Post article posting products
Hillstone – Web App Firewall
Comprehensive Security for Web Assets and APIs Hillstone W-Series Web Application Firewall High-Performance Web App Firewall Defends Against OWASP Top 10 Threats Hillstone W-Series Web...
View moreHillstone – Network Intrusion Prevention System
Understanding what you’re seeing Hillstone Network Intrusion Prevention System (NIPS) Flexible Network Infrastructure Protection with Superior Visibility and Intelligence Hillstone’s Network Intrusion Prevention System (NIPS)...
View moreHillstone HSM
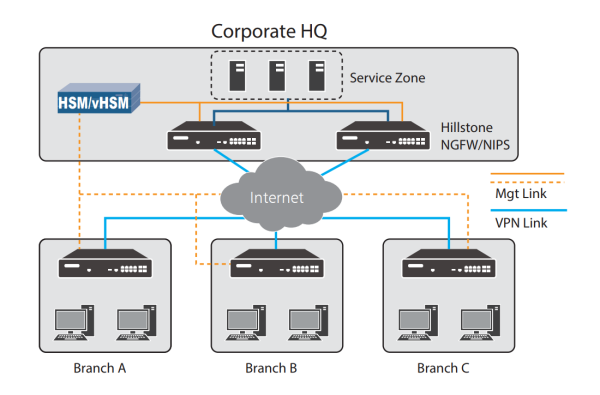
Efficient Security Operations, Secure SD-WAN, ZTNA Management and More Hillstone Security Management Platform Hillstone Security Management (HSM) is a powerful management system that provides advanced...
View moreHillstone CloudHive
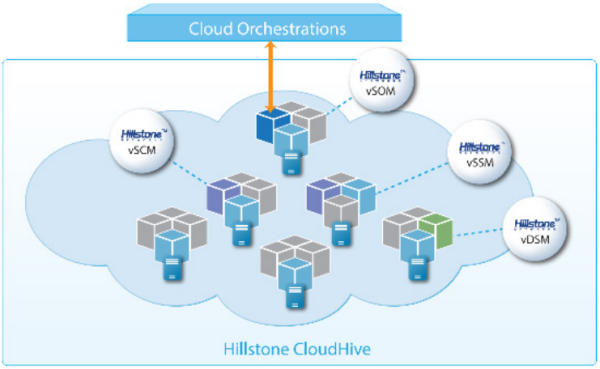
Comprehensive Cloud Protection & Data Security Hillstone CloudHive Solution Comprehensive Cloud Infrastructure Protection with Micro-Segmentation Hillstone CloudHive provides a comprehensive cloud workload protection platform (CWPP)...
View moreHillstone CloudEdge
Cloud Security / Virtualized NGFW Hillstone CloudEdge Solution Comprehensive Cloud Infrastructure Protection for Virtualized Workloads Hillstone CloudEdge is a virtual next-generation firewall (vNGFW) for public...
View moreStellar Cyber
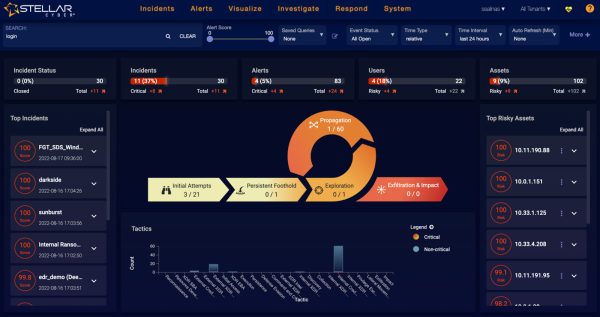
Stellar Cyber SecOps Platform Helps You Take Control of your Security Operations Stop chasing alerts and start closing cases today. Learn more about the Stellar...
View moreCommercial Building
Commercial Building ACTi commercial building end-to-end solutions automate your building maintenance and security management using smart building technologies. The solutions are able to integrate surveillance,...
