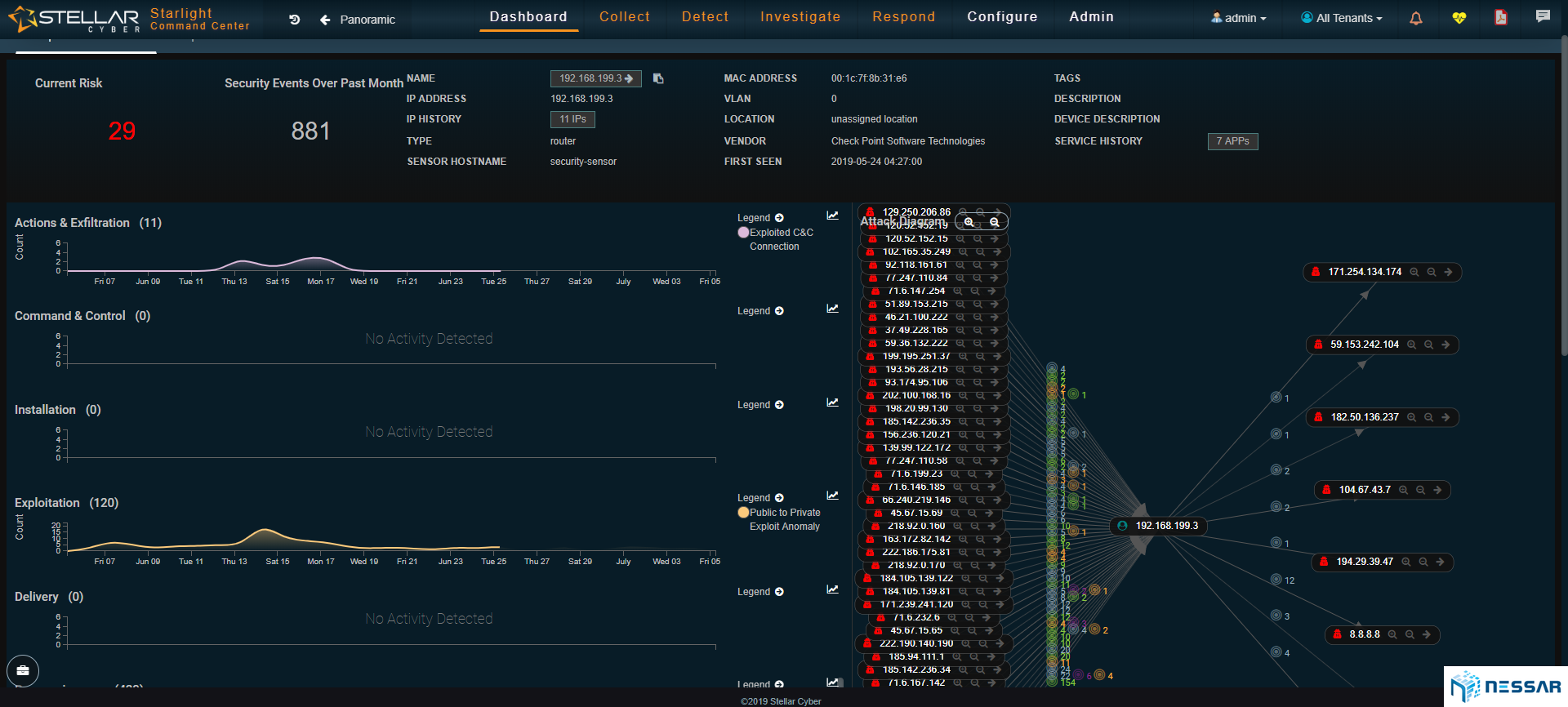
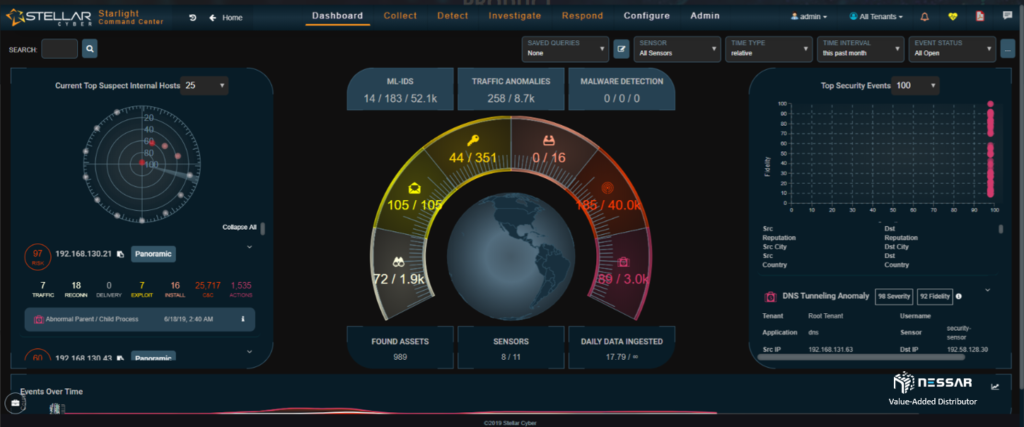
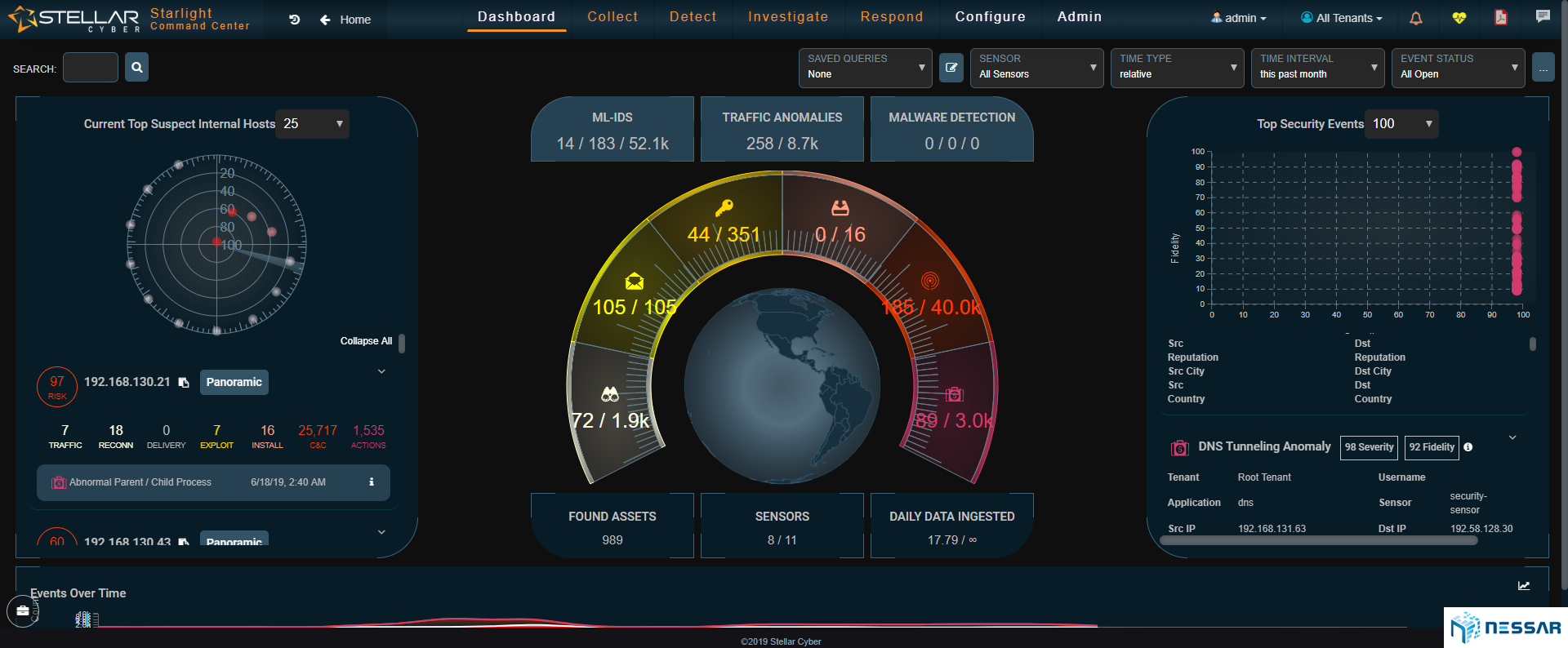
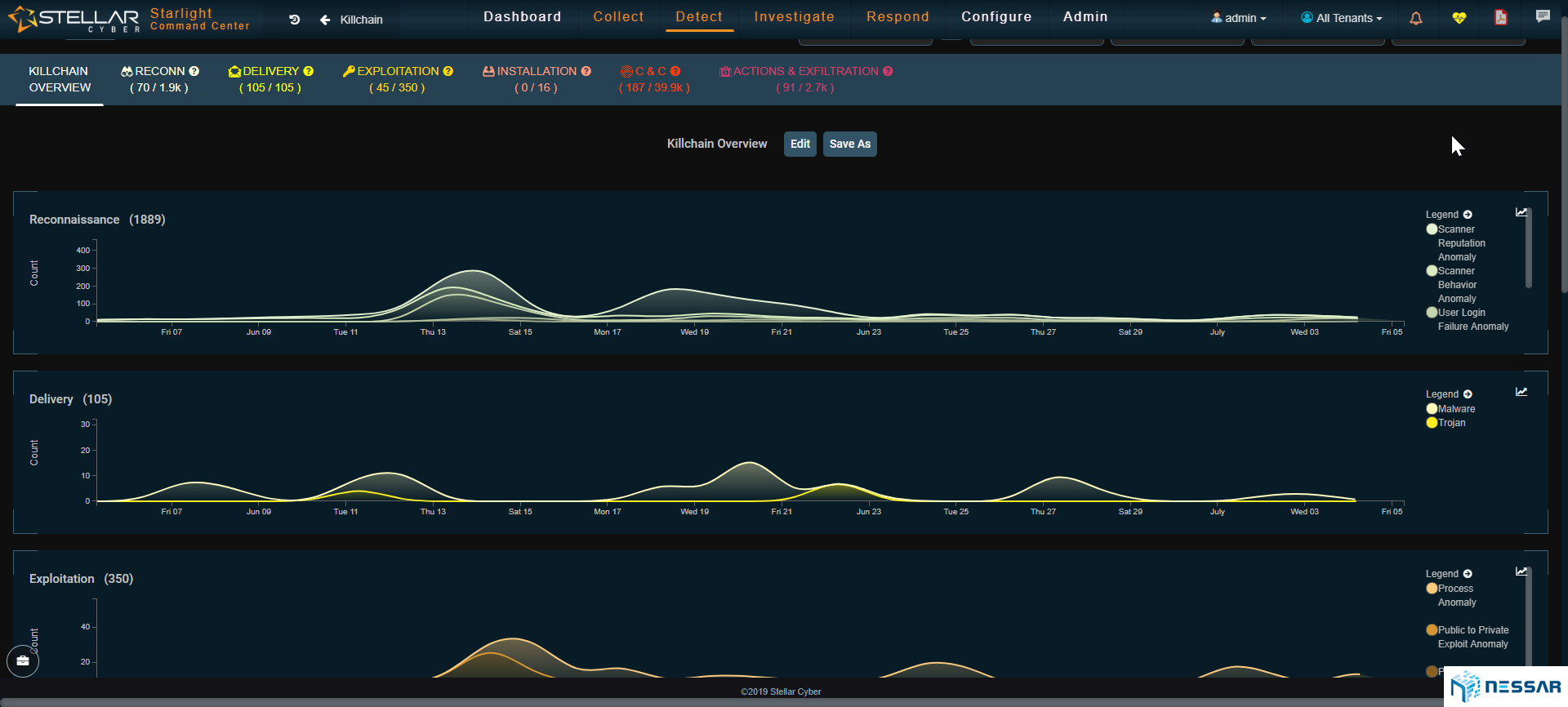
