https://youtu.be/DzYvgEPqKCY Ridge Security Automated Penetration Testing Solution Delivers Advanced Post-Exploitation Techniques Ridge Security helps you stay on the front lines of cyber defense with advanced tools in latest release of RidgeBot® Ridge Security, cutting-edge automated penetration testing solution provider, announces new capabilities in RidgeBot® 3.4, for post-exploitation validation. This new release further differentiates RidgeBot® from […]
Ridge Security Automated Penetration Testing Solution Delivers Advanced Post-Exploitation Techniques
Ridge Security helps you stay on the front lines of cyber defense with advanced tools in latest release of RidgeBot®
Ridge Security, cutting-edge automated penetration testing solution provider, announces new capabilities in RidgeBot® 3.4, for post-exploitation validation. This new release further differentiates RidgeBot® from vulnerability scanners and 1-step auto-exploitation tools that are currently available and strengthens RidgeBot®’s position as a true risk-based vulnerability management platform.
Post-exploitation operations are advanced hacking techniques, often utilized by an APT (Advanced Persistent Threat) attacks, including the notorious DarkSide hacker group that recently targeted the Colonial Pipeline. Post-exploitation refers to the phase of operation after a victim’s system has been compromised by the attacker. After gaining an initial foothold in the network, the attacker collects information about the environment and the organization, exfiltrates the data and pivots from the compromised target to further penetrate deeper into the internal networks.
In this release, RidgeBot® performs post-exploitation tactics by using privilege escalation and implanting a Botlet on the compromised system. This Botlet will act as a pivot to further penetrate the servers in the same class C IP network segment or across network segments if the victim machine has dual-network cards.
RidgeBot®’s post-exploitation capability delivers massive benefits to the organization, allowing them to:
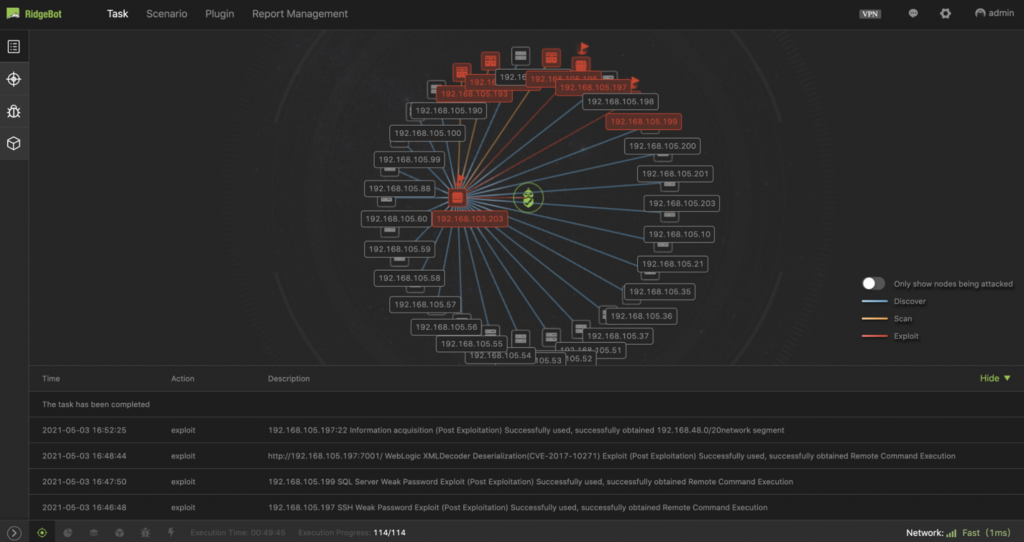
Figure 1. This node view shows that RidgeBot® is making lateral movement from network segment 103 to 105.
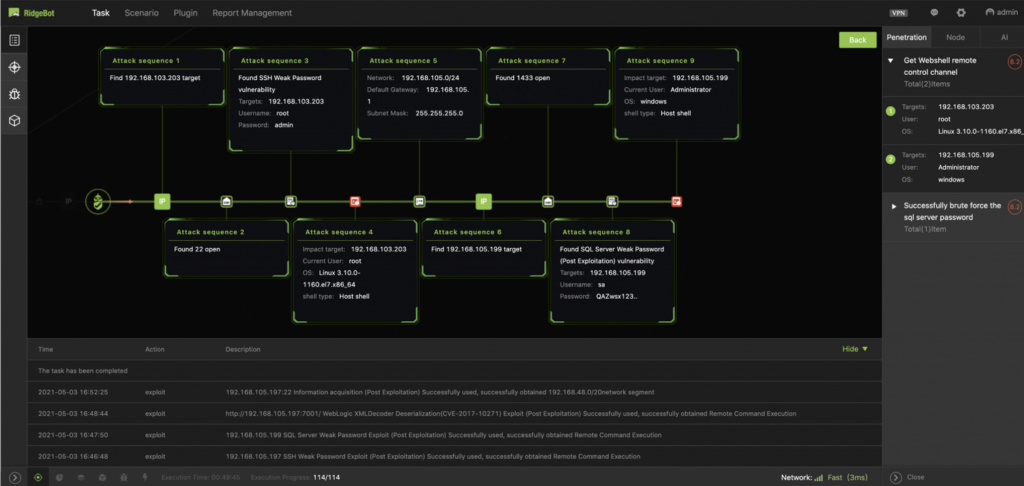
Figure 2. The attack sequences illustrate the RidgeBot®’s kill chain actions.
RidgeBot® couples ethical hacking techniques with AI-driven, decision-making algorithms to help identify and validate weak credentials and frequently exploited vulnerabilities, to minimize damage from simple or sophisticated, extortion-encryption attacks such as ransomware attacks.
