VENDORS SOLUTIONS
VENDORS SOLUTIONS
Zero Standing Privileges
Zero Standing Privileges With the growth of cyberattacks, access credentials have become a strong attack vector. In 74% of cases of data breaches, companies...
View moreAudit- Senhasegura Solution
Audit- Senhasegura Solution Check if you business is in compliance with standards and regulations. Audit- Senhasegura Solution Improper access to privileged accounts is a...
View morePrivilege Abuse
Privilege Abuse Control the misuse of privileges in your company. In most IT environments, the least privilege principle is not valid. There are many...
View moreNetwork Service Assurance for Service Providers
Network Service Assurance for Service Providers Drive Enterprise Digital Transformation Our Expertise and Service Provider’s Partnerships The LiveSP and LiveMSP solutions are massively used by...
View moreAchieve Operational Excellence
Achieve Operational Excellence Improve the overall efficiency and effectiveness of your Network team’s planning, deployment, upgrade, maintenance, and troubleshooting tasks. Download Operational Excellence eBook Manage...
View moreAccelerated Network Troubleshooting
Accelerated Network Troubleshooting Accelerate the identification and resolution of the most difficult network performance issues. Download Network Troubleshooting eBook PDF Complete Visibility Identify issues occurring...
View moreManaging for Network Readiness
Managing for Network Readiness Perform continuous monitoring to gain clear insight into priority updates and upgrades to optimize the network. Download the Capacity Planning Whitepaper...
View moreAdvanced Reporting And Analytics
Advanced Reporting And Analytics Generate and share a complete and comprehensive view of network performance, capacity, and utilization. Download the Advanced Network Analytics Whitepaper Pro-Active...
View moreData-Driven Change Initiatives
Data-Driven Change Initiatives Approaching any IT roll-out must be done with a proper data-driven strategy. Before implementing a significant data-driven change initiative, it’s important to...
View moreApplication Performance Optimization
Deliver a superior user experience with insights into the underlying network infrastructure, policies, and protocols that ensure the successful delivery of critical applications. Download...
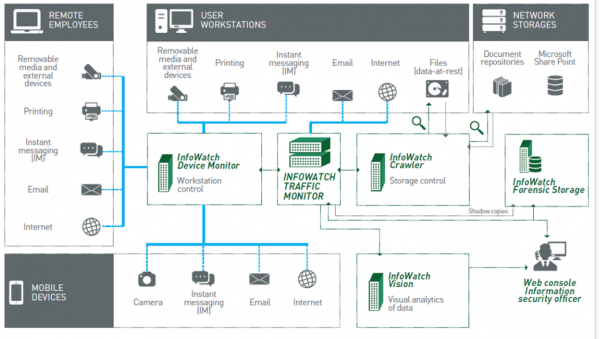
View moreInfowatch Traffic Monitor
Today, many companies defend themselves from viruses and external attacks, while the biggest threat comes from within. Even ordinary employees have access to company’s entire...
View moreInfoWatch Device Monitor
InfoWatch Device Monitor is a module for the protection of workstations, which monitors document printing and copying to removable media, and also ports and portable devices...
View moreWiFi Solutions for Hospitality
Connecting The Chain WiFi for Hotels Hotel owners are now using WiFi-based applications and services to target & engage guests in new ways. Driving differentiation...
View moreCloud Networking
REDUCE NETWORK COMPLEXITY, INCREASE NETWORK INTELLIGENCE With our cloud-first approach, we rapidly innovate and radically simplify wired and wireless networks at scale. Built on the industry’s...
View moreBelden Data Center Solutions
From the demarcation point in the entrance room, to the cross connect, to the equipment rack — and all the cabling in between — Belden...
View morePassive Optical LAN (POLAN) Head Split
Passive optical LANs (POLANs) are adapted to indoor network architectures, and can decrease the amount of cable and equipment required to deploy a network. POLANs...
View morePassive Optical LAN (POLAN) Forward Split
Passive optical LANs (POLANs) are adapted to indoor network architectures, and can decrease the amount of cable and equipment required to deploy a network. POLANs...
View moreData Center Switch Cabinet / Cooling System
Switch cabinets support high load capacities and proper air ow management. With containment, hot exhaust air from equipment is directed to CRAC units through active...
