NEWS
ActiveScale Object Storage
Durable, Secure, S3-Enabled Object Storage for Active Archiving and Long-Term Retention ActiveScale™ object storage provides a new, innovative approach to creating a simple, ‘always-on’ data...
View moreHillstone’s Standalone SD-WAN Solution
Hillstone’s Standalone SD-WAN Solution The latest Hillstone Security Management Platform (HSM) release, version 5.0, expands upon previous versions to provide the first dedicated SD-WAN controller, manager and...
View moreSenhasegura: The Pillars of Information Security – Part 2
The Pillars of Information Security – Part 2 Currently, the use of information is a great ally for companies from different industries. However, along with...
View moreIs your company really prepared for a cyber attack?
Is your company really prepared for a cyber attack? The rise of smart devices and shifting customer preferences have driven the global digital transformation at full steam....
View moreHillstone Security Management Platform
Accelerating Deployment Cycles. Reducing Management Overhead. Simplify Configuration. Hillstone’s Security Manager enhances network security by allowing businesses to segment their networks into multiple virtual domains....
View moreHillstone Security Audit Platform (HSA)
Transform Log Data into Security Intelligence ISPs, universities, large enterprises, government agencies, and large data centers generate millions of events everyday. They require high performance...
View moreHow To Identify Network Issues Hop-By-Hop
How To Identify Network Issues Hop-By-Hop First, let’s define the problem. As networks get bigger they get more complicated. A pretty straightforward statement, but why...
View moreWhat is a Sysadmin?
What is a Sysadmin? In a world of constantly evolving technology, SysAdmin is one of the oldest and most in-demand roles in the technology field. While not...
View moreHillstone ADC Solution
Application Availability and Protection with Built-In Scalability Hillstone’s Application Protection products include an advanced application delivery controller (ADC) that helps scale the performance of your...
View moreHillstone Server Protection Solution
Comprehensive Server Protection with Unparalleled Visibility and Efficacy Hillstone Server Breach Detection System (sBDS) I-Series product line detects and helps mitigate advanced multi-stage, multi-layer, threats...
View morePAM Market Trends According to Gartner
PAM Market Trends According to Gartner Protecting privileged credentials is essential in the cybersecurity strategies of companies of all sizes and verticals. According to Verizon...
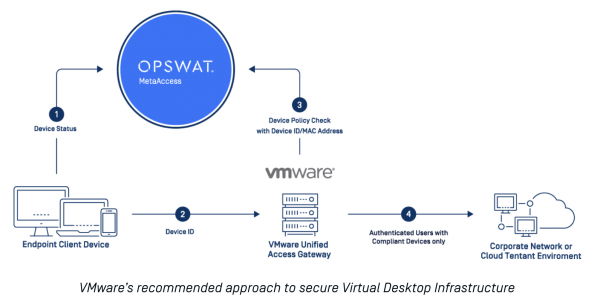
View moreOPSWAT Solutions now available in VMware Marketplace
OPSWAT Solutions now available in VMware Marketplace As a leading provider of security solutions protecting the world’s most critical infrastructure, OPSWAT has built a network...
View more