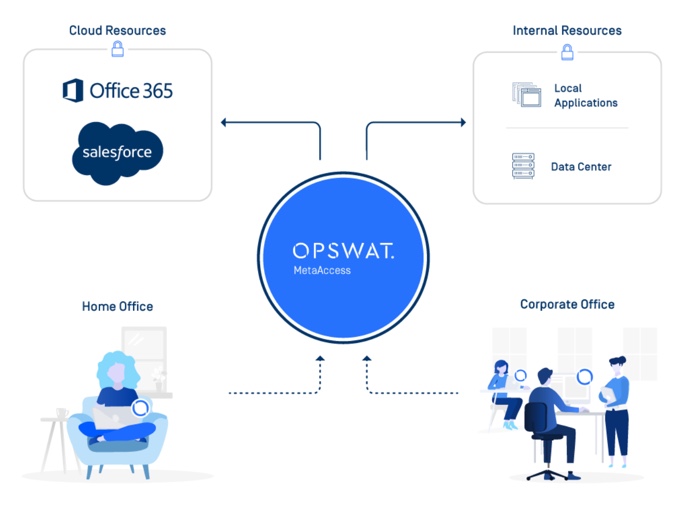
MetaAccess Enables Compliance and Secure Access
In today’s environment, it’s important to have the right security in place both for users accessing your network, data and applications from home or from the office. MetaAccess is one platform to give you just that: Industry leading compliance, security and vulnerability checks, a zero trust VPN alternative and on-premises network access control whether you are at home, the office, or remote locations, and whether your data and applications are on-premises or in the cloud.
Source : opswat.com
View more products : nessar.net