View moreOpen Bridge Rack
An open bridge rack (OBR) provides a flexible path to take you from today’s TIA/EIA-standard rails to open-standard rails when your data center is ready....
View moreFiber LAN Telecom Distribution
Fiber LAN telecom distribution systems take connectivity to wherever it’s needed. As the communications backbone of any business or organization, the right connectivity solutions can...
View moreCopper LAN Horizontal Distribution
Copper LAN horizontal distribution systems take connectivity to wherever it’s needed. As the communications backbone of any business or organization, the right connectivity solutions can...
View more4K HDBaseTTM Solution Guide
HDBase T technology allows the transportation of uncompressed ultra-definition video, audio, Ethernet, control, USB 2.0 and remote power over a single twisted pair cable up...
View moreMDU Multiple Operator Access
By taking ber inputs from multiple operators into separate locked compartments, and sharing with a common building infrastructure, you can offer easy and secure access...
View moreWireless Access Points
Wireless access points (WAPs) can connect to the network in two different ways: Through a patch cord connected to a telecom outlet that is installed...
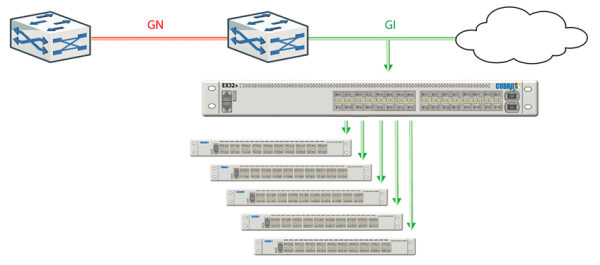
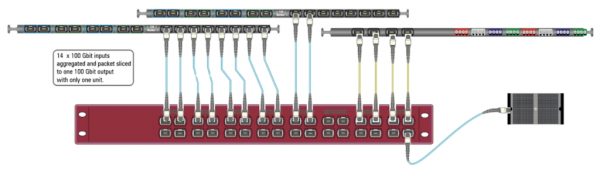
