Cross-Domain Solutions
Create a data and device transfer process that delivers security and trust across the entire perimeter.
Cross-Domain Solutions Overview
How do you secure file transfers across the entire enterprise, especially with devices you don’t control? Transferring files into, across, and out of secure environments is problematic. Files entering via portable media and transient devices create opportunities for infection. Stored files may have zero-day attacks, temporarily unnoticed and dormant on servers. Allowing files to exit secure environments risks sensitive data leakage.
Cross-Domain Solution Benefits

Breach Prevention with Multiscanning
Malware continues to bypass existing defenses because cybercriminals develop threats with evolving sophistication, and enterprises deploy insufficient protection. Sensitive data can be stolen or transferred accidentally. OPSWAT safeguards sensitive data proactively at every transfer point.
Many security professionals allow files to enter a network after only a single anti-virus scan. To detect the latest threats, OPSWAT uses up to 30+ anti-malware engines.

Regulatory Compliance for NERC CIP, GDPR, and More
Regulatory compliance requirements are designed to minimize breaches and privacy violations. Meeting compliance is time consuming and can be costly if requirements are not met.
OPSWAT helps support compliant processes, comprehensive visibility, and detailed reporting to help meet requirements for NERC CIP 003-7, NEI 08-09, NIST 800-53, PCI DSS, GDPR, the Bulk Power Executive Order 13920, and a wide range of other global regulations.

Digital Perimeter Control with Automated Device Blocking
Perimeters can be virtual, physical, or mobile. OPSWAT securely controls the transfer of files and devices in between security levels, systems, and physical transfer points.
The global increase of remote employees, BYOD, and contractors has resulted in an exponential rise in unmanaged devices. Blindly connecting devices to an internal or cloud network exposes enterprises to significant risks. OPSWAT blocks untrusted devices from accessing physical and virtual environments until they are thoroughly inspected and remediated.
Secure File Transfer with Automated Media Blocking
Files risk infection, while in transit. OPSWAT enforces secure file transfer processes, continuously scan for malware, and add digital signatures to ensure file integrity.
Tools work most effectively when combined with informed decision-making. OPSWAT products instill simple, effective processes. Employees will know how to safely bring in, store, transfer, and extract data across the enterprise, while staying in compliance with security policies. If unsanctioned portable media is purposefully or accidentally brought into the environment, safeguard processes will block the media from accessing devices and networks.

