VENDORS
NESSAR VIETNAM TECHNOLOGIES JOINT STOCK COMPANY RECEIVED “ASEAN DISTRIBUTOR PARTNER OF THE YEAR 2023” SELECTED BY STELLAR CYBER
Nessar Vietnam Technologies Joint Stock Company received “ASEAN Distributor Partner of the year 2023” selected by Stellar Cyber Hanoi, March 14, 2024 – Stellar Cyber...
View moreNessar, Stellar Cyber và Viettel IDC have brought Viettel Virtual SOC – an automated security monitoring platform that can automate up to 90% of security operations for organizations and enterprises in Vietnam
Nessar, Stellar Cyber và Viettel IDC have brought Viettel Virtual SOC – an automated security monitoring platform that can automate up to 90% of security...
View moreNessar – Stellar Cyber and Viettel IDC introduced VSOC at the Data Center & Cloud Infrastructure Summit 2023 event
Nessar – Stellar Cyber and Viettel IDC introduced VSOC at the Data Center & Cloud Infrastructure Summit 2023 event HN – Nessar Vietnam and Stellar...
View moreFireMon, Nessar, and Viettel IDC collaborate to enhance network security in Vietnam
FireMon, Nessar, and Viettel IDC collaborate to enhance network security in Vietnam HN – On April 14, 2023, Nessar and Viettel IDC jointly announced the...
View moreContinuing its success, Nessar in collaboration with Viettel IDC organized a comprehensive cloud security conference in Ho Chi Minh City.
Continuing its success, Nessar in collaboration with Viettel IDC organized a comprehensive cloud security conference in Ho Chi Minh City. TP.HCM – Nessar in collaboration...
View moreNessar and Viettel IDC host the seminar “Enhancing the security future – Activating comprehensive security in the future”
Nessar and Viettel IDC host the seminar “Enhancing the security future – Activating comprehensive security in the future” Hanoi – On August 16, a seminar...
View moreNessar becomes a comprehensive strategy distributor of Supermicro in Vietnam
Nessar becomes a comprehensive strategy distributor of Supermicro in Vietnam Nessar Vietnam has officially become a distribution partner of Supermicro – the world’s leading Tier...
View moreNessar Vietnam commits to providing free temporary cybersecurity monitoring services for the Central Highlands – Central Vietnam region
Nessar Vietnam commits to providing free temporary cybersecurity monitoring services for the Central Highlands – Central Vietnam region DN – “We are ready to provide...
View moreThe workshop “Overcoming challenges in the digital transformation process: Solutions from Supermicro and Firemon”
The workshop “Overcoming challenges in the digital transformation process: Solutions from Supermicro and Firemon” HN – On April 13th, in Hanoi, Nessar Vietnam Joint Stock...
View moreNessar presented a security automation solution that achieved up to 90% efficacy at Techfest Vietnam 2022
Nessar presented a security automation solution that achieved up to 90% efficacy at Techfest Vietnam 2022 BD – At Techfest Vietnam 2022, Nessar Vietnam Technologies...
View moreNessar Vietnam – a gold sponsor of the International Conference and Exhibition on Vietnam Cyber Security 2022
Nessar Vietnam – a gold sponsor of the International Conference and Exhibition on Vietnam Cyber Security 2022. HN – In addition to reputable sponsors such...
View moreNessar – Co-head of Cyber Security Technology Village, Techfest organizes a workshop on “Cybersecurity Training in Vietnam”.
Nessar is a partner with Techfest’s Technology Village in organizing the seminar “Cybersecurity Training in Vietnam”. HN – The conference “Cybersecurity Training in Vietnam” within...
View moreNESSAR become an official distributor of Array Networks
Nessar officially becomes a distributor of Array Networks products and solutions. Array Networks is a pioneer in providing a Network Functions platform that combines the...
