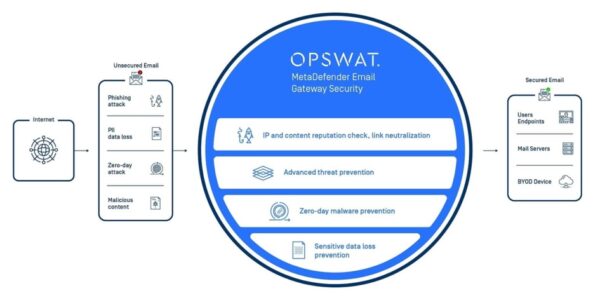
Network Access Control
Get real-time network visibility and prevent risky BYOD, IOT, and other devices from accessing network resources.
Why you should deploy Network Access Control?
With the increasing number and type of devices accessing your network, it is important to provide visibility of all devices and where they are on the network. This prevents non-compliant or risky devices from accessing your network or applications. NAC solutions enable complete policy and device life cycle management.
What happens if I do not deploy a Network Access Control solution?
Without a NAC, it’s difficult to have confidence that you know everything on your network, can block unauthorized access, and all devices are secure. It’s also much more challenging to demonstrate compliance with internal policies and external regulations.
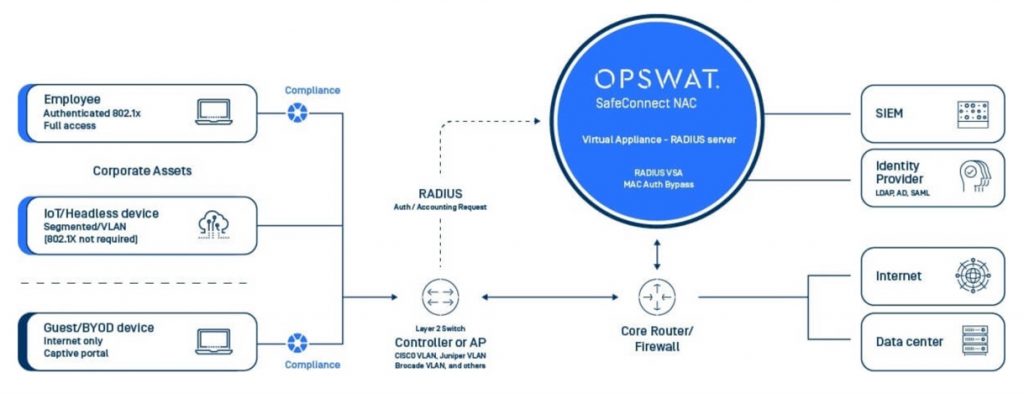
How Network Access Control Works?
Device profiling and visibility
Discover user and IoT (Internet of Things) devices as they attempt to access the network. Devices can be profiled in a passive manner or quarantined until the device is explicitly known using rich patterns and advanced heuristics.
Deep endpoint compliance and real-time posture check
Ensure every device is compliant with a wide range of policies. Integrates with OPSWAT OESIS technology, which is the most widely used technology for checking device security and compliance in the industry.
Seamless Integration
Leverage device information, including user ID, IP and MAC addresses, role, location, time and ownership of the device. This information is called Contextual Intelligence and can be published to many security solutions, such as firewalls and Security Incident and Event Monitoring systems (SIEMs).
Guest and BYOD Networking access
Control access for any type of device (BYOD, managed devices, IOT devices). The captive portal allows different authorization and access levels based upon user groups, including guests.
Incidence response
Take in threat information from an IDS/IPS and act on severe threats to block compromised devices instantaneously.
Trusted by Organizations Worldwide

Network Access Control Use Cases
BYOD Security
Our NAC solution protects your organization from risks associated with BYOD devices where we offer a broad support for BYOD operating system and robust yet fast compliance malware and vulnerability check and network segmentations, solving what can be a difficult management issue for many organizations.
Regulatory Compliance
The core of regulatory compliance standards revolves around knowing who, what, when and where for devices and users on your network and controlling access to the data your company needs to keep secure. NAC addresses security specifications in GDPR, HIPAA, PCI DSS, GLBA, SOX and more.
Guest Security
We enable you to provide Guests with restricted network access and different authorizations and access levels for guests and 3rd party contractors.
Security Platform Integration
NAC solutions can share information such as user identity, role, device type location and ownership with other security solutions to strengthen your overall security and compliance.
IOT Security
We detect and Identify any IOT devices on your network, categorize the devices, and place them into separate security domains to either allow or block access manually or automatically.
Network Access Control Benefits

Ultimate Visibility
Complete visibility to every device on your network. OPSWAT gathers information from multiple sources including LDAP/Active Directory, RADIUS Accounting, DHCP, NetFlow and SFlow to supply not only the IP Address, MAC Address, User ID and Role, but also Device Type, Location and Time of Access, Ownership and compliance. This strong visibility enables authentication to ensure only approved resources can access the network.

Deep Real-Time Compliance Check
Perform posture assessments of the device both pre-admission and post-admission through continuous checking. This capability can check registry entries, executables, applications and more to ensure your organization is compliant. It ensure compliance powered by OPSWAT Access Control Certification program and including endpoint vulnerability assessments, and advanced malware detection.
Simplified Installation and Ongoing Maintenance
Unique to SafeConnect is the capability for remote managed services, with a time proven five-step process to ease the implementation. Ongoing support is available 24/7 with pro-active monitoring, enabling support to immediately engage if there is an issue. Configuration back-ups and new device types are updated nightly. Updates are included and auto installed. Experience the freedom and peace of mind with this solution.