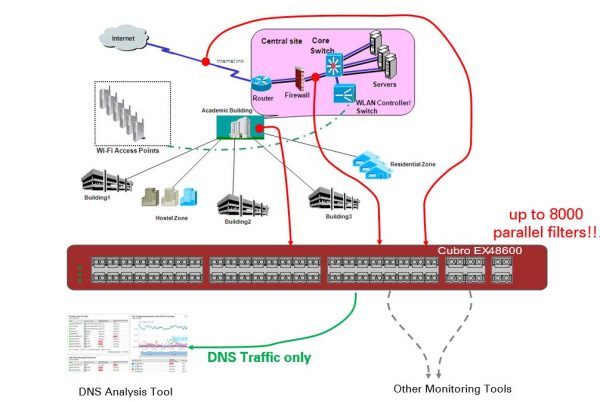
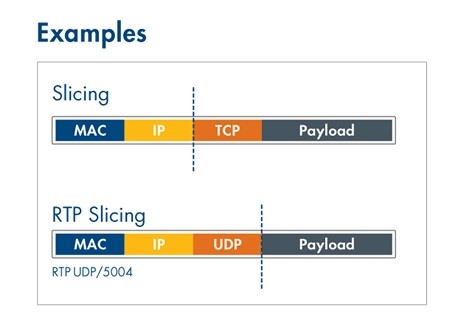
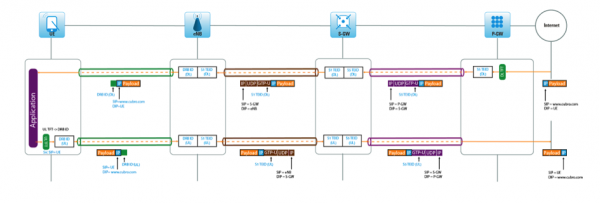
View moreSAVE COSTS OF MONITORING TOOLS WITH PACKET SLICING AT 100 GBIT LINE RATE
Solution description
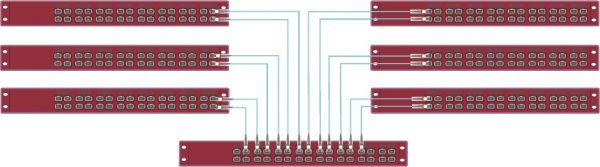
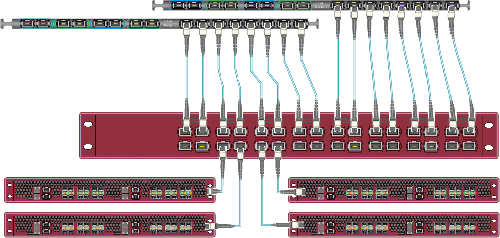
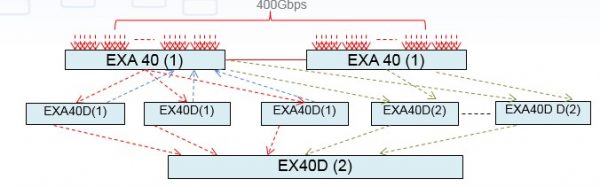
View moreREDUCE COST BY SCALING THE MONITORING GTP LOAD BALANCING WITH EXA32100
Solution description
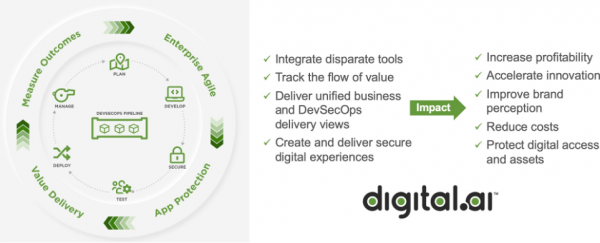
View moreDigital.ai- Platform to accelerate digital transformation
Digital.ai is an industry-leading technology company dedicated to helping Global 5000 enterprises achieve digital transformation goals. Using value stream management as its cornerstone, Digital.ai combines...
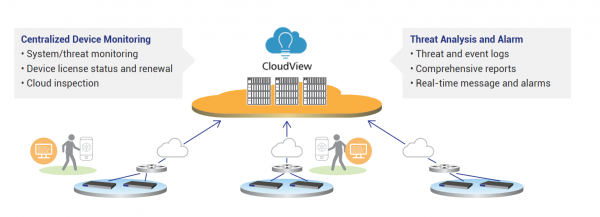
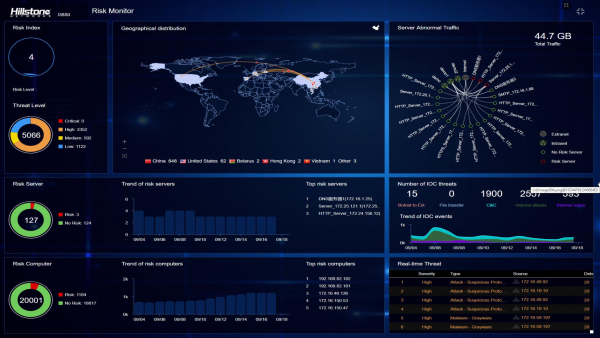
View moreHillstone CloudView
Hillstone CloudView Feature: Device Monitoring• CPU, Memory• Model, OS version, Series Number, IP address etc.• License and renewal status• Abnormality detectionTraffic Monitoring• Uplink/Downlink Traffic• Session•...
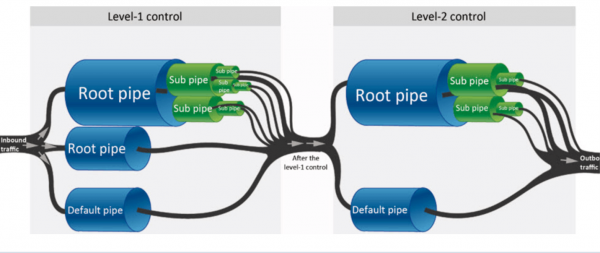
View moreHillstone QoS
Hillstone Quality of Service (QoS) feature: • Max/guaranteed bandwidth tunnels or IP/user basis• Tunnel allocation based on security domain, interface, address, user/user group, server/server group,...