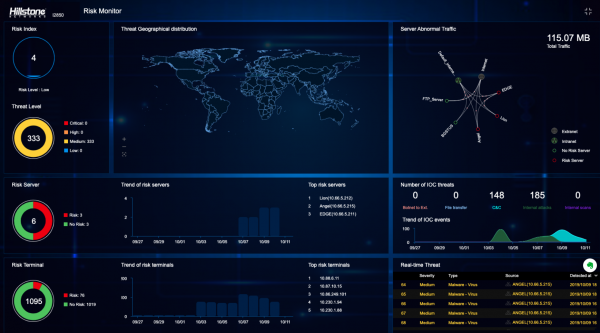
View moreHillstone’s Standalone SD-WAN Solution
Hillstone’s Standalone SD-WAN Solution The latest Hillstone Security Management Platform (HSM) release, version 5.0, expands upon previous versions to provide the first dedicated SD-WAN controller, manager and...
View moreHillstone Security Management Platform
Accelerating Deployment Cycles. Reducing Management Overhead. Simplify Configuration. Hillstone’s Security Manager enhances network security by allowing businesses to segment their networks into multiple virtual domains....
View moreHillstone Security Audit Platform (HSA)
Transform Log Data into Security Intelligence ISPs, universities, large enterprises, government agencies, and large data centers generate millions of events everyday. They require high performance...
View moreHillstone ADC Solution
Application Availability and Protection with Built-In Scalability Hillstone’s Application Protection products include an advanced application delivery controller (ADC) that helps scale the performance of your...
View moreHillstone Server Protection Solution
Comprehensive Server Protection with Unparalleled Visibility and Efficacy Hillstone Server Breach Detection System (sBDS) I-Series product line detects and helps mitigate advanced multi-stage, multi-layer, threats...
View moreHillstone Cloud Protection
Hillstone Cloud Protection Easily Protect your Cloud Applications and Resources With the adoption of public clouds and increasing importance of virtualization, organizations need security solutions...
View moreHillstone Edge Protection Solutions
The First Line of Defense Multi-stage, Multi-layer Attacks Hillstone Edge Protection Solutions Reimagine Perimeter Defense For many corporations, the enterprise edge is the first line...
View moreClustering and other Enhancements for Hillstone ADCs
Clustering and other Enhancements for Hillstone ADCs Recently, Hillstone announced the release of its Application Delivery Controller (ADC) version 2.8. This release offers new models...
View moreHolm Security: 5 Steps to Successful Vulnerability Management
5 Steps to Successful Vulnerability Management Vulnerability Management is a cornerstone in a modern cyber security defense. But getting started and implementing a successful security...
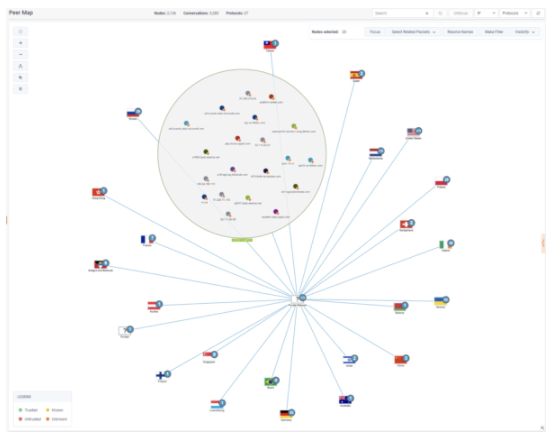
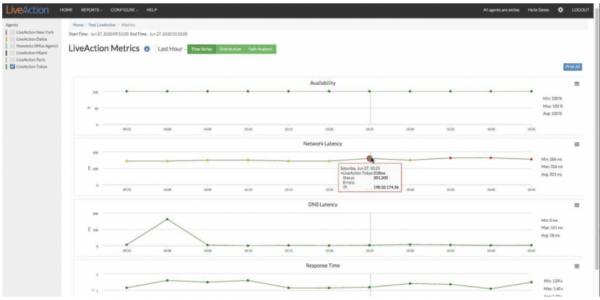
View moreHow to View WAN Applications in LiveNX
How to View WAN Applications in LiveNX Wide-area networks (WAN) have undergone a great transformation over the past decade. An enabler of this evolution, cloud...
View moreA Programmer’s Perspective on Life, the Universe, and the Network
A Programmer’s Perspective on Life, the Universe, and the Network In Part 1, A Programmer’s Perspective on the Current State of Network Tools, we left off...
