STELLAR CYBER SOLUTIONS
STELLAR CYBER SOLUTIONS
Entity Behavior Analytics (EBA) Application
Stellar Cyber’s Open XDR provides a single unified view, automatically and constantly discovering new assets, identifying their behavior and risk Comprehensive Inventory Dynamically discover assets...
View moreNext Gen SIEM Application
Unlike legacy SIEM, Starlight leverages advanced techniques like machine learning for detection of unknown threats and abnormal behaviors without any rules or signatures
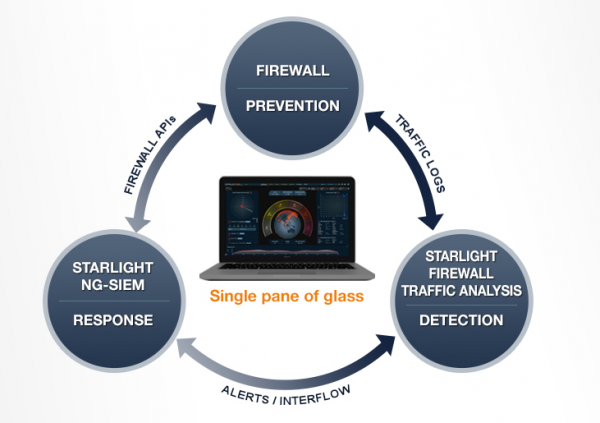
View moreFirewall Traffic Analysis (FTA) Application
Starlight aggregates, parses and normalizes traffic log data from multiple Firewalls, which can be from different vendors such as Check Point, Palo Alto Networks, Fortinet,...
View moreStellar Cyber for MSSPs
Stellar Cyber for MSSPs Multi-Tenancy The industry’s first multi-tenant, AI-driven breach detection platform for MSSPs AI-Driven Multi-tenancy for MSSPs Do you have enough security analysts...
View moreStellar Cyber For SIEM
Stellar Cyber For SIEM With Starlight for SIEM, you can gain more visibility and utility out of SIEM investments Data Pre-Processor forLegacy SIEMs Is your...
View moreStellar Cyber For Private Cloud
Stellar Cyber For Virtualized Environments Lightweight application that consumes less than 5% of the environments total resources Stellar Cyber For Virtualized Environments Virtual environments have...
View moreStellar Cyber For Public Clouds
Stellar Cyber For Public Clouds AI-Driven Security for Public Clouds Do you know if your cloud servers are being attacked? With public cloud services...
View moreStellar Cyber For Containers
Stellar Cyber For Containers The industries first AI-Driven Breach Detection System for container workloads AI-Driven Security For Containers Container deployment is gaining popularity and according...
View more