SENHASEGURA SOLUTIONS
ITSM Integration
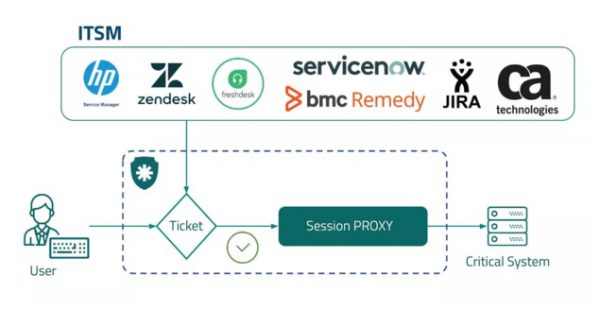
ITSM Integration Avoid unauthorized changes. What it is The senhasegura platform integrates the main IT Service Management (ITSM) solutions to ensure that only changes that...
View morePAM Crypto Virtual Appliance
PAM Crypto Virtual Appliance The solution for virtualized environments For clients who have virtualization infrastructure and wish to choose the architecture plan, senhasegura has the Virtual...
View morePAM Crypto Appliance
PAM Crypto Appliance Advanced hardware technology developed for your company. For companies that want a higher level of security, guaranteed performance, and a centralized software...
View moreHigh availability and contingency
High availability and contingency Eliminate failures that impact your IT environment and cause losses. https://youtu.be/eJp2Nf3muOs Senhasegura has been designed to allow its operation in an...
View moreSenhasegura Security
Senhasegura Security Full protection assured for all types of threats. To ensure optimal protection of stored passwords, senhasegura offers several security mechanisms, both at the...
View moreProduct Architecture
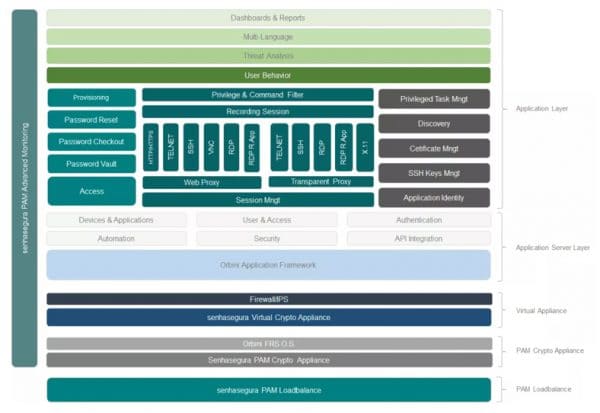
Product Architecture The senhasegura architecture offers the highest technology available. Senhasegura product architecture consists of a set of integrated component layers that support senhasegura functioning,...
View moreHow it works
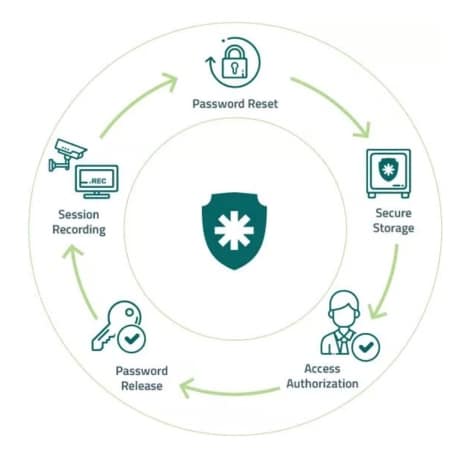
How it works Senhasegura securely centralizes all of your credentials Exposure and misuse of privileged accounts are extremely inviting to cyberattacks. In recent attacks on...
View moreDevOps and Secret Management
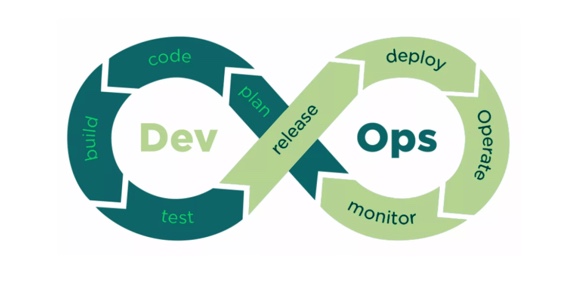
DevOps and Secret Management Senhasegura is fully compliant with DevOps environments. Currently, the software delivery pipeline is focused on delivering high quality products and services...
View morePayment Card Industry – Data Security Standard
Payment Card Industry – Data Security Standard. A favorite target of hackers is companies that accept credit card payments and keep their customers’ sensitive data....
View more7 signs that your company needs to improve the security of sensitive data
7 signs that your company needs to improve the security of sensitive data Undoubtedly, we are in the moment where the most precious asset...
View moreProtect Your Password
Protect Your Password 8 Tips to Protect Your Password We are already in the month of May, and you know what we celebrate on the...
View moreZero Standing Privileges
Zero Standing Privileges With the growth of cyberattacks, access credentials have become a strong attack vector. In 74% of cases of data breaches, companies...
View moreNational Institute of Standards and Technology
NIST- National Institute of Standards and Technology Virtual attacks against government systems are clearly on the rise. According to the FISMA (Federal Information Security...
View moreGeneral Data Protection Regulation
GDPR- General Data Protection Regulation GDPR (General Data Protection Regulation) has been in place since 2016 in all EU Member States and came into...
View moreHealth Insurance Portability and Accountability Act
HIPAA- Health Insurance Portability and Accountability Act The HIPAA (Health Insurance Portability and Accountability Act) was introduced in 1996 and is a set of...
View moreInternational information security management standard
ISO 27001- International information security management standard The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) standard 27001 is internationally recognized...
View moreEasy and agile SOX compliance for your environment
SOX- Easy and agile SOX compliance for your environment Every organization subject to Sarbanes-Oxley (SOX) compliance faces a number of challenges in achieving compliance....
View morePayment Card Industry – Data Security Standard
Payment Card Industry – Data Security Standard. A favorite target of hackers is companies that accept credit card payments and keep their customers’ sensitive data....
View moreAudit- Senhasegura Solution
Audit- Senhasegura Solution Check if you business is in compliance with standards and regulations. Audit- Senhasegura Solution Improper access to privileged accounts is a...
View moreDevOps and Secret Management
DevOps and Secret Management Senhasegura is fully compliant with DevOps environments. Currently, the software delivery pipeline is focused on delivering high quality products and services...
View moreData theft prevention
Data theft prevention Protect your company against critical data theft. Data breaches cost millions to businesses, and the trend is for those amounts to increase...
View morePrivilege Abuse
Privilege Abuse Control the misuse of privileges in your company. In most IT environments, the least privilege principle is not valid. There are many...
View more