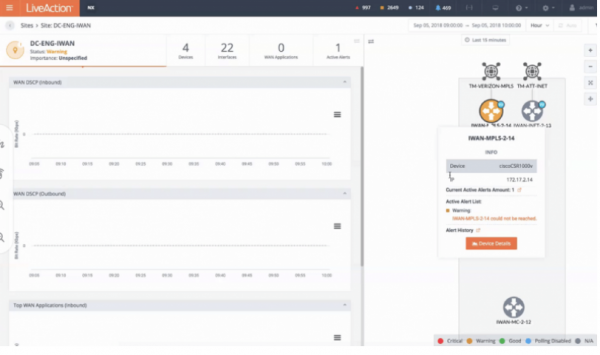
View moreHow to View Sites, Devices, and Interfaces in LiveNX
How to View Sites, Devices, and Interfaces in LiveNX As the network grows more complex, it becomes clear that proper network monitoring software is...
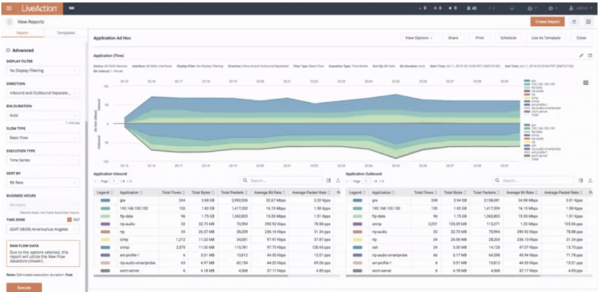
View moreBuild Your Own Network Performance Dashboard
Build Your Own Network Performance Dashboard A network monitoring dashboard is one of the most important features within an all-inclusive network monitoring solution. A dashboard is...
View moreGetting Started with the LiveNX Network Monitoring Dashboard
Getting Started with the LiveNX Network Monitoring Dashboard IT teams are constantly inundated with alerts, requests, and a multitude of daily tasks to properly monitor...
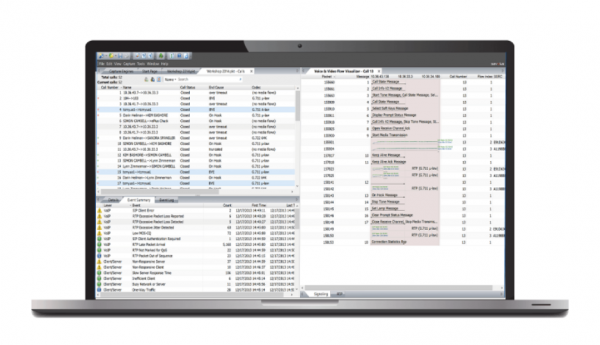
View moreHow To Identify Network Issues Hop-By-Hop
How To Identify Network Issues Hop-By-Hop First, let’s define the problem. As networks get bigger they get more complicated. A pretty straightforward statement, but why...
View moreWhat Is a Network Packet?
What Is a Network Packet? Everything flowing through a network can be classified as part of data enclosed in a packet. A network packet or IP packet...
View moreHow to Measure Network Performance Effectively
How to Measure Network Performance Effectively To run an enterprise effectively today, a good chunk of the yearly budget will have to be directed towards...
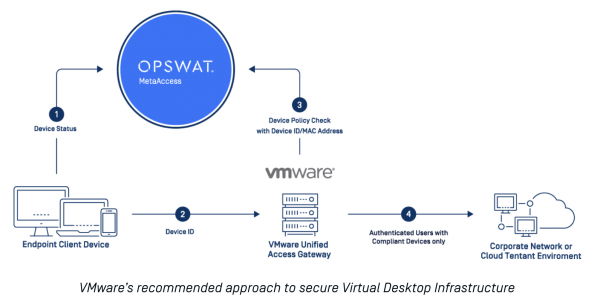
View moreOPSWAT Solutions now available in VMware Marketplace
OPSWAT Solutions now available in VMware Marketplace As a leading provider of security solutions protecting the world’s most critical infrastructure, OPSWAT has built a network...
