admin.nessar
Quantum Solutions for Life Sciences
Simplifying Petabyte-Scale Data Growth Advances in genomics sequencing, microscopy, and bioinformatics have made it possible for researchers to leverage data sets to develop vaccines, find...
View moreHow to View Sites, Devices, and Interfaces in LiveNX
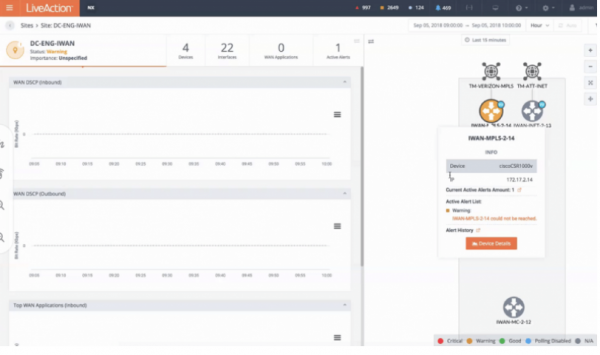
How to View Sites, Devices, and Interfaces in LiveNX As the network grows more complex, it becomes clear that proper network monitoring software is...
View moreDigital Sovereignty: The Precepts of Senhasegura According to an American Periodical
Digital Sovereignty The Precepts of Senhasegura According to an American Periodical Nomenclatures and acronyms are part of the routine of those who work in...
View moreWhy is Data the New Oil?
Why is Data the New Oil? Performing any task today is much easier than it was a few years ago. With the evolution of...
View moreOperating System Fingerprint Recognition – Server Message Block (SMB)
Operating System Fingerprint Recognition – Server Message Block (SMB) Whether you conduct penetration testing an automated vulnerability scanning, knowing your target is the very...
View moreWhy is Information Security Important to Your Organization?
Why is Information Security Important to Your Organization? As technology becomes increasingly sophisticated, criminals’ skills often evolve as well, in many cases surpassing the...
View moreProtect and Retain Data at Scale
Reduce Data Protection Cost by Over 50% File-based storage systems, such as scale-out NAS, have become more sophisticated, storing and delivering data to applications and...
View moreIs your company really prepared for a cyber attack? – Part 2
Is your company really prepared for a cyber attack? – Part 2 In the previous article, we discussed the importance of digital transformation to...
View moreBuild Your Own Network Performance Dashboard
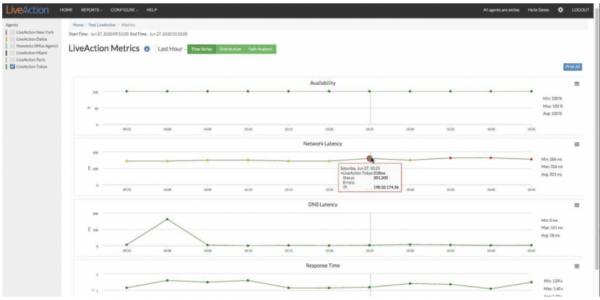
Build Your Own Network Performance Dashboard A network monitoring dashboard is one of the most important features within an all-inclusive network monitoring solution. A dashboard is...
View moreRansomware Recovery
The Relentless Onslaught of Ransomware Attacks are now occurring every 11 seconds, and demand for payments continue their upward trend with backup environments becoming a...
View moreSolutions for Big Data in Manufacturing
Why Manufacturers Need a Big Data Solution High-tech manufacturers are constantly looking for ways to increase efficiency, reduce costs, and streamline productivity, and their data...
View moreProtect and preserve your critical data ON QUANTUM
Ensure the Availability of Your Production Data with Efficient Backup, Recovery, and Archive Solutions from Quantum The requirements for protecting data across the Enterprise continue...
View more