Công Ty Cổ Phần Công Nghệ Nessar Việt Nam - Nessar
- HOME
- ABOUT US
- SOLUTIONS
- ENTERPRISE SOLUTIONS
- SECURITY SOLUTIONS
- INDUSTRIES BASED SOLUTIONS
- VENDORS SOLUTIONS
- VENDORS
ENDPOINT DETECTION & RESPONSE Endpoint Monitoring Benefits Continuous real-time visibility of your endpoints with detection & response. Your IT team wil be able to identify attacks with the accurate root-cause analysis for effective remediation intelligence. Actionable Intelligence for Endpoint Remediation Reporting to Reduce Total Number of Incidents Alerts to Quickly Find Solution to Incidents Lightweight […]
Continuous real-time visibility of your endpoints with detection & response. Your IT team wil be able to identify attacks with the accurate root-cause analysis for effective remediation intelligence.
Actionable Intelligence for Endpoint Remediation
Reporting to Reduce Total Number of Incidents
Alerts to Quickly Find Solution to Incidents
Lightweight Agent with Cloud Delivered Updates
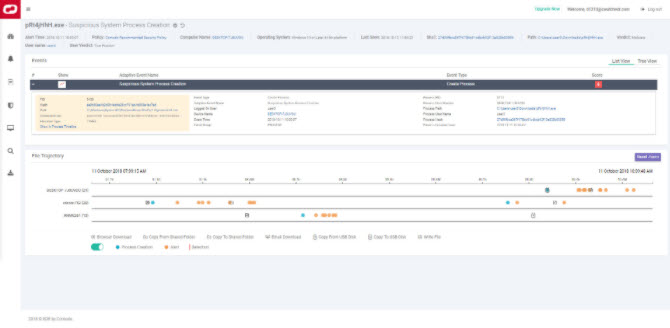
Proven to be the best way to convey this type of information, provide more than just data, they offer actionable knowledge.
FORECAST DETECTION
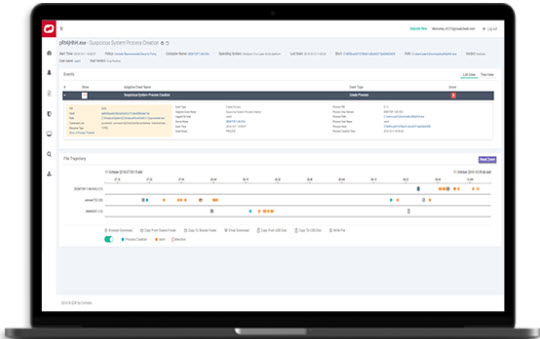
EDR FORECAST ANALYSIS
TIMELINE RESPONSE
SUSPICIOUS ACTIVITY VALIDATION
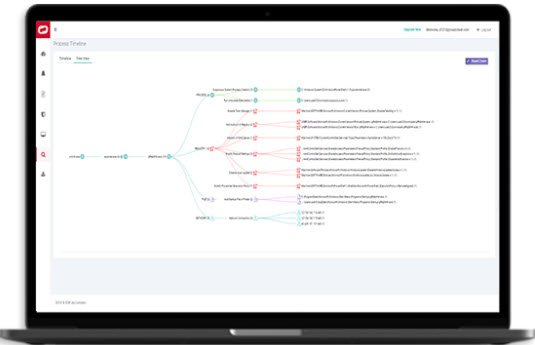
SEE THE CHAIN TO GET ACTIONABLE INTEL

WHY CHOOSE OUR
You get detailed file and device trajectory information and can navigate
single events to uncover a larger issue that may be compromising your system.
Early warning, detection and post-detection visualization
Tracks malicious processes taking place on your endpoints
Forward traffic using our intuitive agent
Apply our security policy based on threat behavior analytics
Set Email and SMS notifications to reduce reaction time
Verdict 100% of unknown executables on all files
Integrate with a SIEM to expand into more advanced security
Detect 100% of unknown fileless threats
Signatures updated automatically without interruption
24 hr expert analysis of more sophisticated threats
Source: comodo.com
View other products: Nessar.net