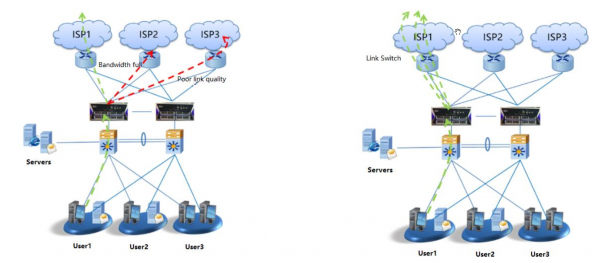
View moreHillstone Load Balancing
Hillstone Load Balancing feature: Link Load Balancing• Bi-directional link load balancing• Outbound link load balancing includes policy based routing, ECMP and weighted, embedded ISP routing...
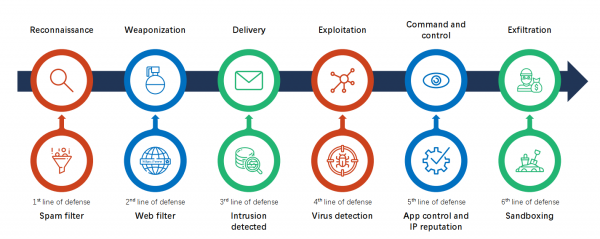
View moreHillstone Intrusion Prevention
Hillstone Intrusion Prevention Feature: • Protocol anomaly detection, rate-based detection, custom signatures, manual, automatic push or pull signature updates, integrated threat encyclopedia• IPS Actions: default,...
View moreHillstone Cloud Sanbox
Hillstone Cloud Sanbox feature • Upload malicious files to cloud sandbox for analysis• Support protocols including HTTP/HTTPS, POP3, IMAP, SMTP and FTP• Support file types...
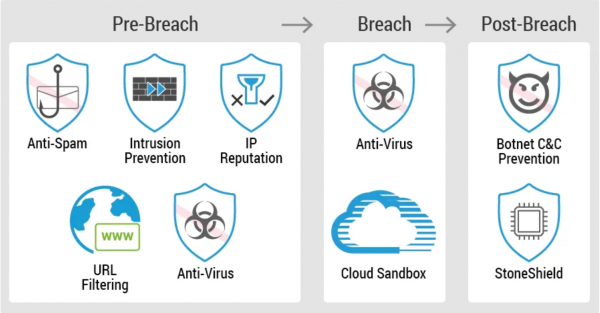
View moreHillstone Attack Defense
Hillstone Attack Defense Feature: • Abnormal protocol attack defense• Anti-DoS/DDoS, including SYN Flood, UDP Flood, DNS Query Flood defense, TCP fragment, ICMP fragment, etc.• ARP...
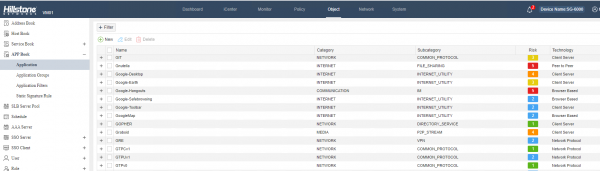
View moreHillstone Appliaction Control
Hillstone Application Control Feature: • Over 3,000 applications that can be filtered by name, category, subcategory, technology and risk• Each application contains a description, risk...
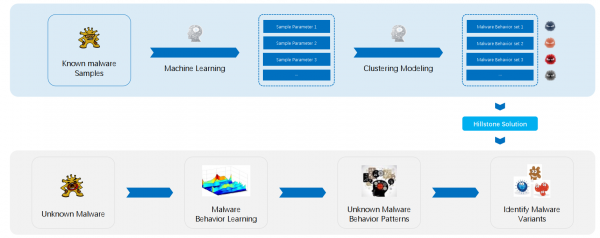
View moreHillstone Advanced Threat Detection
The Hillstone Advanced Threat Detection (ATD) Engine analyzes millions of known HTTP based malware samples with regular updates. It extracts the common characteristics of each...
View moreHillstone Anti Spam
Hillstone Anti Spam feature • Real-time spam classification and prevention • Confirmed Spam, Suspected Spam, Bulk Spam, Valid Bulk • Protection regardless of the language,...
