Công Ty Cổ Phần Công Nghệ Nessar Việt Nam - Nessar
- HOME
- ABOUT US
- SOLUTIONS
- ENTERPRISE SOLUTIONS
- SECURITY SOLUTIONS
- INDUSTRIES BASED SOLUTIONS
- VENDORS SOLUTIONS
- VENDORS
10 Key RidgeBot Features Learn how enterprise customers achieve Risk-Based Vulnerability Management using RidgeBot’s automated penetration testing technology. These 10 key RidgeBot features provide an overview showing the RidgeBot in action. We recommend a product demonstration where you can ask questions specific to your environment and security concerns. Attack Topology Auto-Drawing Visualized attack topology and attack […]
Learn how enterprise customers achieve Risk-Based Vulnerability Management using RidgeBot’s automated penetration testing technology. These 10 key RidgeBot features provide an overview showing the RidgeBot in action. We recommend a product demonstration where you can ask questions specific to your environment and security concerns.
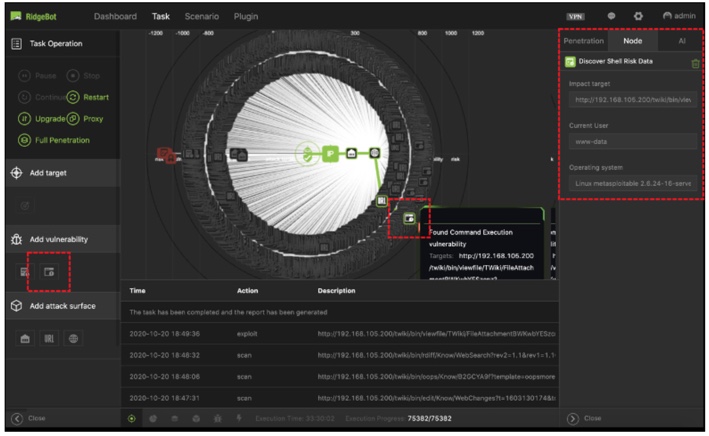
Visualized attack topology and attack path:
Drill down to the Risk to see the detailed attack path of each attack
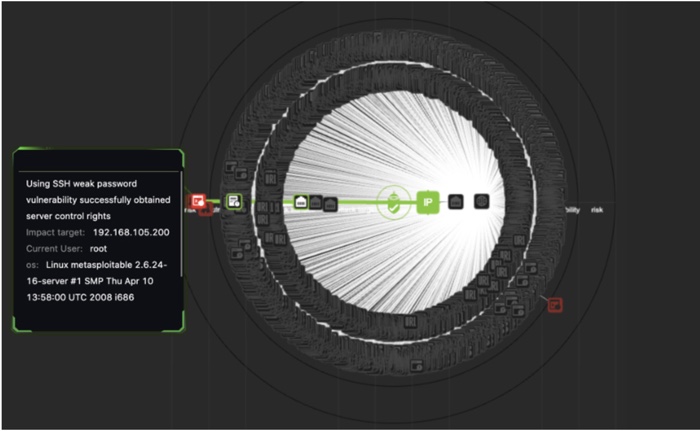
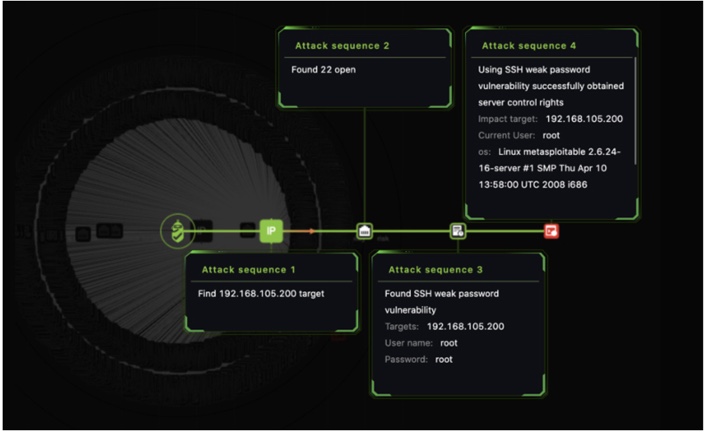
Visualized the process of how a vulnerability is discovered and exploited
Five Layers of attack information:
.