View moreACTi RAS-101
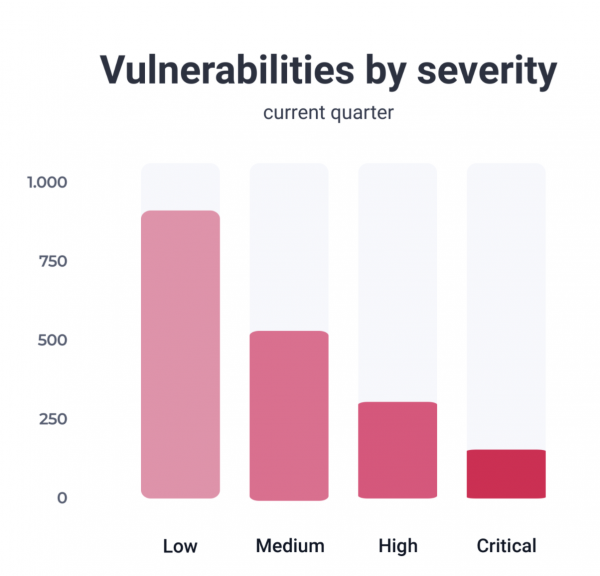
RAS-101 10-Channel Standalone Market Application Suite for Retail Application Total Traffic Performance vs Weather Total Traffic Performance vs Gender/Age Total Traffic Performance vs Weather vs...
View moreACTi RAS-100
RAS-100 100-Channel Standalone Market Application Suite for Retail Application Total Traffic Performance vs Weather Total Traffic Performance vs Gender/Age Total Traffic Performance vs Weather vs...
View moreACTi IPS-100
IPS-100 Standalone Market Application Suite Event real-time monitoring in forbidden zone to detect illegally parked vehicle, and trigger the alarm notification along with detected license...
View moreArray AG1500FIPS
Powered by Array’s SpeedCore® 64-bit architecture, the Array AG1500FIPS is the ideal choice for businesses and service providers looking for flexible and scalable secure access...
View moreArray AG1600V5
Powered by Array’s SpeedCore® 64-bit architecture, the Array AG1600V5 is the ideal choice for businesses and service providers looking for flexible and scalable secure access...
View moreArray AG1500V5
Powered by Array’s SpeedCore® 64-bit architecture, the Array AG1500V5 is the ideal choice for businesses and service providers looking for flexible and scalable secure access...
View moreArray AG1200V5
Powered by Array’s SpeedCore® 64-bit architecture, the Array AG1200V5 is the ideal choice for businesses and service providers looking for flexible and scalable secure access...
View moreArray AG1100V5
Powered by Array’s SpeedCore® 64-bit architecture, the Array AG1100V5 is the ideal choice for businesses and service providers looking for flexible and scalable secure access...
View moreArray AG1000V5
Powered by Array’s SpeedCore® 64-bit architecture, the Array AG1000V5 is the ideal choice for businesses and service providers looking for flexible and scalable secure access...
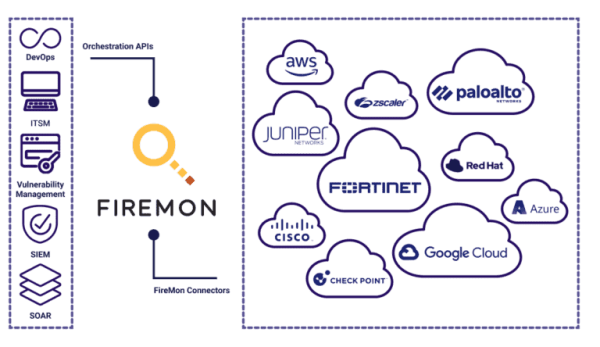
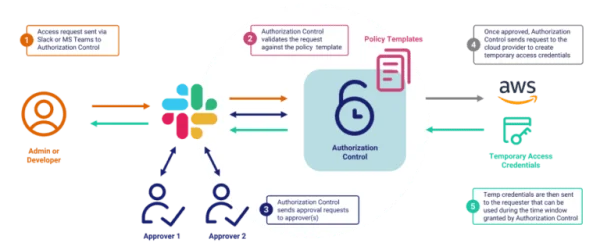
View moreFireMon – Policy Manager
FIREMON PRODUCTS Policy Manager Automate firewall and cloud security policy management from ground to cloud. VIEW DATASHEET Unified Firewall Policy Management FireMon Policy Manager automates...
View moreFireMon – Cloud Defense
FIREMON Cloud Defense Real-time cloud security compliance, inventory, misconfiguration, and threat detection. Now with Just-In-Time IAM defense at an industry-best price. Pragmatic CSPM for Security...
