OWASP Top 10 Compliance with RidgeBot 3.6
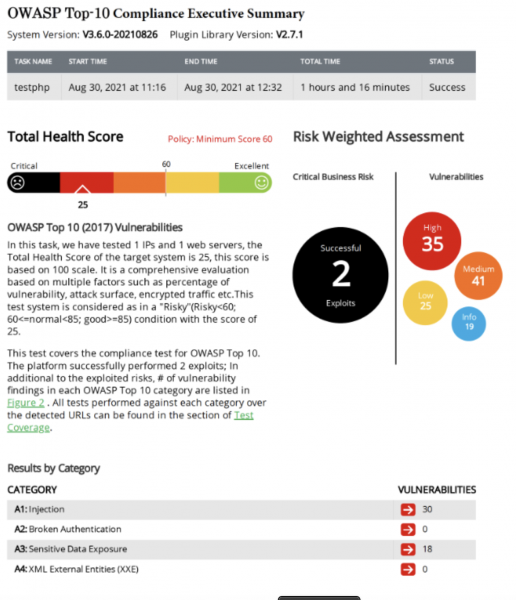
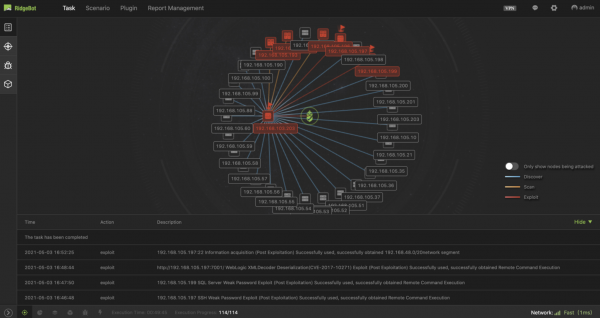
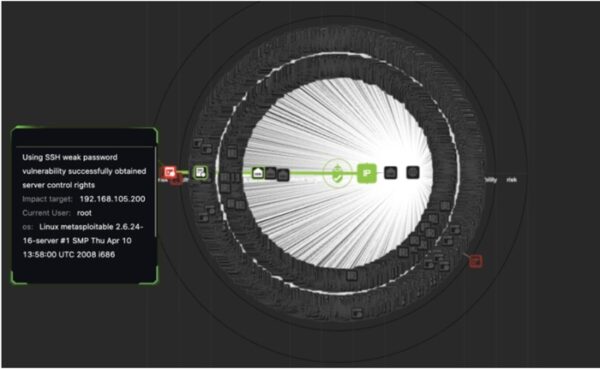
OWASP Top 10 Compliance with RidgeBot 3.6 What is OWASP Top 10? Security breaches and attacks have become so prevalent that only the very...
View moreRidge Security Automated Penetration Testing Solution Delivers Advanced Post-Exploitation Techniques
https://youtu.be/DzYvgEPqKCY Ridge Security Automated Penetration Testing Solution Delivers Advanced Post-Exploitation Techniques Ridge Security helps you stay on the front lines of cyber defense with...
View more10 Key RidgeBot Features
10 Key RidgeBot Features Learn how enterprise customers achieve Risk-Based Vulnerability Management using RidgeBot’s automated penetration testing technology. These 10 key RidgeBot features provide...
View moreWhat is the right way to detect OS by using SMB?
What is the right way to detect OS by using SMB? After studying different vendors’ approaches, here is our summary of how to do...
View moreHow to Use Microsoft SMB for OS Detection
The Study of Different Approaches from 4 Well-Known Vendors You may wonder “how does a blackbox penetration test tool know about my server information...
View moreOperating System Fingerprint Recognition – Server Message Block (SMB)
Operating System Fingerprint Recognition – Server Message Block (SMB) Whether you conduct penetration testing an automated vulnerability scanning, knowing your target is the very...
View moreRidgesecurity: Stop HelloKitty and PrintNightmare with RidgeBot
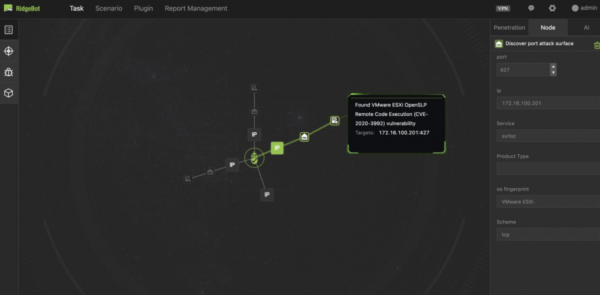
Stop HelloKitty and PrintNightmare with RidgeBot In the cyberworld, HelloKitty is not a cute kitten. And PrintNightmare is an actual nightmare. HelloKitty is a ransomware group who used CVE-2020-3992 to exploit...
View moreRecently discovered Zimbra vulnerabilities may have compromised 200,000 companies
Recently discovered Zimbra vulnerabilities may have compromised 200,000 companies Zimbra, an open-source collaborative office suite, consisting of webmail, web...
View moreRidge Security Announces Expanded Core Capabilities in RidgeBot with Enhanced Web Application Testing
Ridge Security Announces Expanded Core Capabilities in RidgeBot with Enhanced Web Application Testing From network, to host, to web applications, RidgeBot 3.5 delivers the most...
View moreThe Past, Present, and Future of Pentesting
The Past, Present, and Future of Pentesting Pentesting, or penetration testing, is a cybersecurity measure that fights hackers by exposing the hacker’s possible entry points,...
View moreUnderstanding the Challenges, Risks and Best Practices for Securing APIs
Understanding the Challenges, Risks and Best Practices for Securing APIs Overview Most of today’s digital experiences are powered by APIs, however security remains a primary...
View more