Công Ty Cổ Phần Công Nghệ Nessar Việt Nam - Nessar
- HOME
- ABOUT US
- SOLUTIONS
- ENTERPRISE SOLUTIONS
- SECURITY SOLUTIONS
- INDUSTRIES BASED SOLUTIONS
- VENDORS SOLUTIONS
- VENDORS
Web Application Scanning Gartner states that 75% of the attacks occur in the application layer, which makes web applications the most vulnerable layer in your IT environment. Our web application scanner automatically and continuously scans your web applications and APIs for an ever-increasing number of vulnerabilities. We find OWASP top 10 vulnerabilities, misconfigurations, weak passwords, […]
Web Application Scanning
Gartner states that 75% of the attacks occur in the application layer, which makes web applications the most vulnerable layer in your IT environment. Our web application scanner automatically and continuously scans your web applications and APIs for an ever-increasing number of vulnerabilities. We find OWASP top 10 vulnerabilities, misconfigurations, weak passwords, and exposed system information and personal data – in all types of applications.
Just in a month, there are thousands of new known vulnerabilities. Scheduled and continuous scans find new vulnerabilities fast.
Don’t get lost by all the data. Our platform helps you understand what vulnerabilities to remediate first through a number of automated and simple tools.
Our platform provides a great foundation for systematic and risk-based work with your cyber security defense.
We cover every type of web application, public as well as local. Intranets, commercial websites, portals, and more.
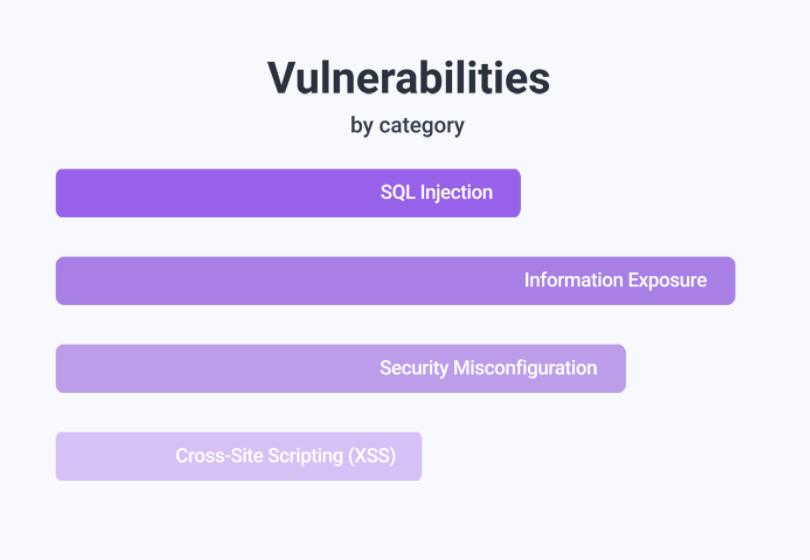
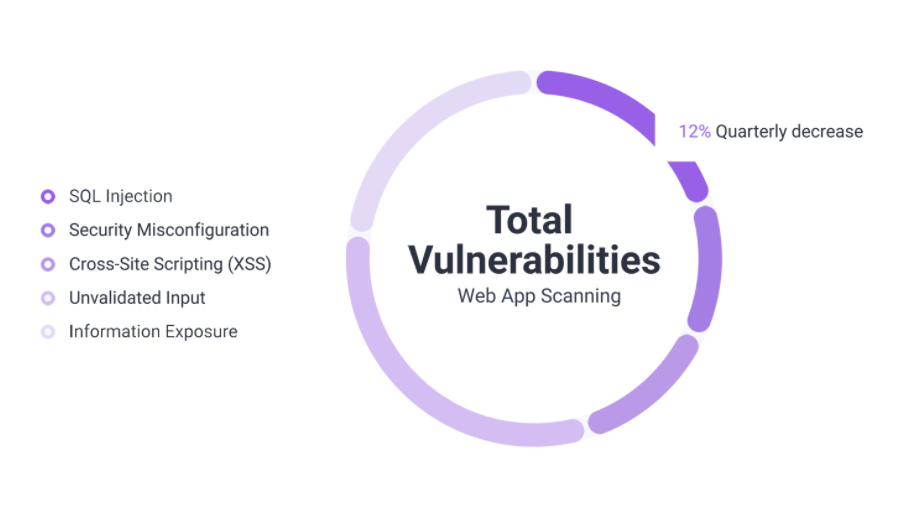
Along with the growing threat picture there are new legal requirements, standards and certifications. We help you meet existing and future requirements.