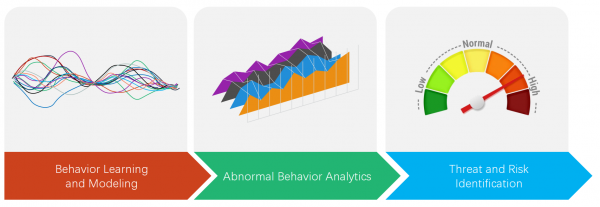
View moreHillstone Abnormal Behavior Detection
The Hillstone user behavior abnormal detection engine monitors and learns the normal behavior of server or host machines in the protected internal network. It extracts...
View moreInfowatch Traffic Monitor
Today, many companies defend themselves from viruses and external attacks, while the biggest threat comes from within. Even ordinary employees have access to company’s entire...
View moreInfoWatch Device Monitor
InfoWatch Device Monitor is a module for the protection of workstations, which monitors document printing and copying to removable media, and also ports and portable devices...
View moreNetwork Service Assurance for Service Providers
Network Service Assurance for Service Providers Drive Enterprise Digital Transformation Our Expertise and Service Provider’s Partnerships The LiveSP and LiveMSP solutions are massively used by...
View moreAchieve Operational Excellence
Achieve Operational Excellence Improve the overall efficiency and effectiveness of your Network team’s planning, deployment, upgrade, maintenance, and troubleshooting tasks. Download Operational Excellence eBook Manage...
View moreAccelerated Network Troubleshooting
Accelerated Network Troubleshooting Accelerate the identification and resolution of the most difficult network performance issues. Download Network Troubleshooting eBook PDF Complete Visibility Identify issues occurring...
View moreManaging for Network Readiness
Managing for Network Readiness Perform continuous monitoring to gain clear insight into priority updates and upgrades to optimize the network. Download the Capacity Planning Whitepaper...
View moreAdvanced Reporting And Analytics
Advanced Reporting And Analytics Generate and share a complete and comprehensive view of network performance, capacity, and utilization. Download the Advanced Network Analytics Whitepaper Pro-Active...
View moreData-Driven Change Initiatives
Data-Driven Change Initiatives Approaching any IT roll-out must be done with a proper data-driven strategy. Before implementing a significant data-driven change initiative, it’s important to...
View moreApplication Performance Optimization
Deliver a superior user experience with insights into the underlying network infrastructure, policies, and protocols that ensure the successful delivery of critical applications. Download...
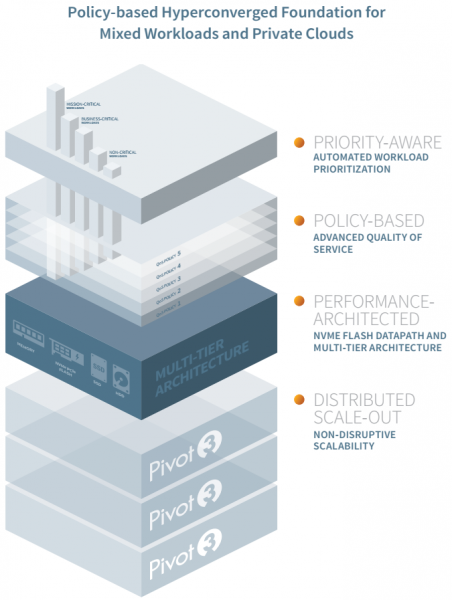
View moreDatacenter Modernization
Modernizing your datacenter with smarter infrastructure solutions from Pivot3 With data playing an increasingly central role in informing business decisions, datacenters are becoming innovation-driven profit...
View moreSAFE TRANSIT
SAFER, SMARTER MASS TRANSIT OPERATIONS WITH INTELLIGENT INFRASTRUCTURE Pivot3 consolidates video management, IoT data collection, video and data analytics and storage, access control and other...
View moreSMART CITY
SAFER CITIES THROUGH SMARTER INFRASTRUCTURE Read the Brief Pivot3 allows for the consolidation of video management, IoT data collection, video and data analytics and storage,...
View moreSMART CASINO
SAFER, SMARTER GAMING OPERATIONS AND COMPLIANCE WITH INTELLIGENT INFRASTRUCTUR Read the Brief Pivot3 consolidates video management, video and data analytics and storage, access control and...
View moreSAFE CAMPUS
A SAFER, SMARTER CAMPUS WITH INTELLIGENT INFRASTRUCTURE Read the Solution Brief Pivot3 improves security effectiveness and simplifies IT operations in complex corporate, educational or federal...