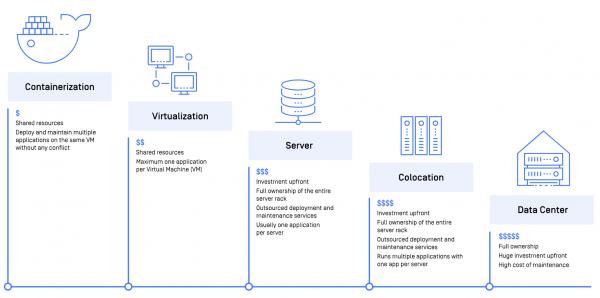
View moreEvolution of Infrastructure: From Data Centers to Containers
Evolution of Infrastructure: From Data Centers to Containers The impact of the digital transformation revolution requires organizations to look for more efficient solutions to manage,...
View moreSignificant Enterprise Features Available in MetaDefender Cloud
Significant Enterprise Features Available in MetaDefender Cloud MetaDefender Cloud platform has been servicing large enterprises for tens of thousands of active users monthly. OPSWAT is...
View moreWHEN SECURITY AND BUSINESS CONVERGE: MEET ED JOPECK
Ed Jopeck is an accomplished national security professional. For nearly three decades, he has worked extensively with the U.S. government, starting as an analyst...
View moreQuantum Scalar Tape Libraries
Data Protection & Long-Term Storage Are More Important Than Ever Tape has been used for decades to preserve and protect data, and today more than...
View moreQuantum StorNext Appliances and Block Storage Systems
StorNext Appliances Overview Quantum offers a flexible range of appliances to host the StorNext File System in order to meet the unique needs of any...
View moreQuantum Solutions for Life Sciences
Simplifying Petabyte-Scale Data Growth Advances in genomics sequencing, microscopy, and bioinformatics have made it possible for researchers to leverage data sets to develop vaccines, find...
View moreProtect and Retain Data at Scale
Reduce Data Protection Cost by Over 50% File-based storage systems, such as scale-out NAS, have become more sophisticated, storing and delivering data to applications and...
View moreRansomware Recovery
The Relentless Onslaught of Ransomware Attacks are now occurring every 11 seconds, and demand for payments continue their upward trend with backup environments becoming a...
View moreSolutions for Big Data in Manufacturing
Why Manufacturers Need a Big Data Solution High-tech manufacturers are constantly looking for ways to increase efficiency, reduce costs, and streamline productivity, and their data...
View moreProtect and preserve your critical data ON QUANTUM
Ensure the Availability of Your Production Data with Efficient Backup, Recovery, and Archive Solutions from Quantum The requirements for protecting data across the Enterprise continue...
View moreRecord and analyze video surveillance data…On Quantum
Making the World Safer and Smarter with Surveillance and Analytics Surveillance recording and analytics are helping to make the world safer through loss prevention, access...
View moreQuantum ransomware
ULTIMATE RANSOMWARE RECOVERY WITH A BUILT-IN, OFF-NETWORK SECURE VAULT Quantum’s Tape Libraries with active vault software, a proven solution against modern cyberattacks. The threat of...
View moreWhat is the right way to detect OS by using SMB?
What is the right way to detect OS by using SMB? After studying different vendors’ approaches, here is our summary of how to do...
View moreHow to Use Microsoft SMB for OS Detection
The Study of Different Approaches from 4 Well-Known Vendors You may wonder “how does a blackbox penetration test tool know about my server information...
View moreOperating System Fingerprint Recognition – Server Message Block (SMB)
Operating System Fingerprint Recognition – Server Message Block (SMB) Whether you conduct penetration testing an automated vulnerability scanning, knowing your target is the very...
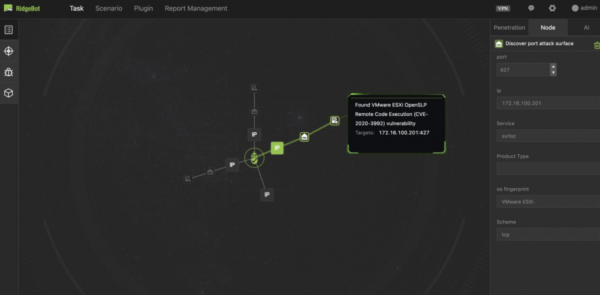
View moreRidgesecurity: Stop HelloKitty and PrintNightmare with RidgeBot
Stop HelloKitty and PrintNightmare with RidgeBot In the cyberworld, HelloKitty is not a cute kitten. And PrintNightmare is an actual nightmare. HelloKitty is a ransomware group who used CVE-2020-3992 to exploit...