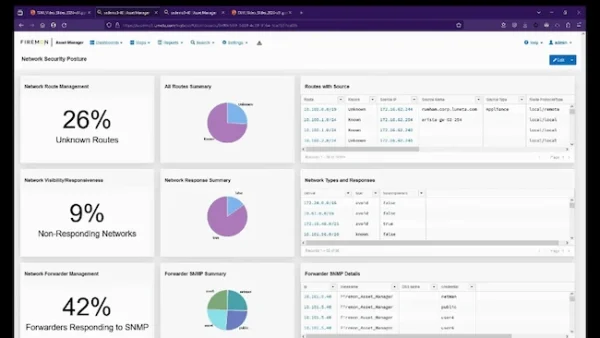
View moreFireMon – Asset Manager
FIREMON PRODUCTS Asset Manager Formerly Lumeta Unmatched real-time cybersecurity asset management that enables network and security teams to discover the darkest corners of their often-obscure infrastructure....
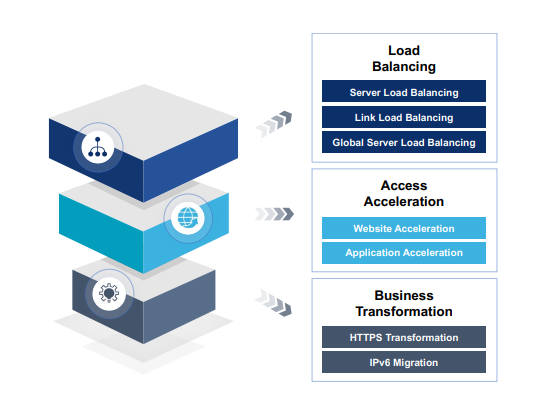
View moreHillstone – Application Delivery Controller
Protecting Critical Applications Hillstone Application Delivery Controller Solution Application Availability and Web Application Protection with Built-In Scalability Hillstone’s Application Protection products include an advanced application...
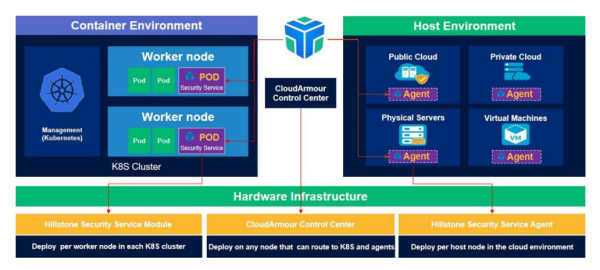
View moreHillstone – CloudArmour
Cloud Workload Protection Platform (CWPP) Hillstone CloudArmour CWPP Solution Comprehensive Cloud Workload Protection Hillstone’s CloudArmour is a CWPP solution that provides deep visibility of the...
View moreHillstone – Data Center NGFW
Enterprise Data Center Security Hillstone X-Series Data Center Firewall Solutions Carrier-Class Infrastructure Protection for Data Centers Hillstone X-Series is a multi-tenant next-generation firewall (NGFW) for...
View moreHillstone – Next Generation Firewalls
Hillstone’s Future-Ready NGFW Platform Hillstone A-Series Hillstone’s Future-Ready Next Generation Firewall Platform The Hillstone A-Series next-generation firewall features high security performance, flexible expansion, complete advanced...
View moreHillstone – License Management System (LMS)
License Management Solution for Virtual Network Function Deployments Hillstone License Management System (LMS) Options for Public Network and Private Networks Hillstone License Management System (LMS)...
View moreHillstone – Web App Firewall
Comprehensive Security for Web Assets and APIs Hillstone W-Series Web Application Firewall High-Performance Web App Firewall Defends Against OWASP Top 10 Threats Hillstone W-Series Web...
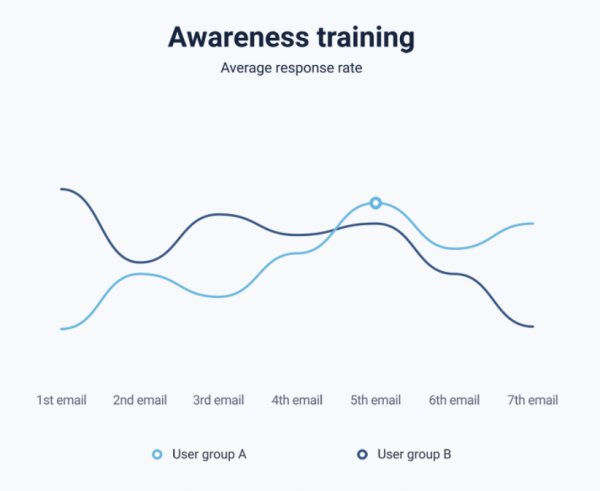
View morePhishing simulation & awareness training
Phishing simulation & awareness training Over 90 % of data breaches start with a malicious email. Do you know how your users will respond to the next attack? Our product for phishing simulation and awareness training helps you increase resilience...