Our web application scanner finds a wide range of vulnerabilities in your web applications.

Safe and secure management and storage in the cloud. Select what physical datacenter that suits you. Get started in just minutes.
Installed and operating within your own infrastructure, with local data storage. Automatic software and vulnerability test updates.
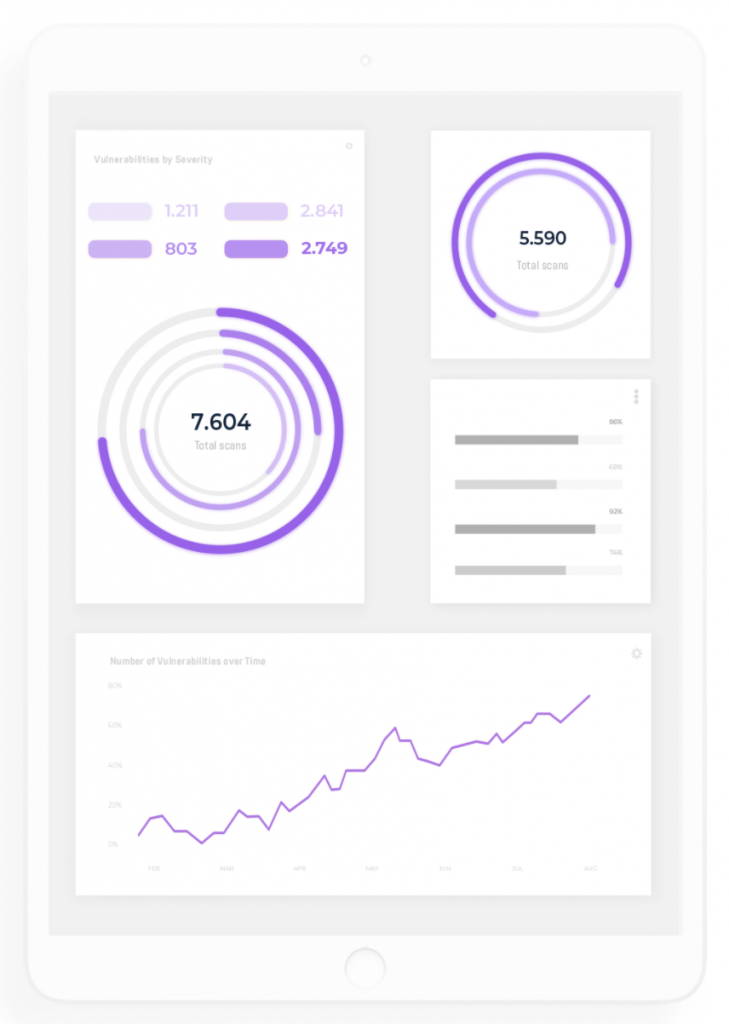
Security Center is our easy-to-use web-based control panel that gives comprehensive insights and helps you manage vulnerabilities. Through flexible dashboards and reports, you get a visual overview of current data, development over time, and more. Security Center supports Role-Based Access Control (RBAC).
Organizer enables different people, groups of users, departments, or countries to be given isolated access to relevant vulnerability data while maintaining a centralized administration. Get the best of two worlds – decentralized management to engage your teams, while still having support for centralized management.