View moreRecently discovered Zimbra vulnerabilities may have compromised 200,000 companies
Recently discovered Zimbra vulnerabilities may have compromised 200,000 companies Zimbra, an open-source collaborative office suite, consisting of webmail, web...
View moreRidge Security Announces Expanded Core Capabilities in RidgeBot with Enhanced Web Application Testing
Ridge Security Announces Expanded Core Capabilities in RidgeBot with Enhanced Web Application Testing From network, to host, to web applications, RidgeBot 3.5 delivers the most...
View moreThe Past, Present, and Future of Pentesting
The Past, Present, and Future of Pentesting Pentesting, or penetration testing, is a cybersecurity measure that fights hackers by exposing the hacker’s possible entry points,...
View moreUnderstanding the Challenges, Risks and Best Practices for Securing APIs
Understanding the Challenges, Risks and Best Practices for Securing APIs Overview Most of today’s digital experiences are powered by APIs, however security remains a primary...
View moreChina has Published Its Specific Law for the Protection of Personal Data. What Are the Implications?
China has Published Its Specific Law for the Protection of Personal Data. What Are the Implications? Global efforts to ensure data protection have increased dramatically...
View moreThe benefits of Using Cloud Computing
The benefits of Using Cloud Computing Cloud computing has been around for some time, and while data points to the efficiency, cost-effectiveness, and competitive advantages...
View moreThe Biggest Cyberattacks of Recent Years
The Biggest Cyberattacks of Recent Years We all know that cyber vulnerabilities are not a current issue. However, with the evolution of technology and virtualization growing...
View moreDigital Sovereignty: The Precepts of Senhasegura According to an American Periodical
Digital Sovereignty The Precepts of Senhasegura According to an American Periodical Nomenclatures and acronyms are part of the routine of those who work in...
View moreWhy is Data the New Oil?
Why is Data the New Oil? Performing any task today is much easier than it was a few years ago. With the evolution of...
View moreWhy is Information Security Important to Your Organization?
Why is Information Security Important to Your Organization? As technology becomes increasingly sophisticated, criminals’ skills often evolve as well, in many cases surpassing the...
View moreIs your company really prepared for a cyber attack? – Part 2
Is your company really prepared for a cyber attack? – Part 2 In the previous article, we discussed the importance of digital transformation to...
View moreSenhasegura: The Pillars of Information Security – Part 2
The Pillars of Information Security – Part 2 Currently, the use of information is a great ally for companies from different industries. However, along with...
View moreChina has Published Its Specific Law for the Protection of Personal Data. What Are the Implications?
China has Published Its Specific Law for the Protection of Personal Data. What Are the Implications? Global efforts to ensure data protection have increased dramatically...
View moreThe benefits of Using Cloud Computing
The benefits of Using Cloud Computing Cloud computing has been around for some time, and while data points to the efficiency, cost-effectiveness, and competitive advantages...
View moreThe Biggest Cyberattacks of Recent Years
The Biggest Cyberattacks of Recent Years We all know that cyber vulnerabilities are not a current issue. However, with the evolution of technology and virtualization growing...
View moreDigital Sovereignty: The Precepts of Senhasegura According to an American Periodical
Digital Sovereignty The Precepts of Senhasegura According to an American Periodical Nomenclatures and acronyms are part of the routine of those who work in...
View moreWhy is Data the New Oil?
Why is Data the New Oil? Performing any task today is much easier than it was a few years ago. With the evolution of...
View moreWhy is Information Security Important to Your Organization?
Why is Information Security Important to Your Organization? As technology becomes increasingly sophisticated, criminals’ skills often evolve as well, in many cases surpassing the...
View moreIs your company really prepared for a cyber attack? – Part 2
Is your company really prepared for a cyber attack? – Part 2 In the previous article, we discussed the importance of digital transformation to...