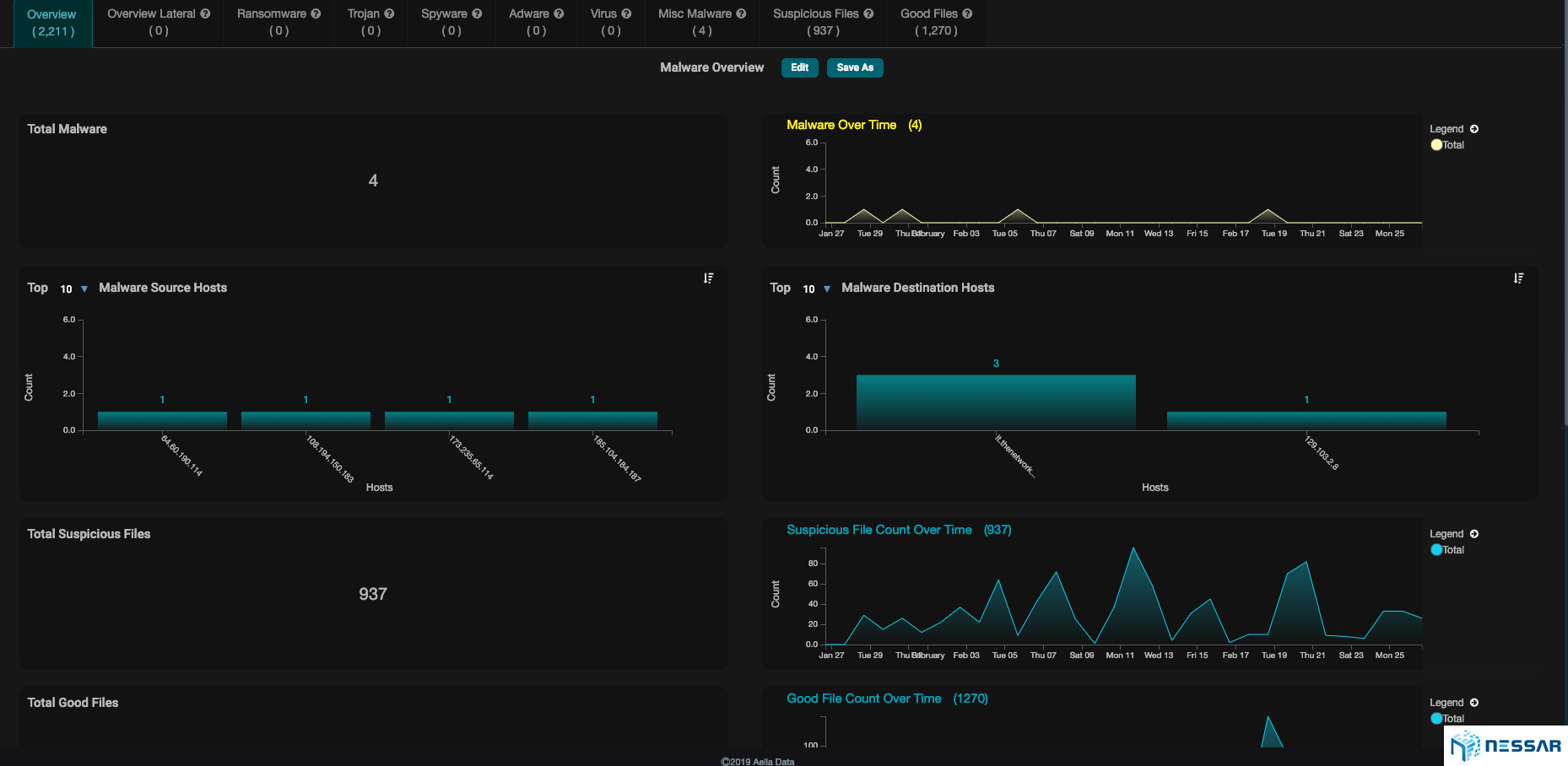
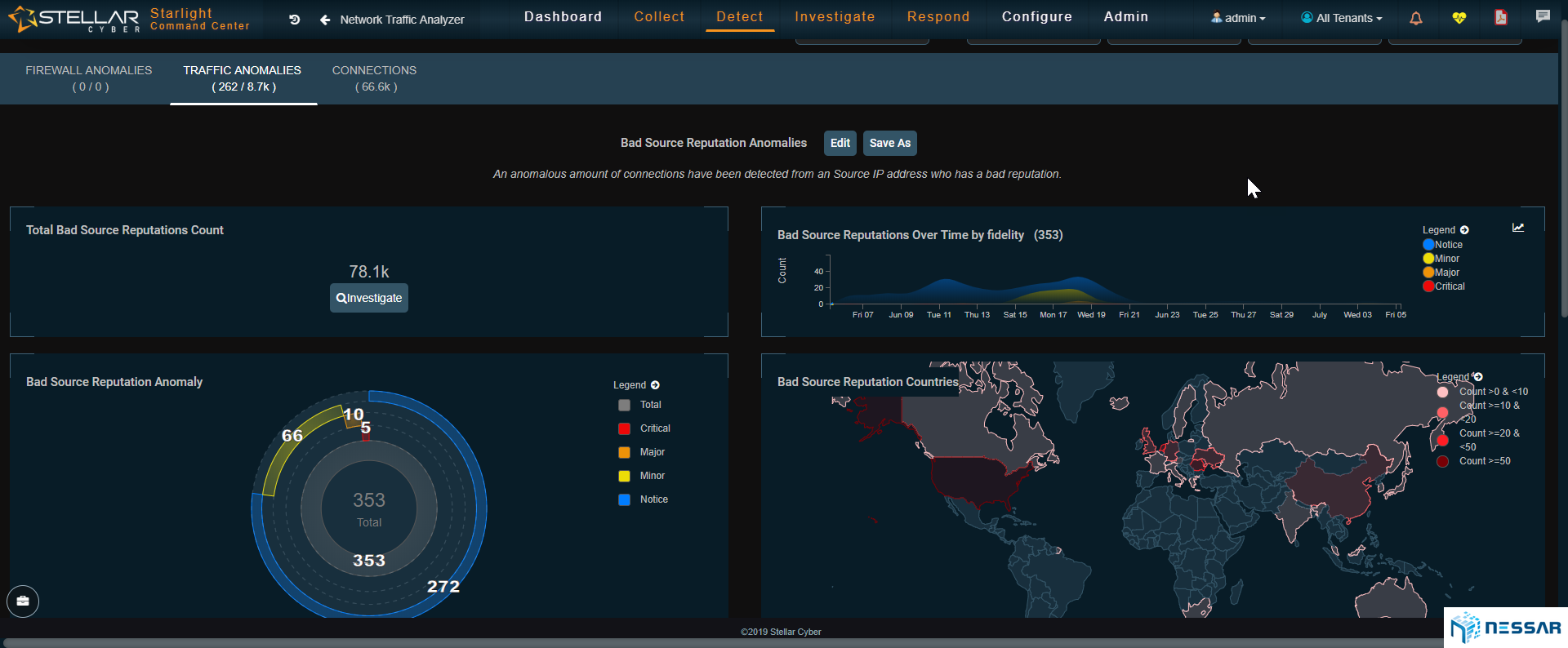
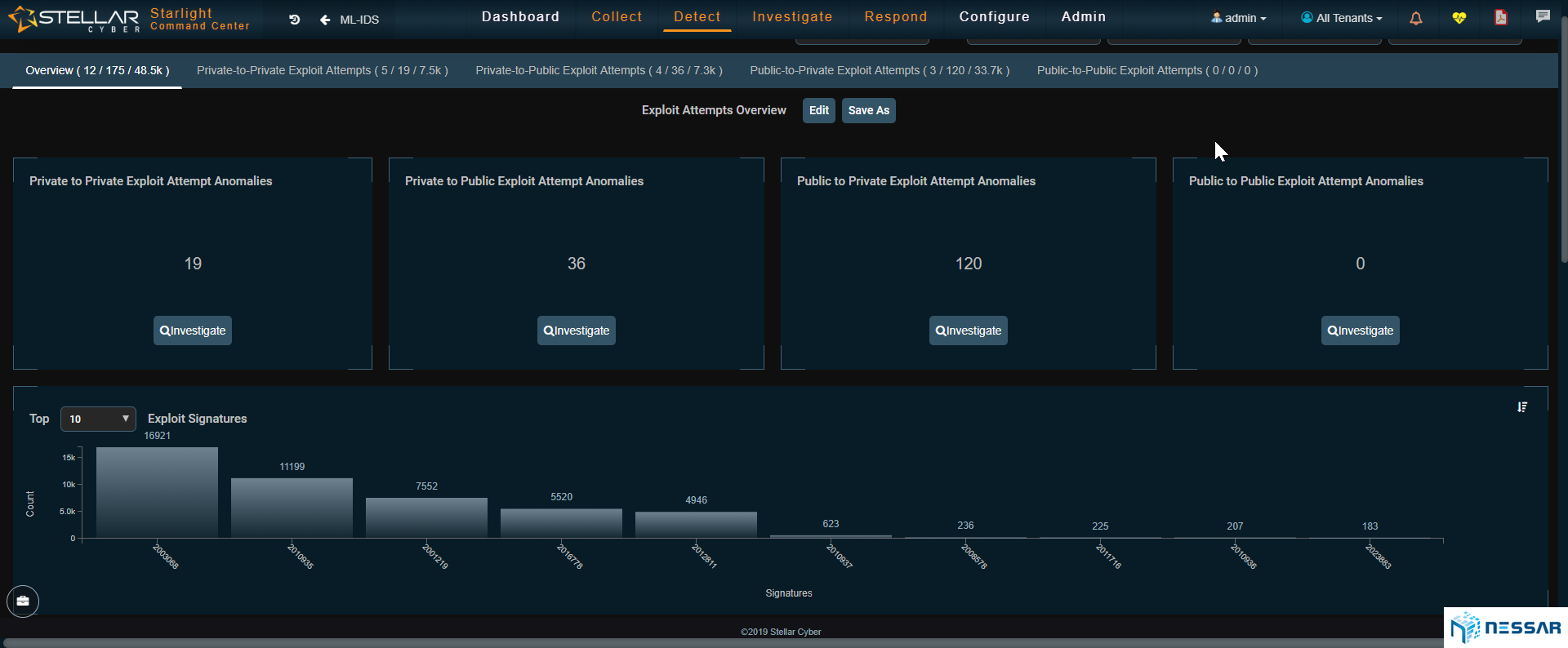
