NEWS
What Is a Network Packet?
What Is a Network Packet? Everything flowing through a network can be classified as part of data enclosed in a packet. A network packet or IP packet...
View moreThe Past, Present, and Future of Pentesting
The Past, Present, and Future of Pentesting Pentesting, or penetration testing, is a cybersecurity measure that fights hackers by exposing the hacker’s possible entry points,...
View moreQuantum’s Portfolio for Managing Unstructured Data
Quantum’s Portfolio for Managing Unstructured Data This week, we made a significant announcement, introducing an expanded portfolio focused on classifying, managing, and protecting unstructured data...
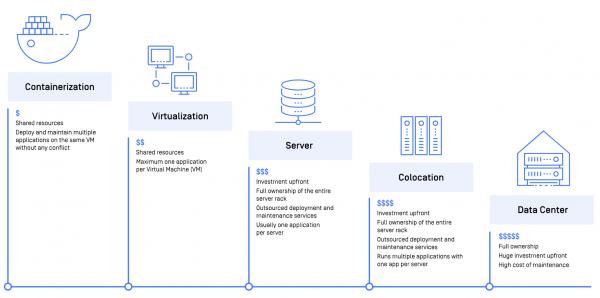
View moreEvolution of Infrastructure: From Data Centers to Containers
Evolution of Infrastructure: From Data Centers to Containers The impact of the digital transformation revolution requires organizations to look for more efficient solutions to manage,...
View moreHow to Measure Network Performance Effectively
How to Measure Network Performance Effectively To run an enterprise effectively today, a good chunk of the yearly budget will have to be directed towards...
View moreTypes of Network Monitoring Protocols
Types of Network Monitoring Protocols Corporate networks as a system are made up of numerous components, and it is not uncommon that some components due...
View moreApplication Delivery That’s Simple Yet Scalable & Powerful Yet Cost-Effective
Application Delivery That’s Simple Yet Scalable & Powerful Yet Cost-Effective Array APV Series application delivery controllers provide the availability, scalability, performance, security and control essential to keeping...
View moreHillstone Server Protection Solution
Comprehensive Server Protection with Unparalleled Visibility and Efficacy Hillstone Server Breach Detection System (sBDS) I-Series product line detects and helps mitigate advanced multi-stage, multi-layer, threats...
View moreTwin Mode HA for Redundant Data Centers
Full Security and Continuity for Intra-Data Center Traffic To support 24/7/365 application availability for enterprise operations, redundant data center design with application failover has become...
View moreProtecting Enterprise Datacenters
Protecting Enterprise Datacenters. Hillstone X-Series Data Center Firewall Solutions. Carrier-Class Infrastructure Protection for Data Centers Hillstone X-Series is a multi-tenant next-generation firewall (NGFW) for service...
View moreSignificant Enterprise Features Available in MetaDefender Cloud
Significant Enterprise Features Available in MetaDefender Cloud MetaDefender Cloud platform has been servicing large enterprises for tens of thousands of active users monthly. OPSWAT is...
View moreSecure SD-WAN for distributed enterprises
Secure SD-WAN for distributed enterprises Uncompromising Edge Security In a post-breach world, the network edge has become both an opportunity and a threat for IT...
View more