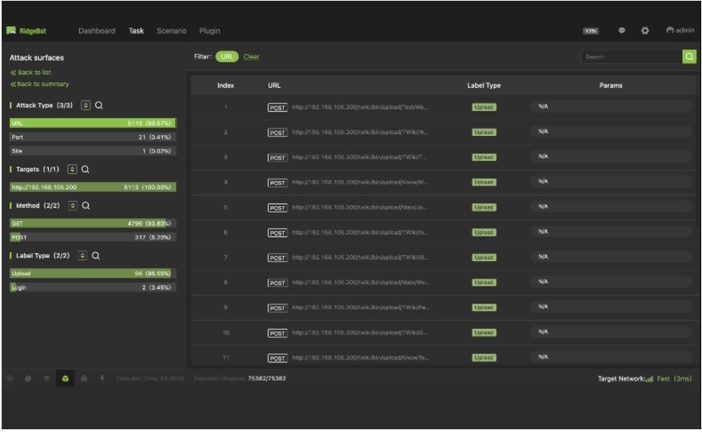
Discover the attack surface for the targets and identify its attack mechanism details in the following categories:
Show the details of each vulnerability including:
Attack snapshot:
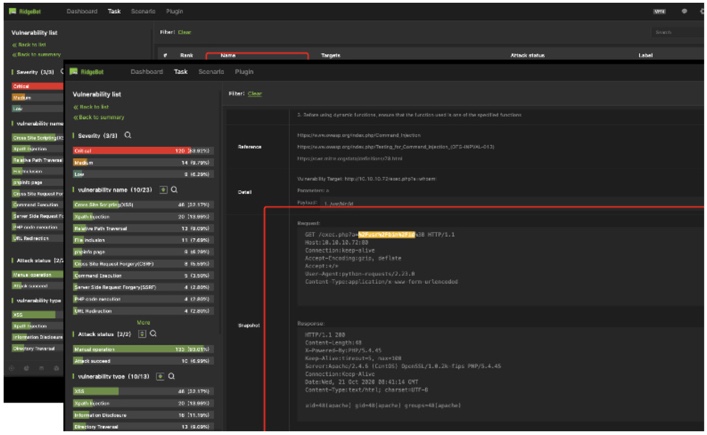
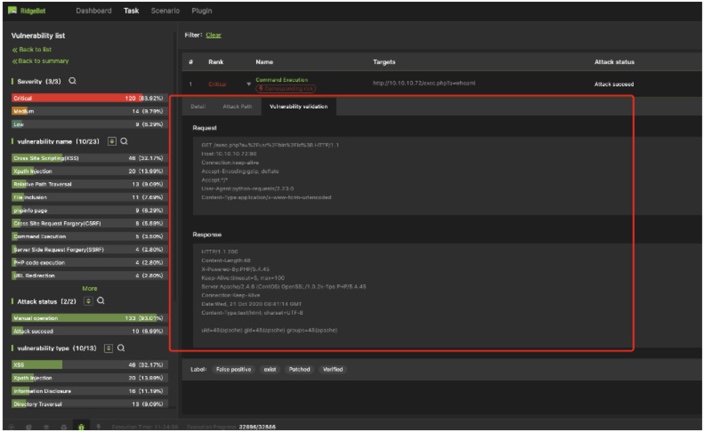
Vulnerability validation is to exploit the vulnerability to validate its existence.
HTTP reload is a typical validation method, its goal is to reload the HTTP request and get the result leveraging the vulnerability
Risk is the result of the vulnerability exploitation and defined as an exploit that accomplishes the whole kill-chain.