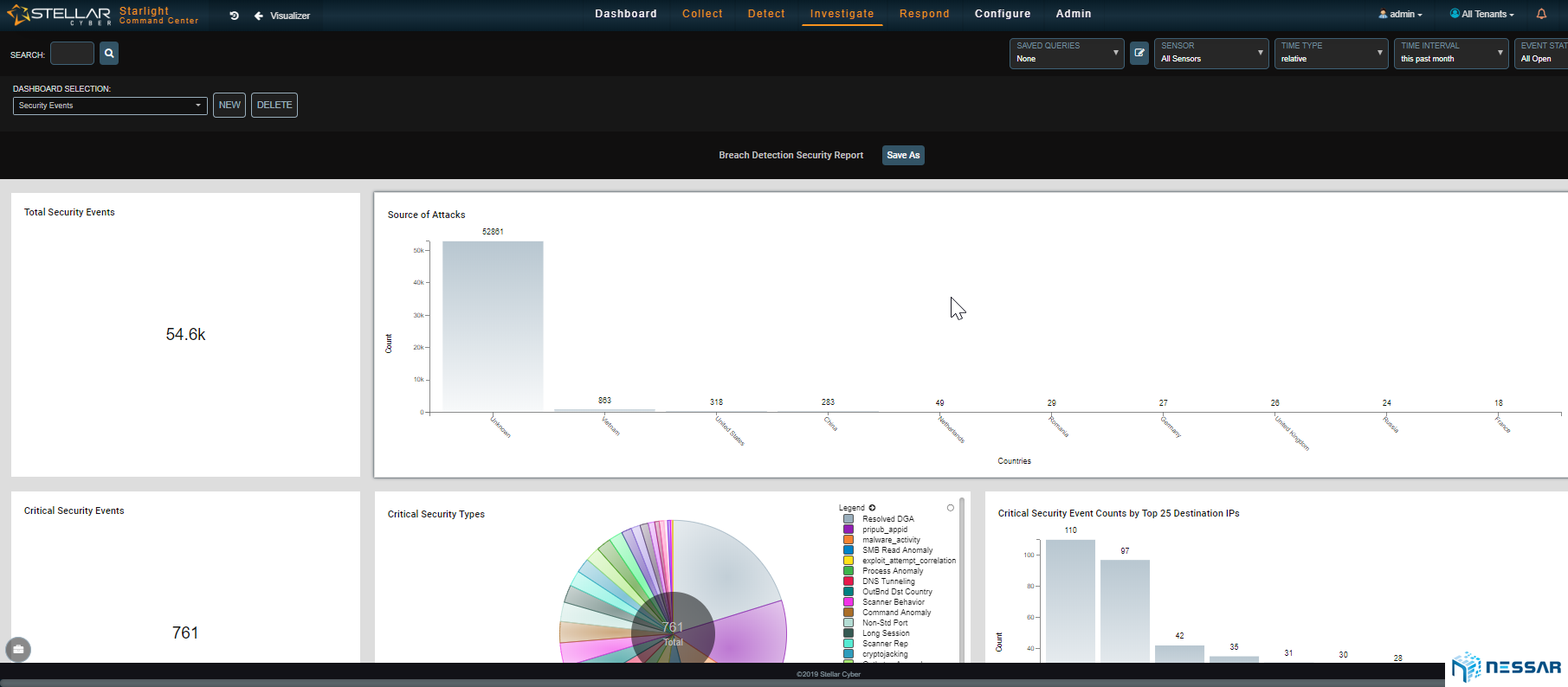
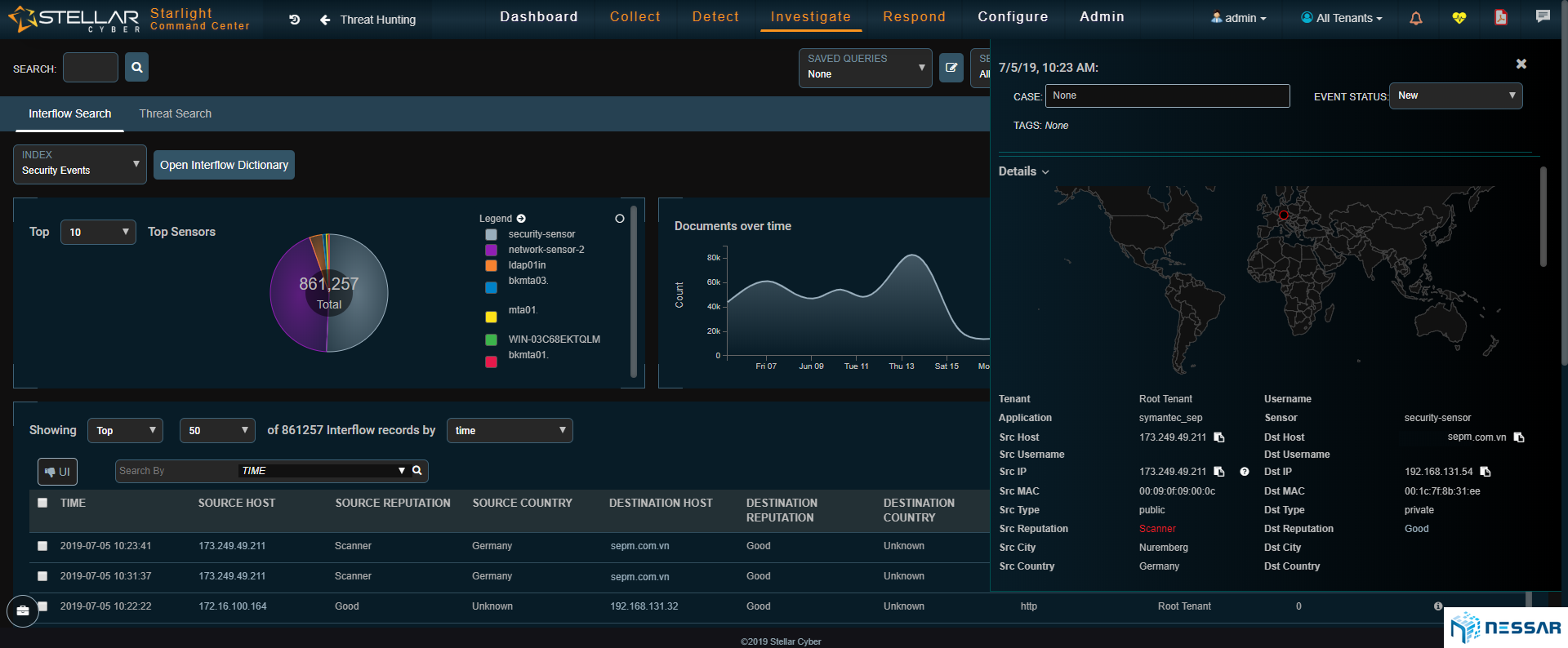
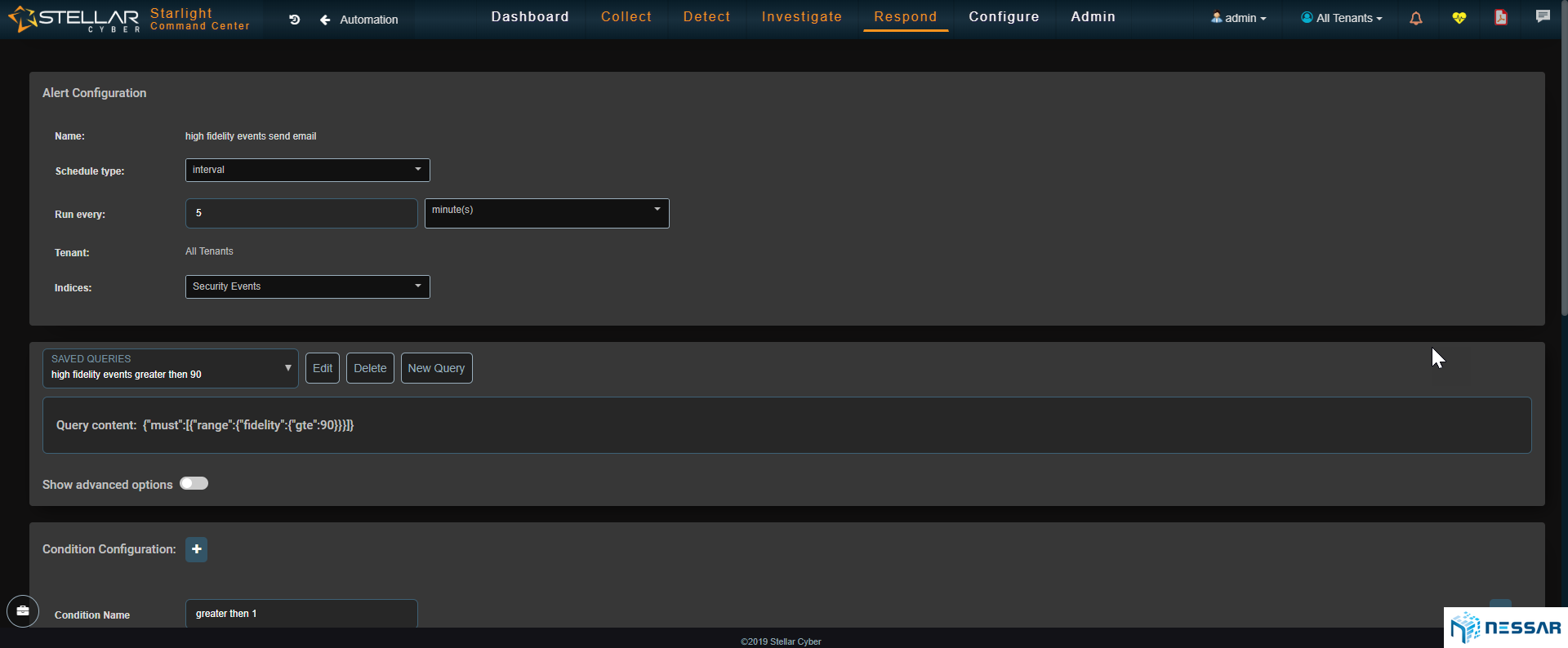
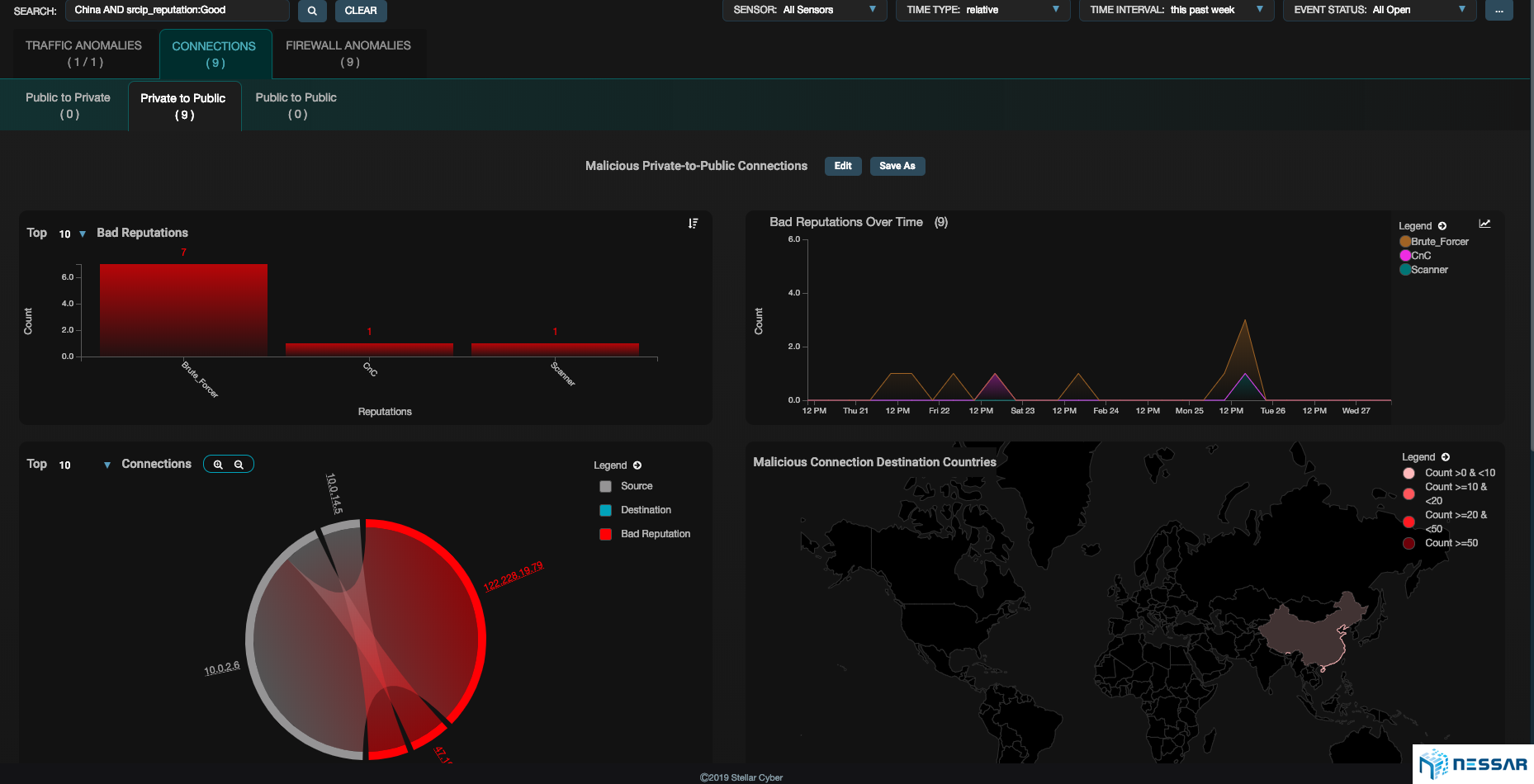
