NEWS
Secure SD-WAN for distributed enterprises
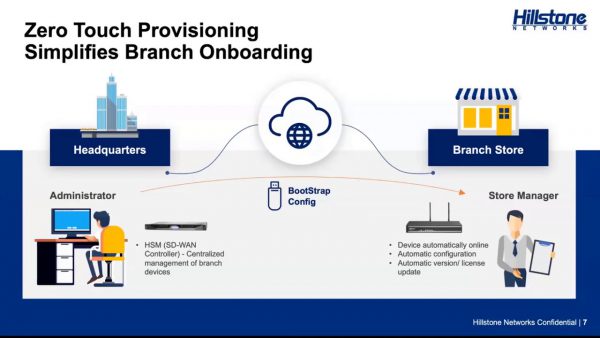
Secure SD-WAN for distributed enterprises Uncompromising Edge Security In a post-breach world, the network edge has become both an opportunity and a threat for IT...
View moreLet’s Get Braced For The “Next Normal
Networking Trends In 2021: Let’s Get Braced For The “Next Normal Over the last decade, we’ve seen some of the most significant disruptions in networking...
View moreThe Importance of Encryption for Cybersecurity
The Importance of Encryption for Cybersecurity Most people may find it difficult to understand the importance of encryption for cybersecurity, especially since both are designed to...
View moreFive Steps for Effective Monitoring of Network Traffic
Five Steps for Effective Monitoring of Network Traffic While this should come as no surprise, monitoring network traffic in large, enterprise-level organizations is quite different from...
View moreZECURION ANALYZE THIS
ANALYZE THIS Remote work taught us a lot about trust – occasionally with carrots, but often with sticks. Some people and teams are still productive,...
View moreHillstone’s Future-Ready NGFW Platform
Hillstone’s Future-Ready NGFW Platform The Hillstone A-Series next-generation firewall features high security performance, expansion as needed, complete advanced threat detection and prevention, and smart and...
View moreZECURION ENTERPRISE SECURITY MAGAZINE: SOLVED BY THE NEXT GENERATION DLP
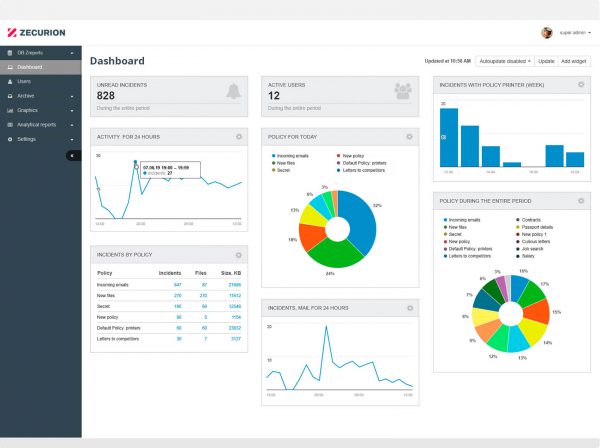
ENTERPRISE SECURITY MAGAZINE: TOP 4 PROBLEMS, SOLVED BY THE NEXT GENERATION DLP Article by Alexey Raevsky, Ph.D., MBA, CEO, and Co-Founder, Zecurion In 2021 we...
View moreZero Trust-Based Security Approaches
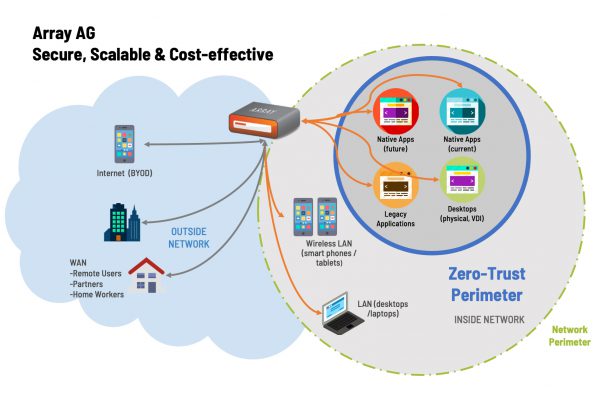
Zero Trust-Based Security Approaches In a world of complex cybersecurity threats and mobile workforces armed with multiple apps and devices, security in Zero Trust aims to provide...
View moreHow to Optimize Network Performance
How to Optimize Network Performance It goes without saying, but the network has grown increasingly complex within an incredibly short amount of time – and...
View moreThe Role of the Cloud in Accelerating Digital Transformation
The Role of the Cloud in Accelerating Digital Transformation Digital transformation continues to be a high priority this year. Remote work, eCommerce, digital collaboration, and...
View moreUnderstanding the Challenges, Risks and Best Practices for Securing APIs
Understanding the Challenges, Risks and Best Practices for Securing APIs Overview Most of today’s digital experiences are powered by APIs, however security remains a primary...
View moreHolm Security: 5 Steps to Successful Vulnerability Management
5 Steps to Successful Vulnerability Management Vulnerability Management is a cornerstone in a modern cyber security defense. But getting started and implementing a successful security...
View more