View moreSAFE AIRPORT
SAFER AIRPORT SECURITY AND OPERATIONS WITH INTELLIGENT INFRASTRUCTURE Read Solution Brief Pivot3 intelligent infrastructure supports mission-critical video surveillance, security and IT operations with maximum resilience...
View moreENTERPRISE APPLICATIONS
CONSOLIDATE YOUR ENTERPRISE APPLICATIONS PREDICTABLY WITH POLICY-BASED HCI Read Ref. Architecture Pivot3 HCI helps consolidate enterprise applications while simplifying management and slashing footprint. Its high-performance...
View moreBIG DATA ANALYTICS
HIGH-PERFORMANCE BIG DATA ANALYTICS WITH HCI Read Solution Brief Pivot3 optimizes big data analytics deployments by providing market-leading search and indexing performance while slashing infrastructure...
View moreEND-USER COMPUTING
COST-EFFECTIVE AND HIGH PERFORMANCE VIRTUAL DESKTOPS Read Solution Brief Pivot3’s HCI solutions optimize virtual desktop deployments by providing a modular policy-based platform that minimizes infrastructure...
View moreNational Institute of Standards and Technology
NIST- National Institute of Standards and Technology Virtual attacks against government systems are clearly on the rise. According to the FISMA (Federal Information Security...
View moreGeneral Data Protection Regulation
GDPR- General Data Protection Regulation GDPR (General Data Protection Regulation) has been in place since 2016 in all EU Member States and came into...
View moreHealth Insurance Portability and Accountability Act
HIPAA- Health Insurance Portability and Accountability Act The HIPAA (Health Insurance Portability and Accountability Act) was introduced in 1996 and is a set of...
View moreInternational information security management standard
ISO 27001- International information security management standard The International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC) standard 27001 is internationally recognized...
View moreEasy and agile SOX compliance for your environment
SOX- Easy and agile SOX compliance for your environment Every organization subject to Sarbanes-Oxley (SOX) compliance faces a number of challenges in achieving compliance....
View moreData theft prevention
Data theft prevention Protect your company against critical data theft. Data breaches cost millions to businesses, and the trend is for those amounts to increase...
View moreSession Management
Session Management (PSM) Access to your company’s servers without revealing the password. What it is Recording and storage of all remote sessions performed through the...
View moreTask Management
Task Management Secured privileged task management. What it is User action management on devices, allowing a user to execute a specific task without the need...
View moreScan Discovery
Scan Discovery Discover privileged credentials automatically. What it is The Scan Discovery feature surveys the environment and enables automated registration of devices and their respective...
View moreScan Discovery
Privileged Information Protection Protect your business’ critical and sensitive information. What it is Storage of personal information, such as personal passwords and digital certificates. Benefits...
View moreThreat Analysis
Threat Analysis- Automatic analysis of crucial actions. What it is A solution dedicated to environment monitoring in order to detect and send real-time alerts of...
View moreBehavior Analysis
Behavior Analysis Monitor user behavior automatically. What it is Even when privileged access is inherent to the user’s role, some critical stages in access management...
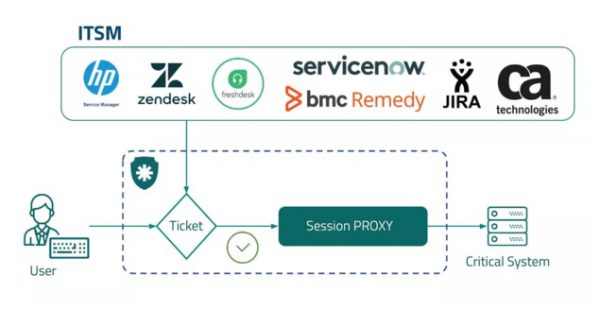
View moreITSM Integration
ITSM Integration Avoid unauthorized changes. What it is The senhasegura platform integrates the main IT Service Management (ITSM) solutions to ensure that only changes that...
View morePAM Crypto Virtual Appliance
PAM Crypto Virtual Appliance The solution for virtualized environments For clients who have virtualization infrastructure and wish to choose the architecture plan, senhasegura has the Virtual...