RidgeBot 3.1 supports 4-type of risks:
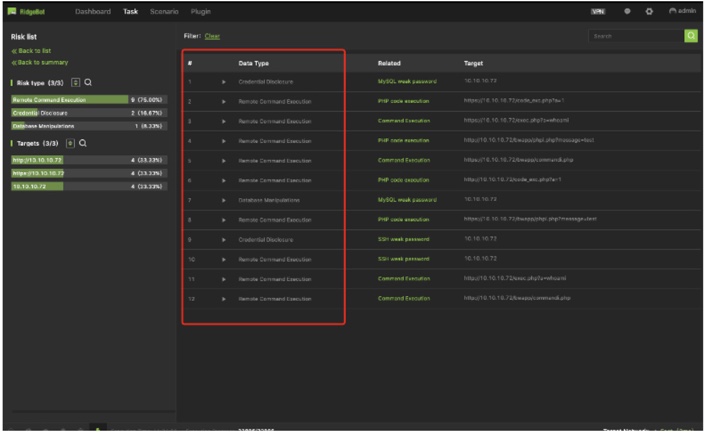
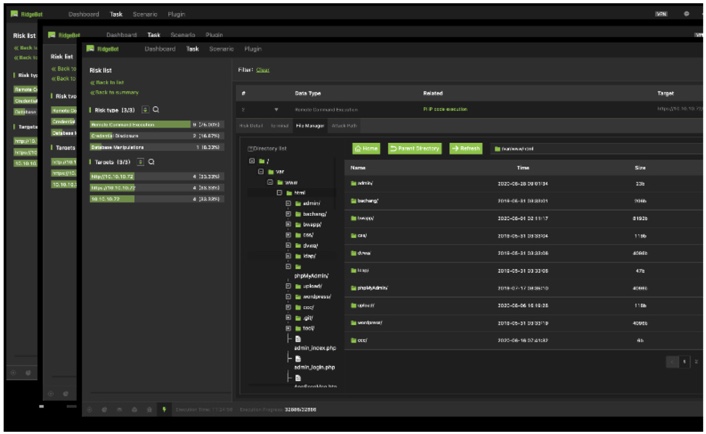
Details of Remote Command Execution risk
Details of Database manipulations risk
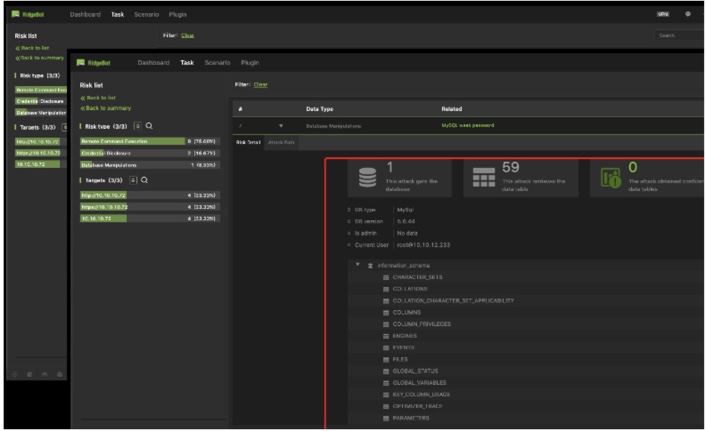
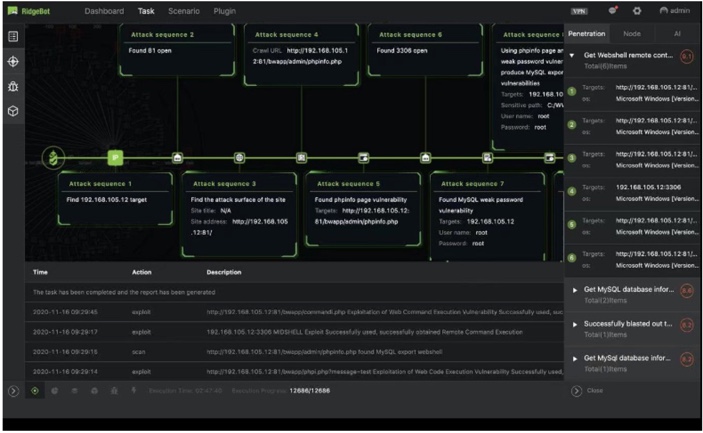
Jointly exploit the vulnerabilities to find more risks
The iterative attack/exploitation
Dynamic Task Configuration
Dynamically update the attack tasks during a test