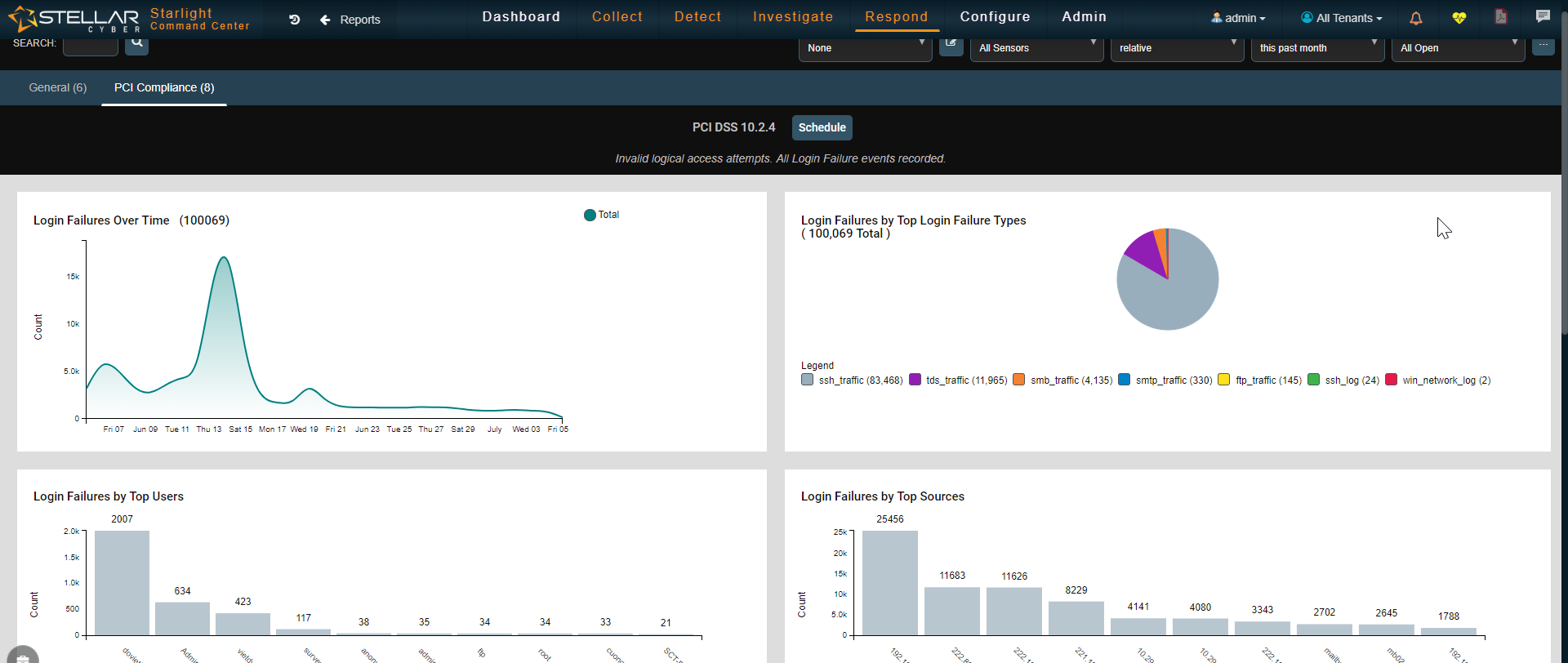
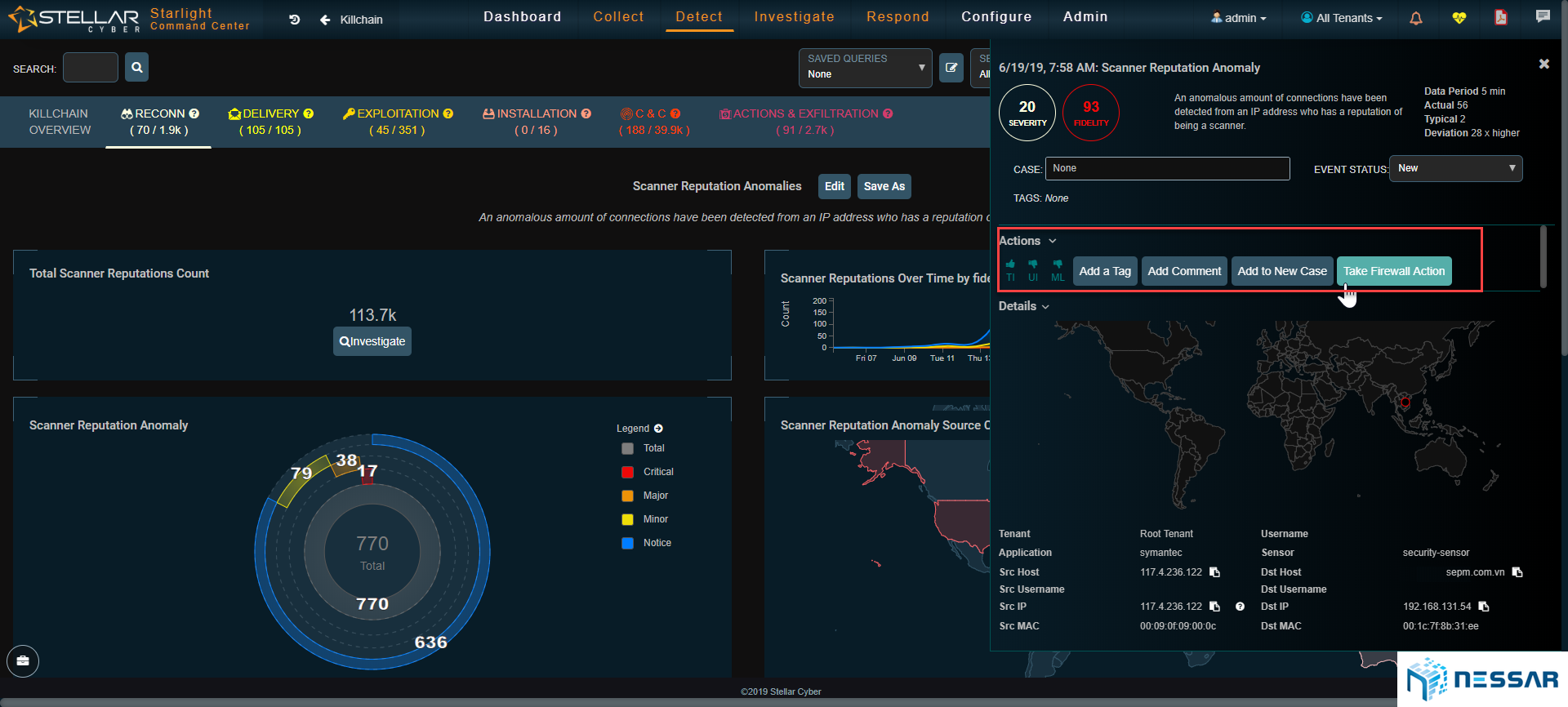
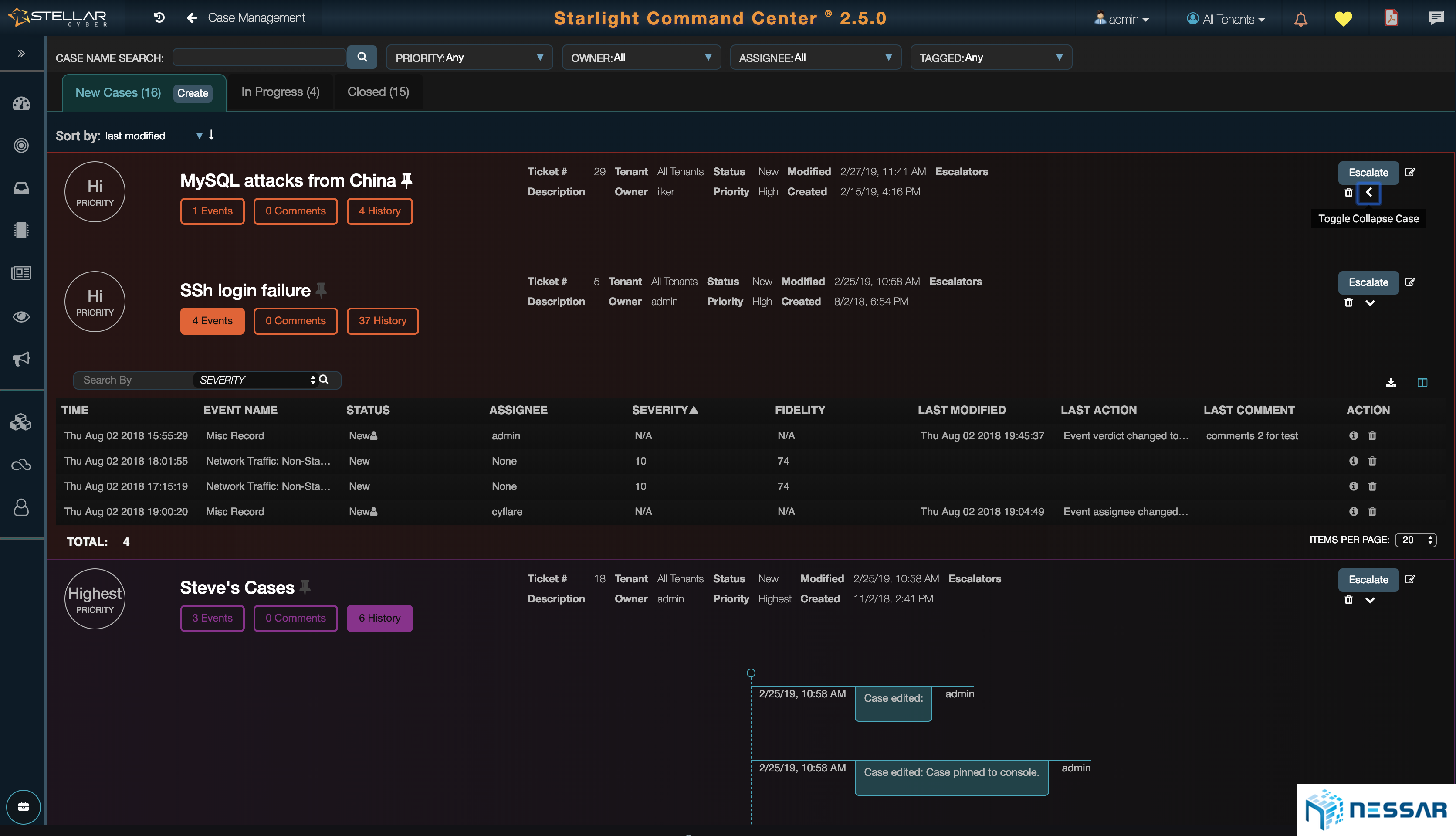
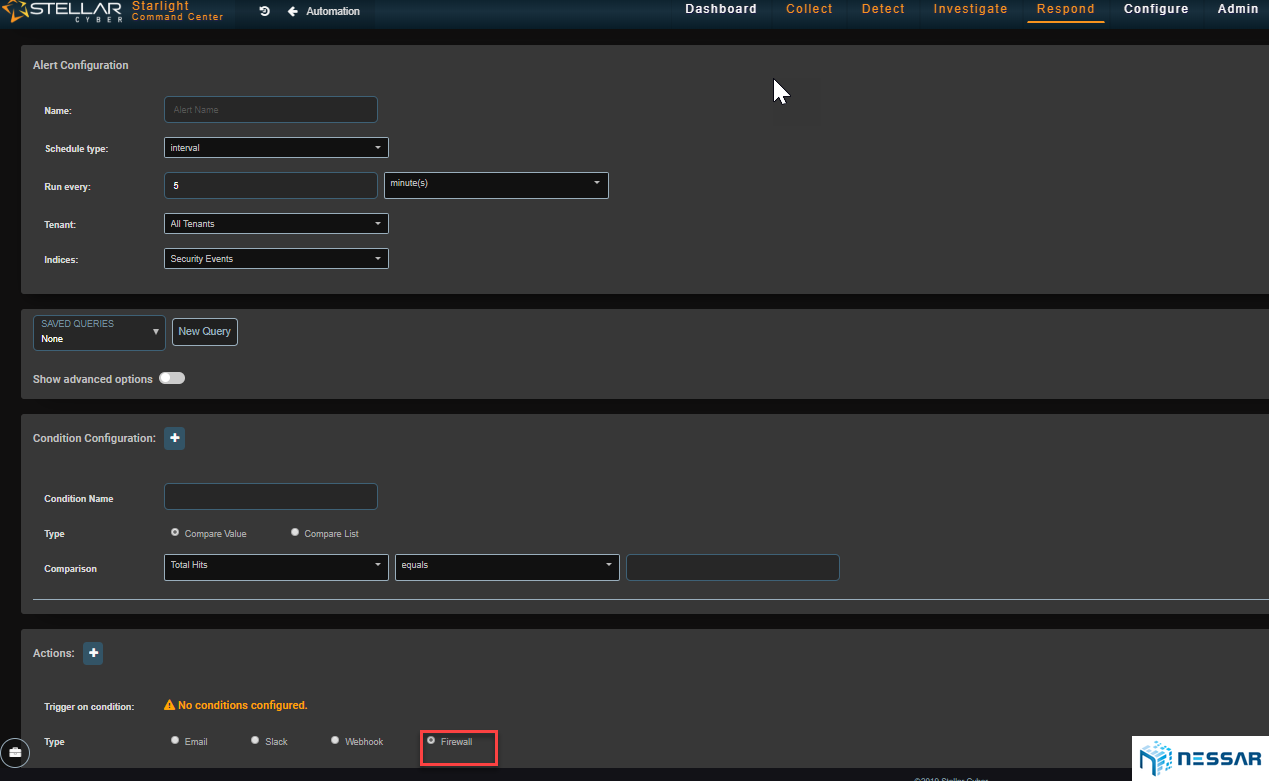
