Category: VENDORSNEWSRidge Security News

In the cyberworld, HelloKitty is not a cute kitten. And PrintNightmare is an actual nightmare.
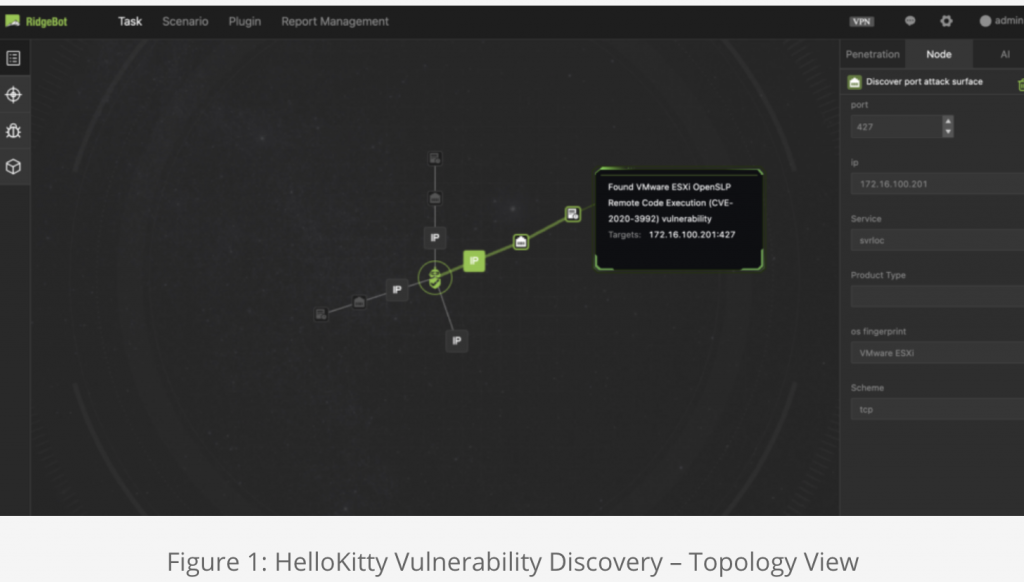
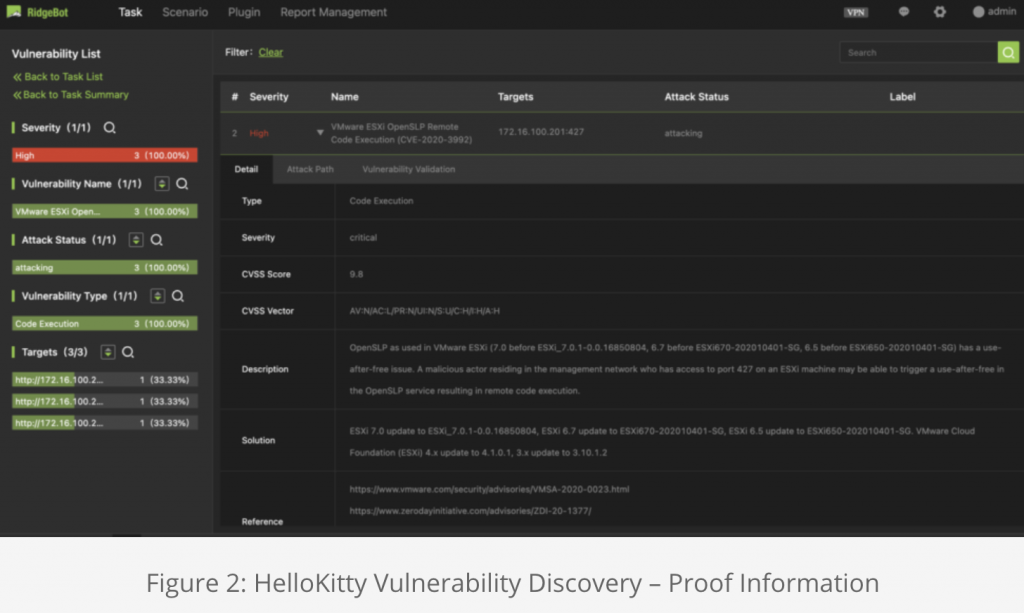
HelloKitty is a ransomware group who used CVE-2020-3992 to exploit networks and launch ransomware attacks against VMware ESXi servers. Due to the wide deployment of ESXi in enterprise networks, the number of high-profile cases has been increasing since last month.
With the vulnerability in CVE-2020-3992, an attacker can use port 427 to access and exploit ESXi servers by running esxcli commands to stop virtual machine (VM) processes and start encrypting the virtual machine files. The name comes from the infamous case HelloKitty, where CDProjekt Red, the Poland based popular video game development firm was hacked collectively by the group. The hacker group successfully accessed source code for video game projects that were in development, as well as encrypted devices.