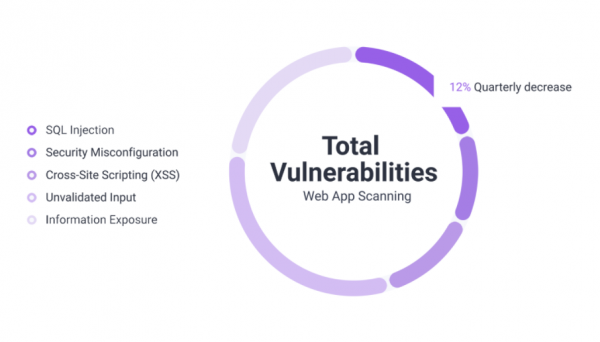
View moreWeb Application Scanning
Web Application Scanning Gartner states that 75% of the attacks occur in the application layer, which makes web applications the most vulnerable layer in your...
View moreSystem And Network Scanning
System And Network Scanning Our automated and continuous system and network scanner provides unparalleled coverage and comprehensive insight to enable you to detect vulnerabilities, assess...
View moreLiveNX Enterprise Network Monitoring Software Platform
Next Generation Enterprise Network Monitoring Software LiveNX is the only network performance platform with the scale and power to optimize your entire network. Unify...
View moreLiveNA Network and Application Anomaly Detection
AIOps for Enterprise Network Monitoring LiveNA uses Artificial Intelligence and Machine Learning to provide expert insights to application and network performance. Application Performance Optimization...
View moreLiveSP Network Monitoring for Service Providers
Solutions Delivery and Assurance for SP LiveSP network monitoring and reporting platform helps suppliers deliver value-added services to their customers. Collect Data from an Unlimited...
View moreLiveCapture Packet Capture and Analysis
Optimize the Performance of Your Remote Network Quickly troubleshoot and resolve poor application performance at branch offices, WAN links, and data centers. Capture Packets...
View moreLiveAction Omnipeek Network Protocol Analyzer
World’s Most Powerful Network Protocol Analyzer Omnipeek empowers you with rapid-fire analytics and insights so you can make the best decisions, quickly,about your network speed,...
View moreLiveWire – Extend Network Monitoring
Optimize Application Performance at Remote Sites, WAN edge, and Data Centers LiveWire supports quickly troubleshoot and resolve poor application performance at remote sites, WAN edge,...
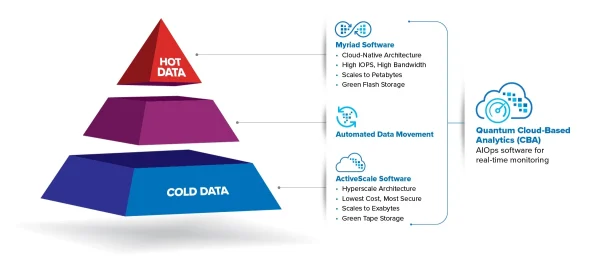
View moreQuantum – Scalar Tape Storage
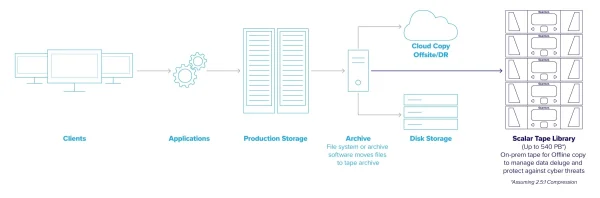
Low-Cost, Reliable Long-Term Data Storage for Massive Data Growth Tape is the most cost-effective, secure storage option that requires very little power to store data...
View moreQuantum – DXi Backup Appliances
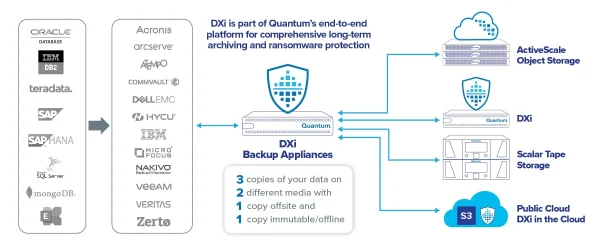
Reduce Risks with Efficient Data Protection, Cyber Resilience, and Disaster Recovery Business continuity is critical to every organization, and enterprises must protect against operational risks...