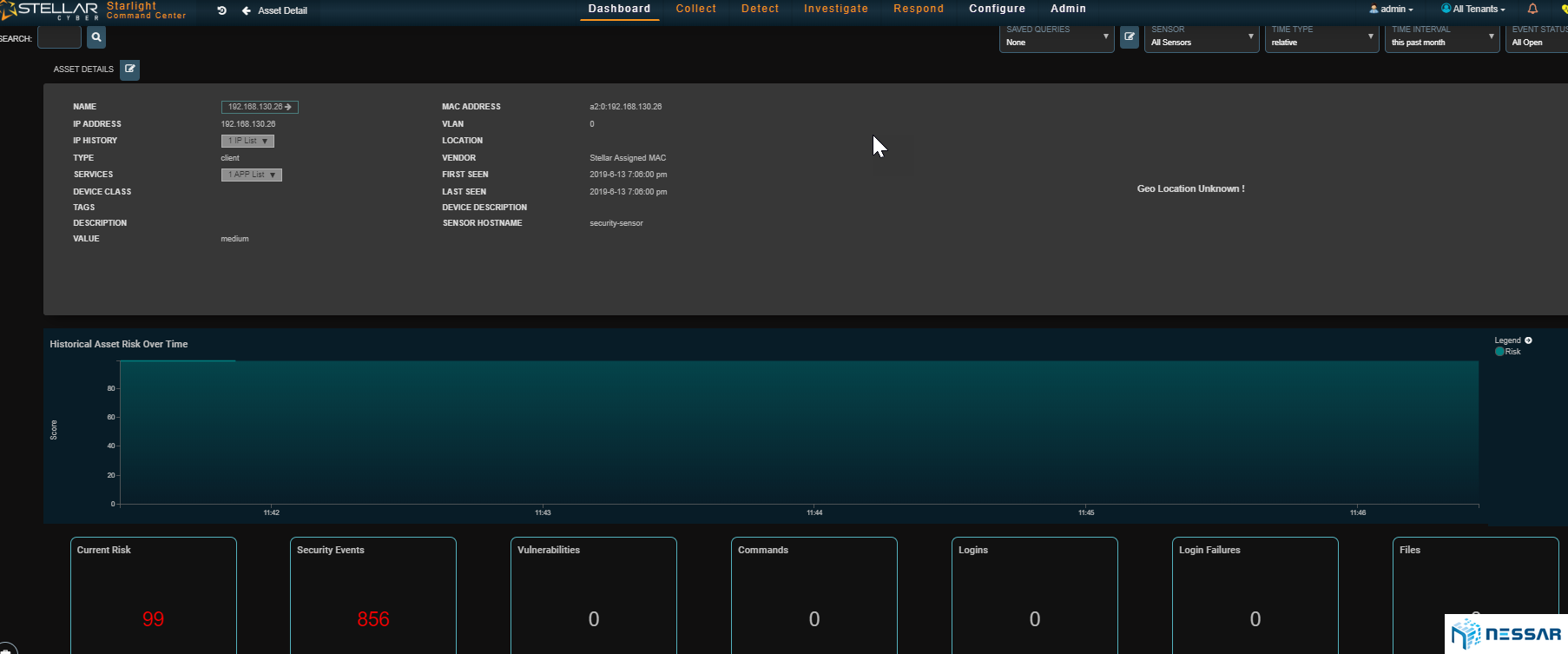
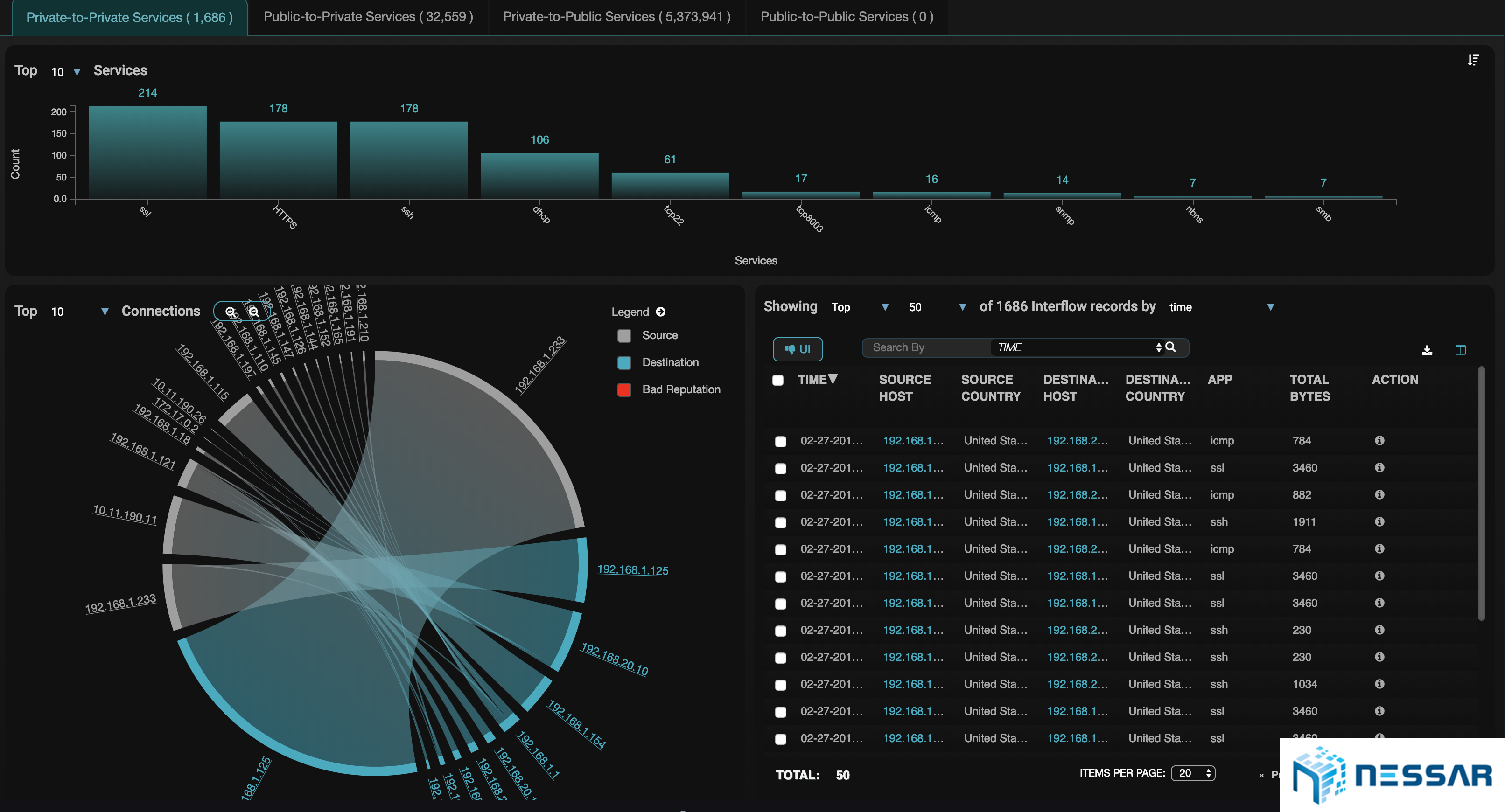
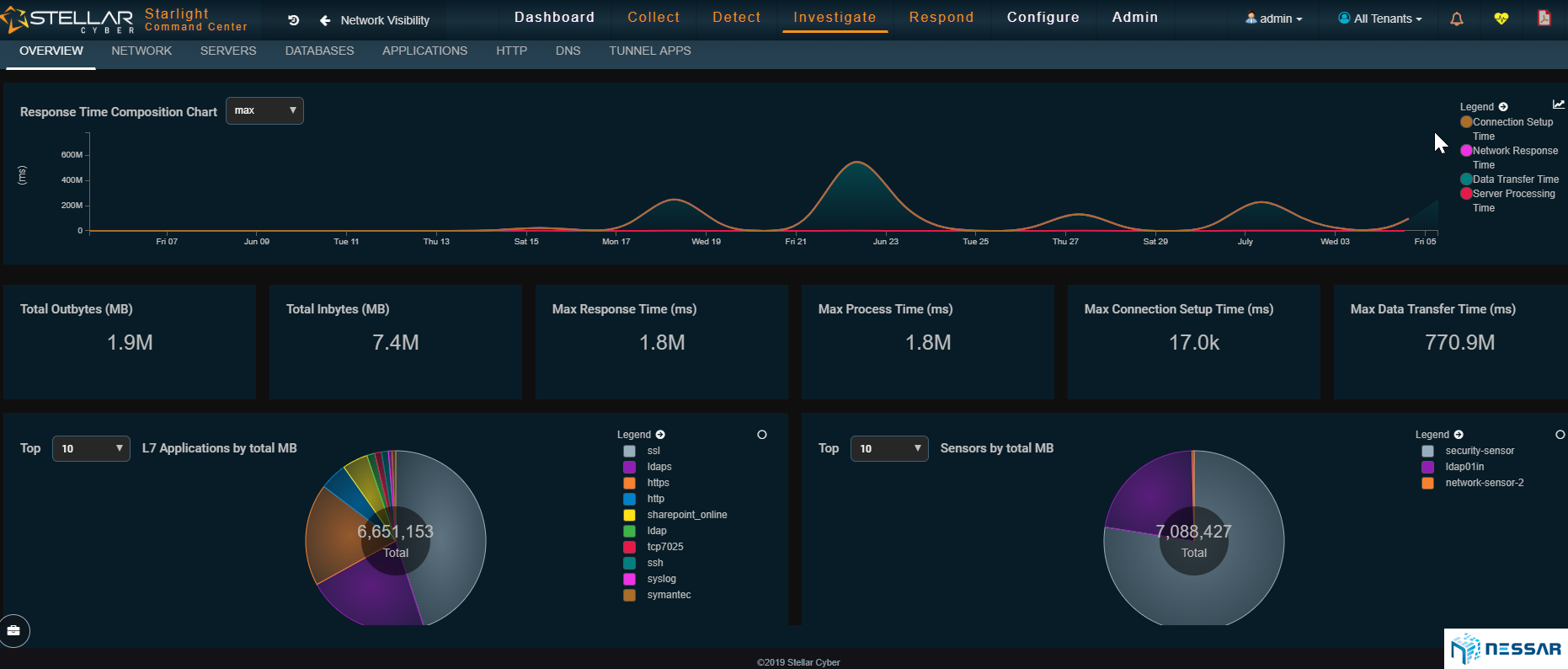
Admins can easily trace the attacks that have taken place on an asset and identify which bad actors have contributed to the compromise. Starlight also gives admins the ability to locate where bad actors are coming from. With the single click of a button an admin can drill down to see the details of security events and determine the reason of behind an event.
Starlight is the most open and easy to understand, so use, security analytics platform in the world with huge difference…