View morePAM Crypto Appliance
PAM Crypto Appliance Advanced hardware technology developed for your company. For companies that want a higher level of security, guaranteed performance, and a centralized software...
View moreHigh availability and contingency
High availability and contingency Eliminate failures that impact your IT environment and cause losses. https://youtu.be/eJp2Nf3muOs Senhasegura has been designed to allow its operation in an...
View moreSenhasegura Security
Senhasegura Security Full protection assured for all types of threats. To ensure optimal protection of stored passwords, senhasegura offers several security mechanisms, both at the...
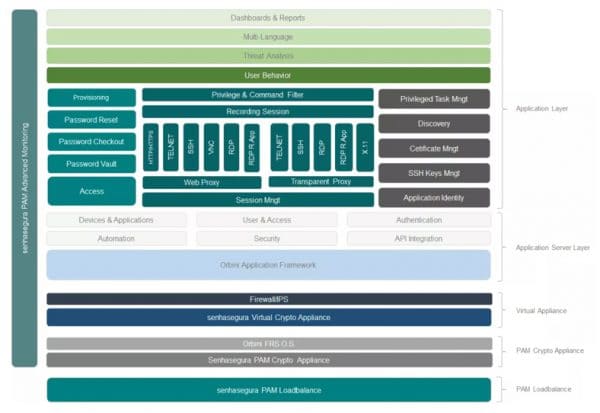
View moreProduct Architecture
Product Architecture The senhasegura architecture offers the highest technology available. Senhasegura product architecture consists of a set of integrated component layers that support senhasegura functioning,...
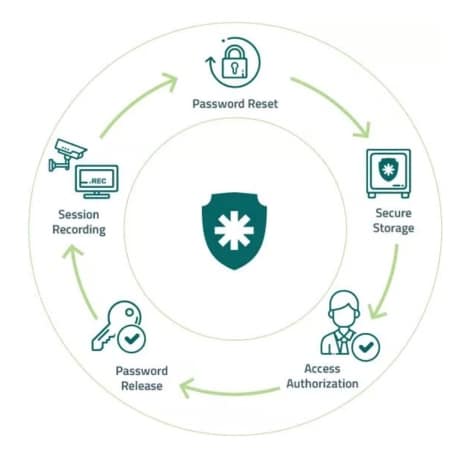
View moreHow it works
How it works Senhasegura securely centralizes all of your credentials Exposure and misuse of privileged accounts are extremely inviting to cyberattacks. In recent attacks on...
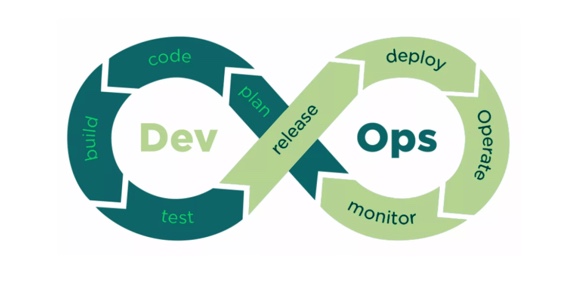
View moreDevOps and Secret Management
DevOps and Secret Management Senhasegura is fully compliant with DevOps environments. Currently, the software delivery pipeline is focused on delivering high quality products and services...
View morePayment Card Industry – Data Security Standard
Payment Card Industry – Data Security Standard. A favorite target of hackers is companies that accept credit card payments and keep their customers’ sensitive data....
View more7 signs that your company needs to improve the security of sensitive data
7 signs that your company needs to improve the security of sensitive data Undoubtedly, we are in the moment where the most precious asset...
View moreProtect Your Password
Protect Your Password 8 Tips to Protect Your Password We are already in the month of May, and you know what we celebrate on the...
View moreZero Standing Privileges
Zero Standing Privileges With the growth of cyberattacks, access credentials have become a strong attack vector. In 74% of cases of data breaches, companies...
View moreAudit- Senhasegura Solution
Audit- Senhasegura Solution Check if you business is in compliance with standards and regulations. Audit- Senhasegura Solution Improper access to privileged accounts is a...
View morePrivilege Abuse
Privilege Abuse Control the misuse of privileges in your company. In most IT environments, the least privilege principle is not valid. There are many...
View more