Phishing simulation & awareness training
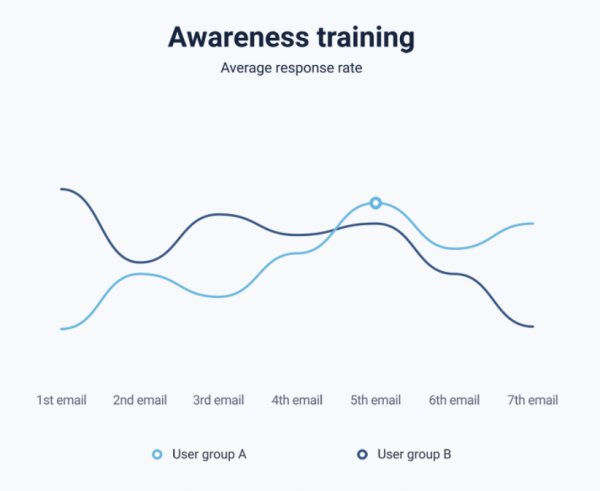
Phishing simulation & awareness training Over 90 % of data breaches start with a malicious email. Do you know how your users will respond to the next attack? Our product for phishing simulation and awareness training helps you increase resilience...
View moreWeb Application Scanning
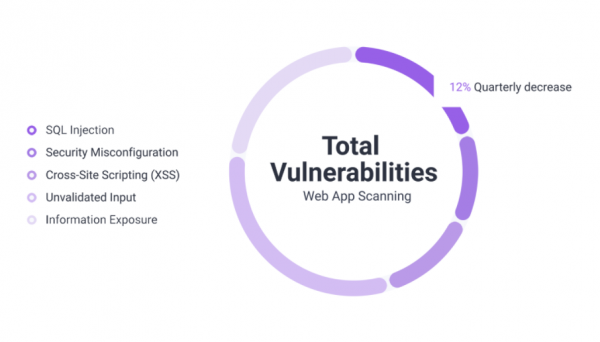
Web Application Scanning Gartner states that 75% of the attacks occur in the application layer, which makes web applications the most vulnerable layer in your...
View moreSystem And Network Scanning
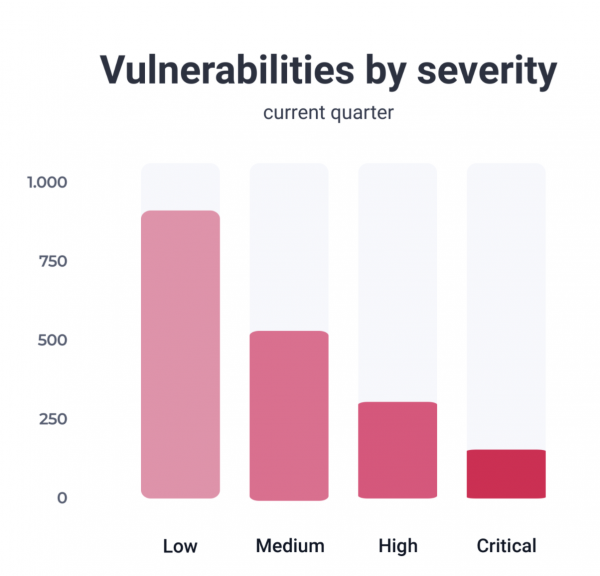
System And Network Scanning Our automated and continuous system and network scanner provides unparalleled coverage and comprehensive insight to enable you to detect vulnerabilities, assess...
View moreHolm Security: 5 Steps to Successful Vulnerability Management
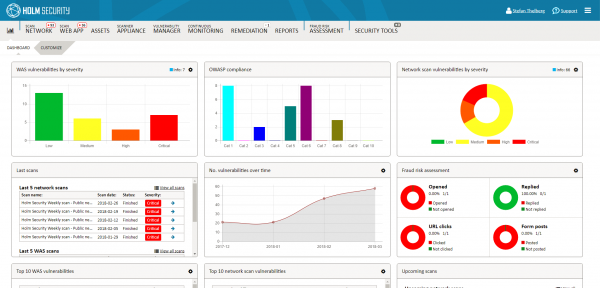
5 Steps to Successful Vulnerability Management Vulnerability Management is a cornerstone in a modern cyber security defense. But getting started and implementing a successful security...
View more