View moreSenhasegura: The Pillars of Information Security – Part 2
The Pillars of Information Security – Part 2 Currently, the use of information is a great ally for companies from different industries. However, along with...
View moreNESSAR VIETNAM TECHNOLOGIES JOINT STOCK COMPANY RECEIVED “ASEAN DISTRIBUTOR PARTNER OF THE YEAR 2023” SELECTED BY STELLAR CYBER
Nessar Vietnam Technologies Joint Stock Company received “ASEAN Distributor Partner of the year 2023” selected by Stellar Cyber Hanoi, March 14, 2024 – Stellar Cyber...
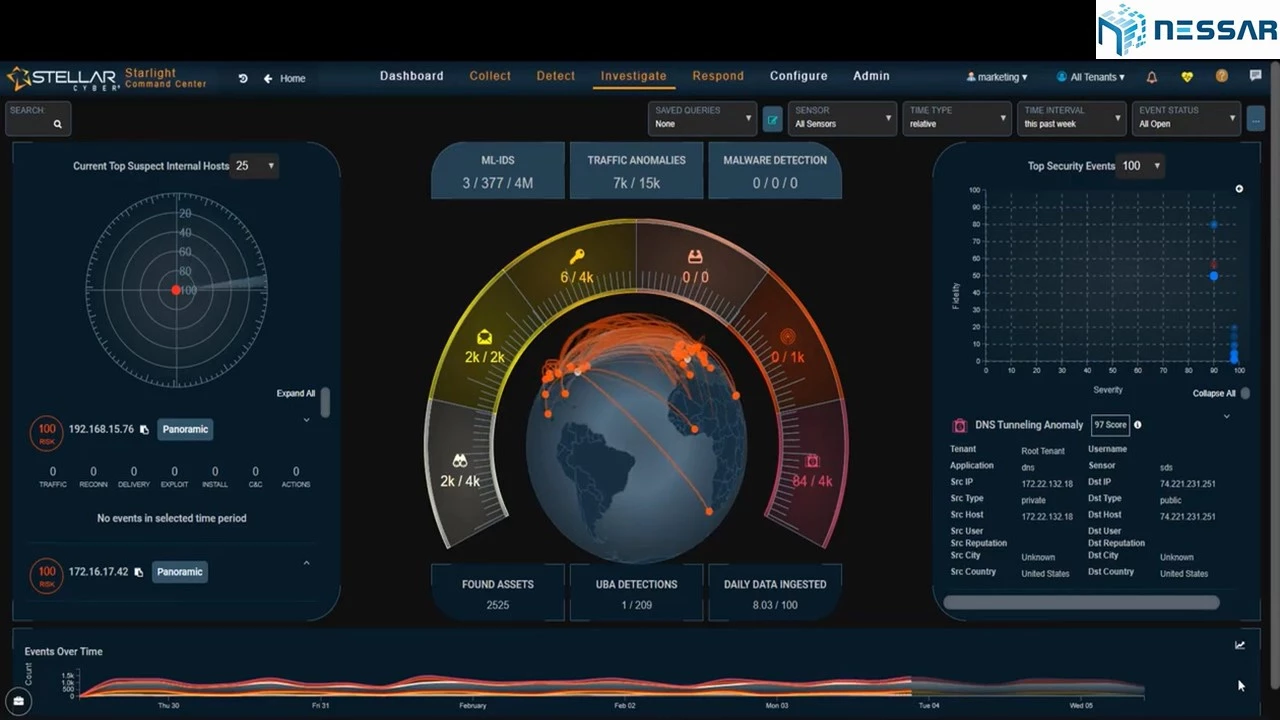
View moreStarlight Open-XDR Platform
TODAY’S CYBER SECURITY CHALLENGE Cyberattacks and breaches are soaring and security budgets are growing in response. The industry needs a scalable, intelligent central platform...
View moreStellar Cyber with John Peterson, Chief Product Officer
Stellar Cyber with John Peterson, Chief Product Officer On this episode of Silicon Valley Insider host Keith Koo has special guest John Peterson, Chief Product...
View more