TECHNOLOGY NEWS
It’s official: Redis is the #1 AI agent data storage tool
Built for devs. Trusted by devs. The 2025 Stack Overflow Developer Survey is out, and devs worldwide have spoken. They named Redis the most-used data management tool...
View moreDemystifying Next-Gen WAF: Meaning, Benefits & More
Demystifying Next-Gen WAF: Meaning, Benefits & More With the proliferation of threat actors on the internet, enterprises must strengthen their security backbone to mitigate modern...
View moreVietnam Cyber Law Compliance Summit 2025: Reshaping Digital Security Strategy – Solutions from Nessar
Vietnam Cyber Law Compliance Summit 2025: Reshaping Digital Security Strategy – Solutions from Nessar In the era of booming digitalization, as cyber threats grow increasingly...
View moreSix ways privilege management improves your security posture
Six ways privilege management improves your security posture Identities, computers and groups all need access to resources. But only enough to fulfill a role, and...
View moreEnhancing Network Visibility at a leading American University
Enhancing Network Visibility at a leading American University Overview of the University The prestigious institution of higher learning ranks among the top 25 universities in...
View moreEnhancing security in critical and industrial OT networks with tapping and aggregation solutions
Enhancing security in critical and industrial OT networks with tapping and aggregation solutions Operational Technology (OT) encompasses the hardware and software systems vital for monitoring...
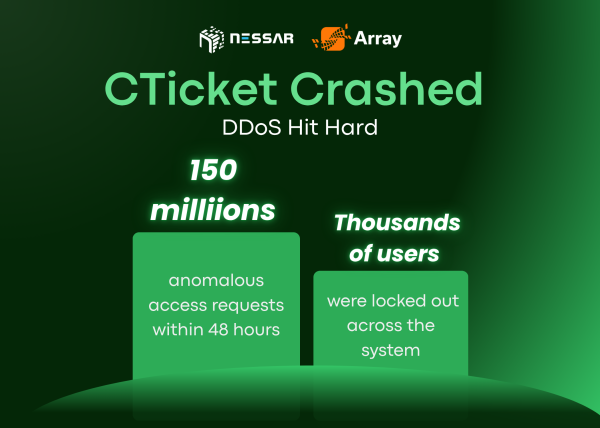
View moreWhen Clicks Turn into Chaos: Learning from the CTicket DDoS Ordeal
When Clicks Turn into Chaos: Learning from the CTicket DDoS Ordeal In today’s hyper-connected world, even a few minutes of downtime can translate into lost...
View moreNessar Showcases DevOps Data Platform from Perforce Delphix at Banking Roundtable on Digital Transformation
Nessar Showcases DevOps Data Platform from Perforce Delphix at Banking Roundtable on Digital Transformation On May 16, 2025, the Roundtable on “Applying AI in the...
View moreWhat is Data Masking?
Data masking protects sensitive information by replacing real data with realistic, fictitious values. It’s an essential technique for securing data, reducing breach risks, and meeting...
View moreWhat Is Network Security Management?
What Is Network Security Management? Network security management is the practice of keeping digital environments secure, running smoothly, and in compliance with industry regulations. It’s...
View moreWhy Stellar Cyber’s Open Cybersecurity Alliance Is a Game-Changer for MSSPs and Enterprises Alike
Why Stellar Cyber’s Open Cybersecurity Alliance Is a Game-Changer for MSSPs and Enterprises Alike The cybersecurity world has long struggled with a fundamental challenge: how...
View moreStellar Cyber unveils Human-Augmented Autonomous SOC Powered by Agentic AI
Stellar Cyber unveils Human-Augmented Autonomous SOC Powered by Agentic AI Organizations today are navigating an environment where threats are not only more frequent, but also...
View more