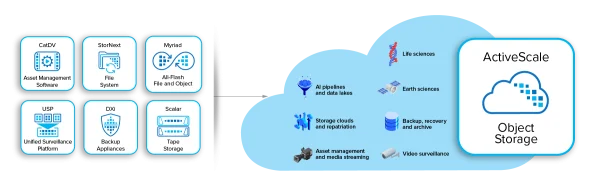
View moreQuantum – ActiveScale Object Storage
Secure, Scalable S3 Object Storage for Analyzing, Managing, and Retaining Massive Data Sets With AI pipelines and other data-intensive workflows topping the list of business...
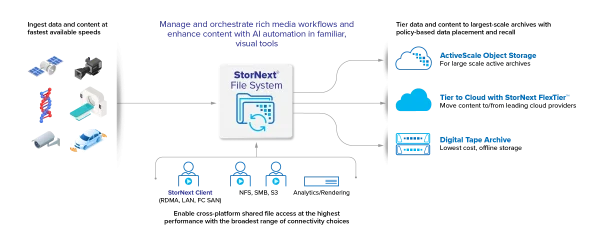
View moreQuantum – StorNext File System
Maximum Productivity and Efficiency for Your End-to-End Workflows With the demand for rich media content constantly growing, content producers need to work on fast-moving data...
View moreQuantum – Myriad All-flash file and Object Storage
A Modern All-Flash Storage Platform Designed to Power New Workflows Modern applications like rapidly evolving data and life sciences, AI & ML, and VFX &...
View moreRedis Open Source
Redis Open Source Redis 8 is free. Seriously. No games. Just free open source software. You read that right. It doesn’t cost anything to start...
View moreRedis Software
Redis Software Enterprise-grade Redis wherever you need it Build with the most feature-rich Redis—on premises or self managed in the cloud—and deploy how you want...
View moreRedis Cloud
Redis Cloud You know us for caching. Find out why. Build on any cloud with the highest-performing, most feature-rich Redis as a service. Start building...
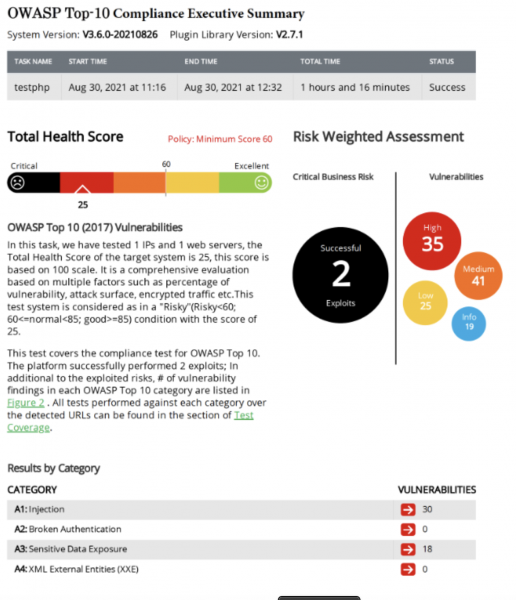
View moreOWASP Top 10 Compliance with RidgeBot 3.6
OWASP Top 10 Compliance with RidgeBot 3.6 What is OWASP Top 10? Security breaches and attacks have become so prevalent that only the very...
