Supercharge Firewalls with intelligence through machine learning, built-in threat intelligence and integrated applications
Supercharge Firewallsa
Leverage existing Firewall investments to collect security data without deploying dedicated sensors
Apply Machine Learning to Firewall data in order to see any anomalies
Detect potential Firewall policy mis-configurations, compromised and malicious users and their abnormal traffic to/from the Internet
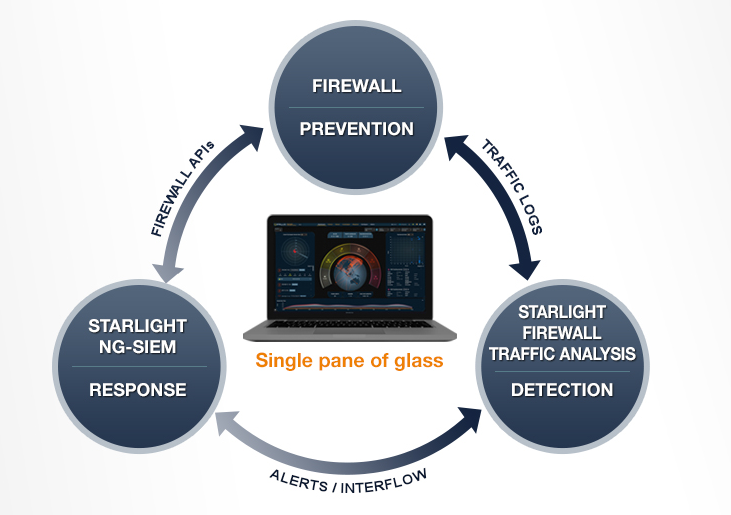
Firewall traffic logs are transformed into Interflow™ records through normalization and enrichment.
Fuse context with threat intelligence and reveal additional detection’s such as Geo Fencing or communication with known malicious actors
Cost-effectively store firewall traffic logs for forensics and threat hunting
Leverage closed-loop automated workflow to block attackers through Firewall APIs
Second set of eyes
Dedicated Stellar Cyber security sensors deployed behind the Firewall detect what’s missed
Deep packet inspection (DPI) engines integrated in these security sensors generates richer set of meta data
Detect potential Firewall policy misconfigurations
Integrated NTA and UBA detections also provide a rich workbench for security personnel
Detect DGA and DNS tunneling through machine learning and additional detection’s across the cyber kill chain, such as Ransomware
Leverage closed-loop automated workflow to block attackers through Firewall APIs
Key Features

Firewalls are for Enforcement
Firewalls are the first line of defense in any network security framework. The primary purpose is to inspect network traffic in real time and determine whether to allow or block specific traffic based on a set of security rules defined by administrators. The traffic volume can be significant and legacy Firewalls have limited resources in terms of processing power and storage size. Thus the Firewall has limited intelligence itself and it is usually optimized only for policy enforcement.
Firewall Traffic Analysis [FTA]
Starlight aggregates, parses and normalizes traffic log data from multiple Firewalls, which can be from different vendors such as Check Point, Palo Alto Networks, Fortinet, and Sophos. Interflow records create context for these logs by fusing together many other data sources like Threat Intelligence, Geolocations, host or domain names, and user names. Both real-time and historical advanced analysis of contextual data are performed through machine learning.
Starlight performs anomaly detection through machine learning including deep learning. Starlight can detect mis-configuration of Firewalls, which can be deadly. One reason that CapitalOne was hacked was because of Firewall misconfigurations. Starlight can expand Firewall rules into dimensions such as geo-location, reputation, hostnames, etc. besides IP address and user names.

Integrated SOAR
Starlight is a software application architected with container-based micro-services and a data lake for big data. It processes and stores large amount of Firewall logs turned Interflow records, and scales for more processing power and available storage capacity. Security analysts can perform Google like search on Interflow records for forensics and threat hunting. Respond to detected advanced threats by blocking attackers’ IP through API calls to Firewalls. These interactions can be done either manually or automatically.
Data-Driven Cyber Security Stellar Cyber’s Starlight detects cyber breaches across your entire network, regardless of scale or complexity. When Starlight is activated, it quickly establishes...
View more