How OPSWAT Can Help Manage Cross-Domain Security
OPSWAT offers several products to support a wide range of use cases and manage cross-domain security and compliance.
MetaDefender Kiosk
MetaDefender Kiosk acts as a digital security guard – inspecting all media for malware, vulnerabilities, and sensitive data. The Kiosk is designed for installation at the physical entry point of secure facilities.
MetaDefender Vault
MetaDefender Vault is a secure file storage and retrieval solution that protects critical files. The Vault works alongside the Kiosk to provide a secure and efficient way to manage threat protection.
MetaDefender Drive
MetaDefender Drive is a portable USB-based solution to inspect devices for malware, vulnerabilities and sensitive data before they enter or leave any organization. The Drive is designed for use where portability is valued and connection to an external network is not available.
OPSWAT Client
OPSWAT Client blocks all unauthorized removable media usage on all endpoints and scans them for malware before any files are copied over to the internal systems. The client can also enforce the usage of any media only processed and approved by MetaDefender Kiosk at the entry of your organization.
Central Management
Central Management offers a single pane of glass for globally managing multiple OPSWAT deployments, updating policies and settings, monitoring health of all instances in near real-time.
Cross-Domain Solution Deployment Scenarios
Standalone MetaDefender Kiosk
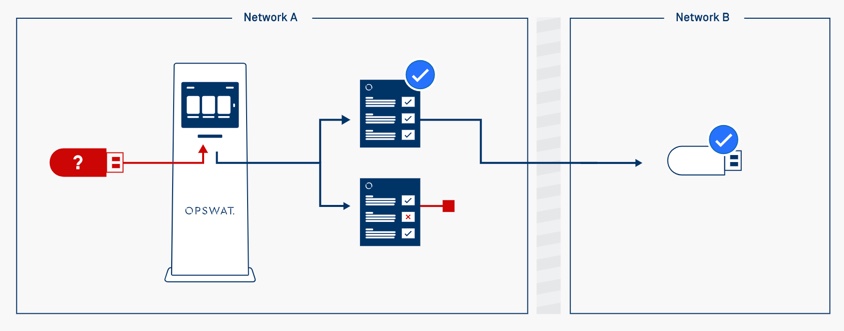
Removable media are allowed to be used inside the organization, however, must be processed by the MetaDefender Kiosk.
After user scans the content on the media, malicious files will be blocked/removed, sensitive data can be redacted and only verified files can remain on the media to be carried forward into the security areas.
MetaDefender Kiosk to MetaDefender Vault
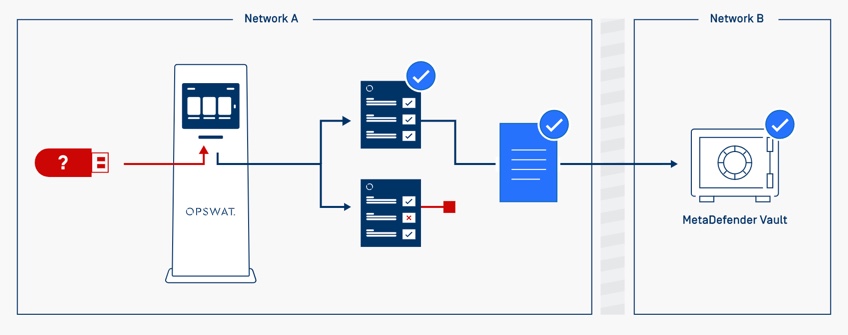
MetaDefender Kiosk is deployed on low security segments of the networks.
After user scans the content on the media, malicious files will be blocked/removed, sensitive data can be redacted and only verified files can be transferred to MetaDefender Vault, a secure storage product to store and enable the data download from the high security segments of the networks.
Optionally a data diode can be used to ensure one-way data transfer between the Kiosk and Vault. Users can retrieve approved files from MetaDefender Vault for maintaining a media-less environment of high security networks.
MetaDefender Kiosk to OPSWAT Client
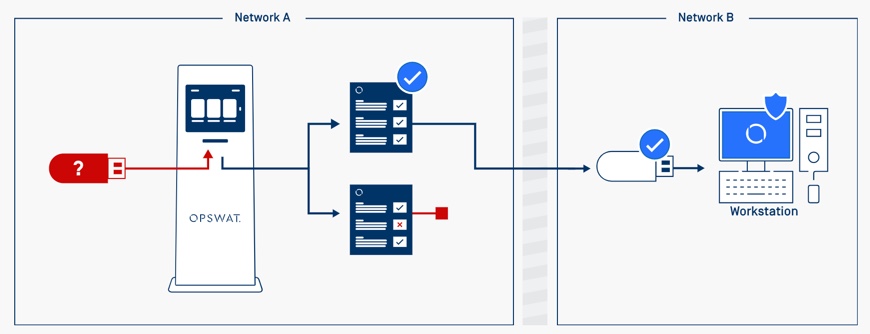
Removable media are allowed to be used inside the organization, however, they must be analyzed by the MetaDefender Kiosk and the usage enforced via an endpoint agent – the OPSWAT Client.
After user scans the content on the media, malicious files will be blocked/removed, sensitive data can be redacted, and only verified files can remain on the media to be carried forward into the secure areas. In case any unauthorized removable media is brought into the organization and inserted into devices that are protected by the OPSWAT Client, the unverified media will be blocked entirely.
MetaDefender Vault to MetaDefender Vault
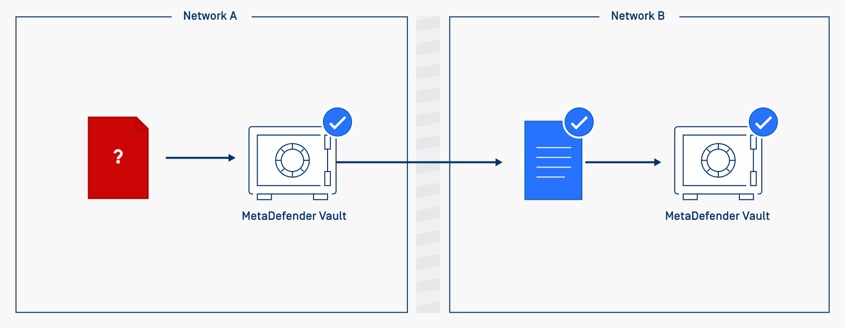
A MetaDefender Vault (the transferring side) is deployed in the low security segments of the networks. All users can use Web Browsers to visit the Vault landing page and login with credentials or a guest ID to upload files through the interface.
All content will then be scanned by MetaDefender Vault (the transferring side): malicious files will be blocked/removed, sensitive data can be redacted, and only verified files can be transferred to the other MetaDefender Vault (the receiving side), typically residing in the high security segments of the networks. Once the files are transferred, they can be continuously scanned for outbreaks before made available for download unless they are approved by supervisory controls.
MetaDefender Drive
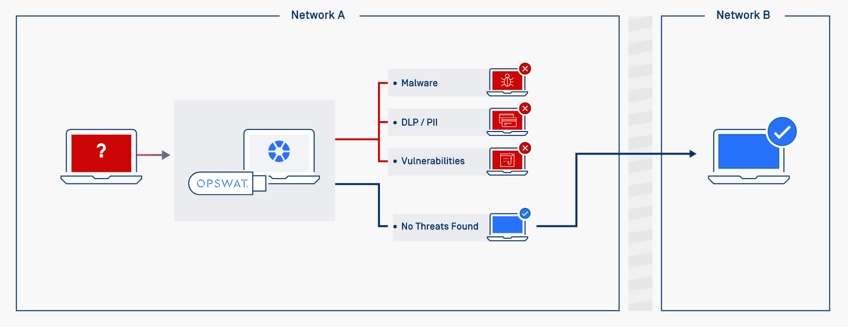
When any transient devices such as a loaner laptop, returned assets from existing employees, contractor machines, etc. come back to the high security networks, MetaDefender Drive can be used to scan the assets for risks of compromised malware, sensitive data loss, vulnerable binaries and installers, and applications developed by foreign adversaries.
After thorough inspection of the device, a detailed inspectionapproval report will summarize which assets may be allowed inside.
Source : opswat.com
View more products : nessar.net