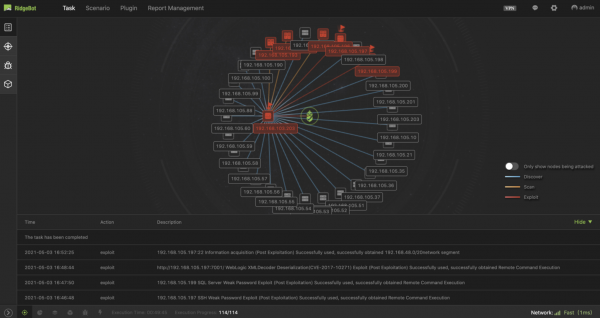
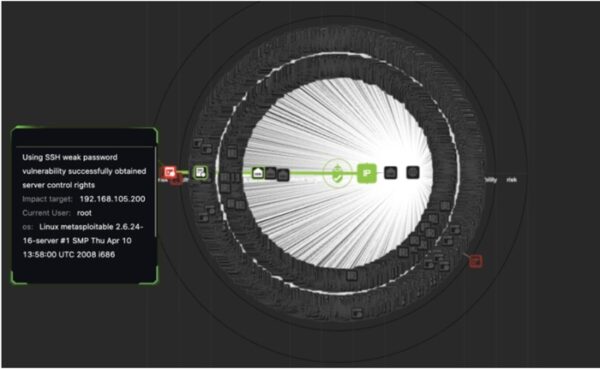
View moreRidge Security Automated Penetration Testing Solution Delivers Advanced Post-Exploitation Techniques
https://youtu.be/DzYvgEPqKCY Ridge Security Automated Penetration Testing Solution Delivers Advanced Post-Exploitation Techniques Ridge Security helps you stay on the front lines of cyber defense with...
View more10 Key RidgeBot Features
10 Key RidgeBot Features Learn how enterprise customers achieve Risk-Based Vulnerability Management using RidgeBot’s automated penetration testing technology. These 10 key RidgeBot features provide...
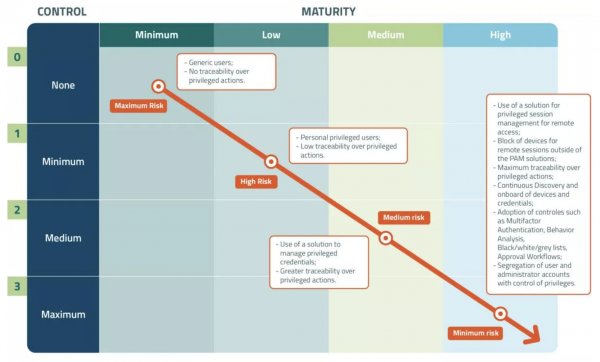
View morePAMaturity
PAMaturity Find out your PAM maturity level. We at senhasegura take Privileged Access Management (PAM) seriously. And we want to bring all of our PAM...
View morePAM Advanced Monitoring
PAM Advanced Monitoring Full monitoring of the senhasegura solution. What it is Monitoring of senhasegura operation aspects and its components. Benefits Operational gain in the...
View morePAM Load Balancer
PAM Load Balancer Optimal usage of senhasegura resources. What it is Integrated load balancing solution, which monitors various aspects of senhasegura Cluster and performs...
View moreLocal User Provisioning
Local User Provisioning Create and manage local users centrally. What it is Provisioning and revocation of privileged local user access on Windows, Linux and...
View moreCertificate Management
Certificate Management Automatic and centralized digital certificate management. What it is Centralized management of digital certificates lifecycle within the organization, from discovery through automatic scanning...
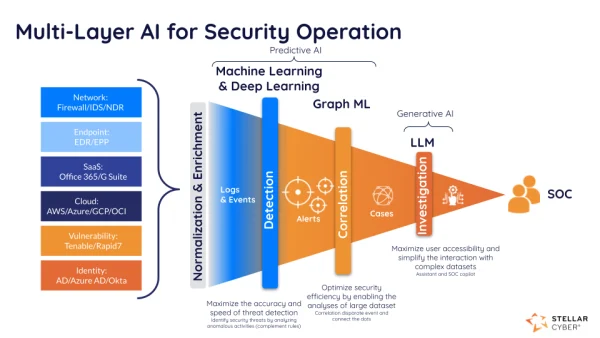
View moreStellar Cyber – Multi Layer AI
Stellar Cyber Multi-Layer AI™ The driving force behind the Stellar Cyber SecOps Platform’s ability to deliver security analyst efficiency and effectiveness gains. Take A Product...
View moreStellar Cyber
Stellar Cyber SecOps Platform Helps You Take Control of your Security Operations Stop chasing alerts and start closing cases today. Learn more about the Stellar...
View moreStellar Cyber Photon Sensor – 10G
Photon Sensor – 10G The Photon Sensor is a network sensor that can monitor 10 LAN segments at an aggregated throughput of 1 gigabit per...
View moreStellar Cyber Photon Sensor – 1G
Photon Sensor – 1G The Photon Sensor enables organizations to gain unprecedented visibility into network security events. By solving the “Goldilocks” problem, our sensors collect...
View more