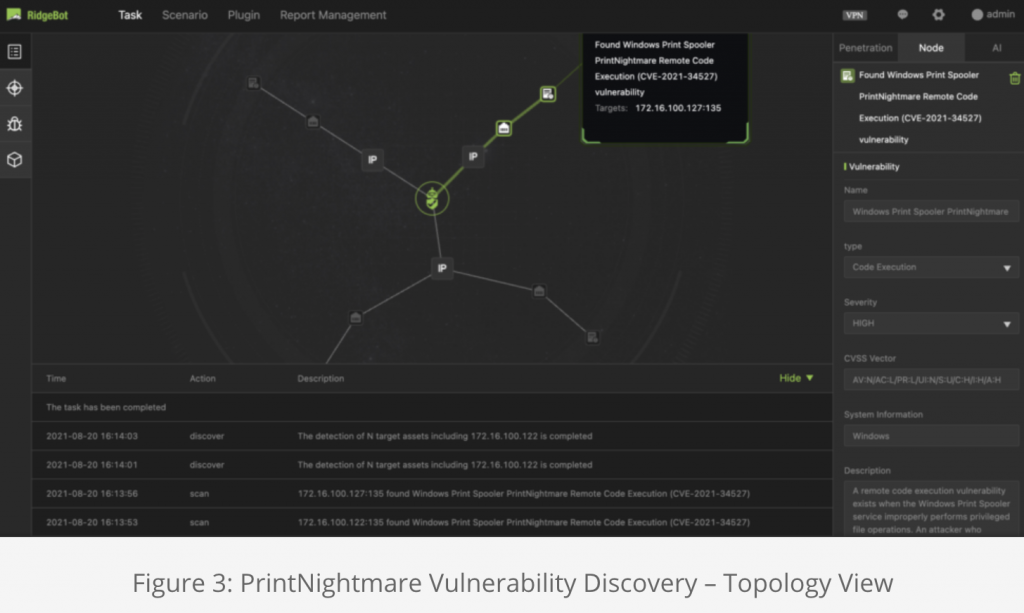
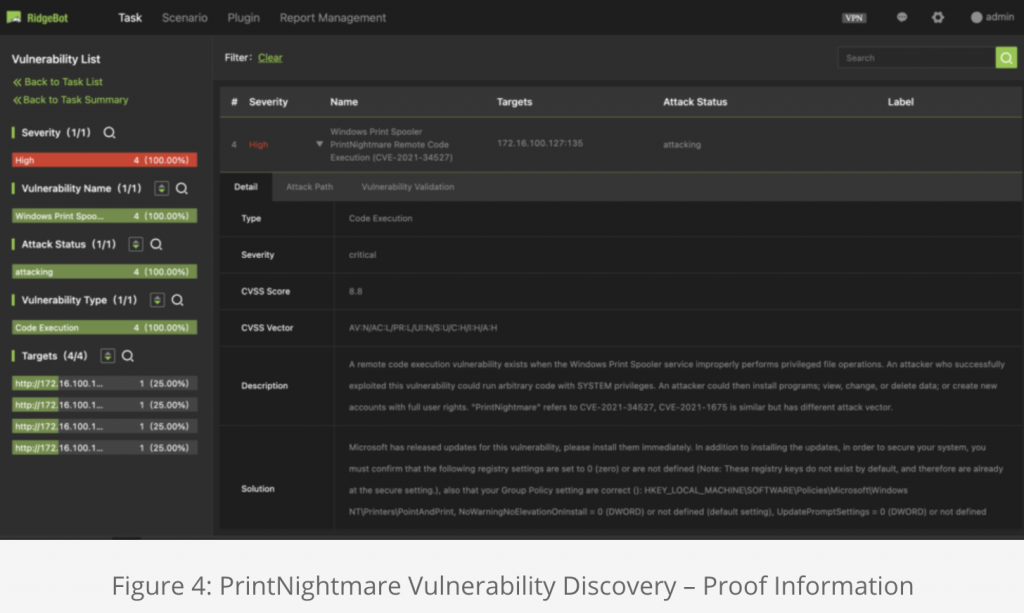
PrintNightmare is another high-impact vulnerability exploit that received pervasive media coverage last month. Its official name is “Windows Print Spooler Remote Code Execution Vulnerability” also CVE-2021-34527. It becomes a literal nightmare for many organizations as it could lead to system intrusions and data breaches on Windows Server 2008/2008R2, 2012/2012R2, 2016, 2019, Windows 10 and others.
Naturally, the victims typically panic at first, and then they come to us for help. In response, the Ridge Security research lab analyzed the two vulnerabilities thoroughly and were able to quickly build the requisite discovery capability into RidgeBot, our automated pen-test bot. If customers test their infrastructure with the latest release of RidgeBot, they will know immediately whether they are at risk with these two harmful vulnerabilities.
For reference, the following screen shots (Figure 1-4) demonstrate the discoveries of HelloKitty and PrintNightmare vulnerabilities in networks that were scanned by RidgeBot.
Category: VENDORSNEWSRidge Security News
